A Detailed Orientation To SaaS Application and its Security Aspect
With the enormous utilization of the internet and business goals to save additional expenses, SaaS applications are coming to light. Such applications are now running in every organization, handling extensive confidential information.
Therefore, it makes firms focus more on understanding SaaS application security. So, we have curated the most prominent SaaS app security aspects, covering the primary user’s perspective from each end.
Let’s have a look at it.
A Brief Introduction to SaaS Application and its Usage
SaaS or Software as a Service is an advanced cloud-based mechanism that leverages end-users to utilize applications without installation. More straightforwardly, it aids the stakeholders in accessing the apps through browsers and performing operations as they are running on their own devices.
Such applications can fulfill each of your requirements, even if you are low on budget. You only require a system, a browser, and an internet connection to use the SaaS applications.
Moreover, you don’t have to worry about upgrades, as the cloud vendor will do it automatically. You will have the interface of your application on your screen, and server operations will get automatically executed.
Furthermore, the following are some primary reasons and utilization of SaaS applications:
- It streamlines the administrative task of providing a standard application to large users.
- It helps you save money, as you pay only for the resources getting utilized.
- When any new code gets deployed, it gets reflected at each user’s end.
- SaaS infrastructure leads to running highly power-consuming apps on an average system.
Real-Life Significant SaaS Application Examples
Daily, we all utilize some SaaS applications, among which the most common are Gmail and Microsoft Outlook. When you access these apps through a web browser, it runs on the servers of the respective publisher.
Let’s look at the bigger picture, how organizations benefit from SaaS.
Suppose you are a system administrator in an organization with hundreds of employees. And you get a task to connect everyone through Microsoft Outlook.
So, in this case, you get two choices. First, install Outlook on every computer system, which can take weeks or months. Second, to set up Outlook for everyone on a SaaS cloud within a minimal time.
It’s clear that you will select the second option, as it will aid you in saving time. In addition, you will get the same functionalities of the app installed on a system.
And you don’t have to upgrade the software or hardware of any computer, as Outlook will be running through the browser, utilizing cloud server resources.
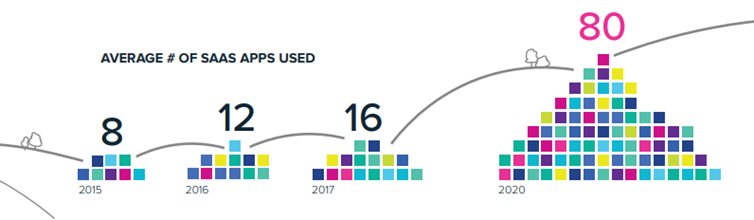
Further, as per BetterCloud, 80% of the applications used in an organization are SaaS-based. And, the statistics will grow by 5-10% more by 2025.
SaaS Architecture and its Working Scenario
IaaS, PaaS, and SaaS are the three primary infrastructures in cloud computing. And SaaS gets the highest preference by companies, as the vendor covers server and security maintenance. You only have to configure your applications and provide access, and your users will start operating on them.
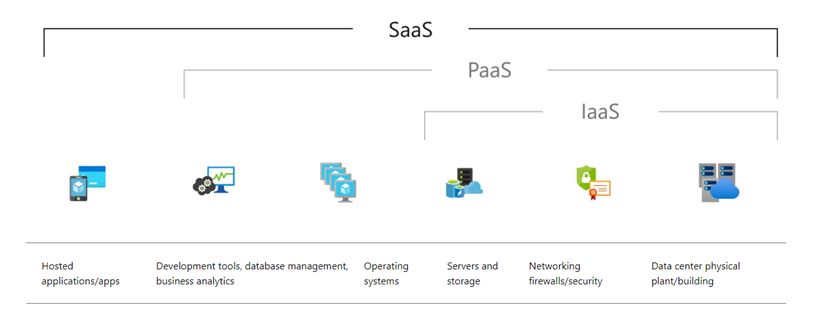
Moreover, SaaS also provides built-in tools for performing administrative tasks. You can monitor the performance, assign new resources, and manage databases, operating systems, and networking functionalities.
And the main benefit is that you don’t need to set up any additional hardware to execute all such operations. An internet connection and a system are all you need.
Understanding the Benefits of Software as a Service Applications
Highly Affordable
SaaS infrastructure lets you minimize your server costs to the lowest. Cloud vendors offer different types of deals, such as pay-as-per-use. Under such an agreement, you only have to pay for the resources getting utilized.
Recommended: Top SaaS Security Risks & How to Prevent Them?
For instance, if the cloud provider is charging $50/month for 100 GB of storage space. Then you will only pay $50 once you cross the defined limit.
And when you utilize more storage space, you only have to pay more. Therefore, cost directly relies on usage.
Platform and Device Compatibility
You don’t require any particular operating system for accessing and operating SaaS applications. A constant internet connection and a web browser are the primary requisites. Whether you are a software publisher or an end-user, it benefits both.
Organizations can directly upload the code over the cloud, leveraging users to use their software. And stakeholders benefit from accessing software without performing any additional configuration. As a result, user experience improves, and productivity gets increases.
Improves Inter-Department Operations
As SaaS applications are always connected to the internet, sharing and updating data in real-time is easy. Most firms use a SaaS Enterprise Resource Management system, connecting each department through a centralized cloud server. It helps the departments to view live data flow and move further accordingly.
Moreover, it helps to organize the tasks to run the agile sprints effectively and seamlessly. And, if the company adds a new feature for a particular or entire staff, it gets updated directly from the backend.
Anywhere Anytime Access
One of the main benefits of SaaS applications is around-the-clock access. Whether working from the office or remotely, you can always access the application and execute your operations. In addition, the SaaS services are available 24/7 in every region, enabling you to schedule work accordingly.
It removes the roadblocks and helps you create a smooth workflow to achieve targets on time. The staff member has to login into the portal through the browser, and appropriate resources will get available.
High-end Security
Cloud vendors follow all the NIST and ISO guidelines to maintain data integrity, confidentiality, and availability. Cloud providers configure the latest mechanisms for their protection, whether it’s security for hardware components or the software running on the server.
Furthermore, you get the leverage to set up additional access, authentication, and authorization control for better security. Besides, cloud vendors maintain the physical security and performance of servers under the same subscription.
Prominent Data Storage and Backup
When you operate SaaS applications, it utilizes the processing power of cloud servers rather than your system resources. Although cloud vendors have a mammoth storage facility, you can handle the increase in storage demand. SaaS gives you the leverage to scale up resources within minutes for efficient business execution.
In addition, it also offers automatic data backup and restoration, never letting you lose any data. Also, if you face any cyber-attack, it will aid you in restoring your data and continuing business operations.
Listing Up the Primary Security Implications for SaaS Applications
SaaS applications offer numerous benefits, empowering business processes. However, there can be some conditions that can heighten the risk of facing a cyber-attack.
Misconfiguration
Misconfigurations are not common in any SaaS infrastructure, as cloud providers cross-verify the server setups. However, there can be a slight probability of misconfiguration due to human error. In addition, if you make any mistake during the setup, it can also work as a loophole for the attacker.
Therefore, the cloud vendor and the user can be responsible for the attack through misconfiguration. For instance, if you provide administrative controls to a low-level staff member, it will be a misconfiguration from your end.
Non-Compliance with Industry Standards
In every sector, you will find some regulatory organizations, which define some standards for seamless operations. And same is the case with SaaS application developers and cloud vendors. Both must follow NIST, ISO, and other mandatory government protocols to ensure data and system security.
If anyone among both is not able to meet the requirements, it lacks achieving the utmost security. As a result, attackers find the system vulnerable and execute cyber-attacks. Moreover, legal actions also get imposed if the SaaS app is not up to the standards.
Outdated Access Controls
When you configure a SaaS application, setting up its access controls is crucial. Any loophole in access control can open doors for a malicious actor to enter the organizational network. However, if your application has an outdated access control system, hackers are highly likely to crack it quickly.
Furthermore, your administration and other backend accounts will also be at risk with such a system. And your data will have a higher probability of getting modified unauthorizedly.
Data Processing in Original Format
Nowadays, hackers utilize numerous strategies to understand the type of data processed by the application. However, if they found something meaningful, they try to breach it. And processing your data in its original format is the primary vulnerability, attracting data breaches.
In addition, even a SQL injection attack can lead you to face heavy loss if you store and transfer data in the original format. It’s not only limited to the user data; even the application’s source code available in its first form is an attraction for crackers.
Lack of Hardware Controls
Maintaining hardware is the cloud vendor’s responsibility. Although, you must check about the services offered by the provider before finalizing it. It is essential to configure physical locks to protect servers from unauthorized access.
Furthermore, if you have a dedicated system running the administrator’s account, you must protect it using hardware controls. Otherwise, a third person can access it illegally and modify the application.
Mechanisms to Strengthen the SaaS App Security
Regular Audits and Updates
To consistently comply with the latest standards and regulations, you should perform frequent audits. This practice is essential for both the cloud service provider and the user. It will help to discover the vulnerabilities in the system and patch them as soon as possible.
In addition, you will get to understand your system thoroughly and update it accurately to meet business goals. And you will also analyze an increase in performance, quality, and security.
Usage of Code Signing Certificate
Utilizing Code Signing Certificate will help you protect the application code from illegitimate modification. It will convert the overall code into an unreadable format by performing hashing and encryption. As a result, if attackers try to read and modify source code, they will not be able to read it.
Moreover, Code Signing Certificate will also enhance your business reputation. Whenever any end-user runs your application, its system will not show any warning message. Hence, your users will have a secure and seamless experience.
Selecting the Best Code Signing Certificate: Comodo EV Code Signing Certificate or Sectigo EV Code Signing Certificate
Extended Validation Code Signing Certificate is a perfect choice for publishers providing a SaaS application. It gives the top-most level of security and fulfills the requirement of aligning with all industry regulations. Moreover, it offers instant legitimacy recognition across platforms.
And if you are looking to buy an EV Code Signing Certificate, then Comodo EV Code Signing Certificate and Sectigo EV Code Signing Certificate are the most recognized brands. You can trust both, as they offer advanced encryption and an additional security layer with a hardware token, tamper-proofing the app.
Overall Data Encryption
Securing user and other confidential data is as essential as encrypting the source code. So, you always configure the latest hashing, salting, and encryption algorithms over data in databases and transactions.
It will help you maintain data integrity, and even a SQL injection gets successfully executed. It will prevent the attacker from reading information and performing any further action.
Additionally, you should always verify the encryption standards cloud vendors use to process your data securely.
Two-Factor Authentication
You must always focus on authentication security whenever you set up any SaaS application. It will help you authorize only legitimate users to access the software and utilize resources.
And always try to configure a two-factor authentication mechanism. With its help, all your users will be a step ahead of getting affected by spoofing and account takeover attacks.
Concluding Up
SaaS applications are in trend, utilized by more than 70% of organizations. It aids the firms in saving server maintenance and upscaling cost, as the cloud provider provides all such services. However, in some aspects, application security comes under the provider and the user. Hence, both have to maintain it on their end.
Furthermore, the most significant way to secure a SaaS app is to encrypt its code and data to ensure integrity. And frequently auditing to find loopholes and patch them. SaaS applications are one of the finest ways to enhance productivity, but ensure you focus on all its security aspects.

