What is FIPS? Detailed Guide on FIPS 140-2

What is Federal Information Processing Standard (FIPS)?
The Federal Information Processing Standard (FIPS) is a collection of rules published by the National Institute of Standards and Technology (NIST) that outlines how to store and handle sensitive data securely. It is a fundamental security precaution that all companies must use to protect Personally Identifiable Information (PII).
FIPS defines best practices for data encryption, authentication, and access control. Enterprises must implement precise technological and administrative safeguards to protect their data from unauthorized access.

It also describes the procedures for dealing with security issues like data breaches. Finally, FIPS contributes to the protection of sensitive data at all stages of its life.
Adopting the FIPS standard can be challenging, requiring enterprises to have a thorough grasp of their data and the policies that govern it. Organizations must create an all-encompassing security plan that outlines all security actions.
Furthermore, organizations must assess their data regularly and ensure the associated controls comply with the standards.
FIPS is an integral component of any security architecture for protecting sensitive data. Organizations may ensure they apply the appropriate security steps to secure their data by following the criteria outlined in FIPS.
What is FIPS 140-2?

FIPS 140-2 is a standard for evaluating the efficacy of cryptographic devices. It is the industry standard for securing digital data and maintaining communication system integrity. Before being certified as compliant, cryptographic modules must fulfill stringent performance, security, and availability standards.
FIPS 140-2 is the most frequently used security standard, which most governments and businesses worldwide need. If a product has a FIPS 140-2 certificate, it has been evaluated and formally verified by the United States and Canadian governments.
This certification is significant because it ensures that product cryptographic modules have been verified for efficacy and any flaws that hostile actors may exploit.
Companies must use FIPS 140-2 certified solutions to secure the confidentiality, integrity, and availability of their data, communications, and transactions.
What are FIPS 140-2 levels?
The Federal Information Processing Standard (FIPS) is a collection of federal standards designed to protect electronic data. It provides a complete set of security procedures and principles to be followed while creating, storing, and processing sensitive data.
FIPS pertains to encryption and authentication systems at all levels, from software implementations to hardware devices.
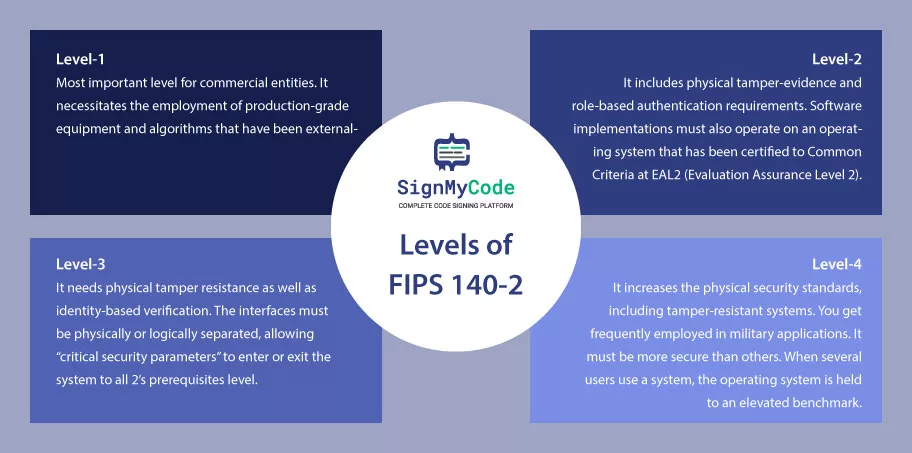
FIPS Level 1:
This is the most important level for commercial entities. It necessitates the employment of production-grade equipment and algorithms that have been externally evaluated. Government organizations, on the other hand, are expected to conform to Level 2 and higher.
FIPS Level 2:
It includes physical tamper-evidence and role-based authentication requirements. Software implementations must also operate on an operating system that has been certified to Common Criteria at EAL2 (Evaluation Assurance Level 2).
FIPS Level 3:
Now, coming to what is FIPS 140-2 Level 3, it needs physical tamper resistance as well as identity-based verification. Furthermore, the interfaces must be physically or logically separated, allowing “critical security parameters” to enter or exit the system to all 2’s prerequisites level.
FIPS Level 4:
This level increases the physical security standards, including tamper-resistant systems. You get frequently employed in military applications. Although the requirements are kind of similar to Level 2, any detected attacks in the environment erase the text to conceal the information.
Another emphasis of FIPS 140-2 level 4 is upon the cryptography module’s operating systems. It must be more secure than in previous levels. When several users use a system, the operating system is held to an elevated benchmark.
Understanding FIPS standards is critical for creating secure systems. It guarantees that all sensitive data is handled appropriately and safely.
Recommended: FIPS 140-2: Validation VS Compliance
FIPS 140-2 Compliant List
FIPS compliant list is a comprehensive checklist of cryptographic modules that have been tested and certified to meet the requirements of the Federal Information Processing Standard (FIPS) 140-2.
The list is used by various organizations, government agencies, and businesses to identify and validate secure cryptographic modules.
FIPS 140-2 is a U.S. government standard that defines security requirements for cryptographic modules protecting sensitive information. This security standards that are used by agencies within the U.S. federal government to protect sensitive data.
These compliant algorithms have become a critical security standard for many organizations, especially the federal government. The main organizations required to be FIPS 140-2 compliant are federal government organizations that collect, share, disseminate, transfer, or store sensitive data, like Personally Identifiable Information (PII).
All federal agencies, including their contractors and service providers, must also comply with FIPS. Additionally, any systems deployed in a federal environment must also be FIPS 140-2 compliant.
This includes encryption systems that Cloud Service Providers (CSPs) use. It counts software, computer solutions, and other technologies that store, transmit, or manage sensitive data.
Important: One of the reasons why so many technology businesses want to ensure they are FIPS 140-2 compliant is because FIPS-compliant products can even be evaluated for use by the federal government.
This essential security standard that organizations must comply with to protect sensitive information. Organizations must ensure that all encryption technologies that protect sensitive data meet FIPS 140-2 standards.
Furthermore, organizations must audit their systems regularly to ensure they yield with FIPS 140-2 standards. Adherence to these security standards helps organizations ensure the security of their systems, data, and sensitive information.
Why is FIPS Compliance Used All Over the World?
FIPS compliance is crucial for enterprises to ensure their security is current, up to par, and recognized globally. Organizations may guarantee that their goods and services are sold and disseminated both domestically and abroad by obtaining FIPS compliance.
Therefore, to be recognized as a reliable supplier of services, goods, or software, organizations should ensure they are included on the FIPS 140-2 compliant list.
FIPS 140-2 compliance frequently appears as a significant security measure for government and defense groups. This is due to the fact that the National Institute of Standards and Technology (NIST) set a strict security standard for it.
A set of security specifications called the Federal Information Processing Standard (FIPS) 140-2 apply to develop or use cryptographic modules in government-run and -approved networks and services.
The standard is crucial in ensuring the authenticity, non-repudiation, secrecy, and integrity of the government’s sensitive assets.
Local governments and certain industries, including those in manufacturing, healthcare, and finance, also need FIPS 140-2 compliance.
What is FIPS 140-2 Compliant Encryption?
FIPS 140-2 compliance is an important security measure for government and defense organizations. It helps secure and integrity of government networks and services and ensures citizens’ personal data privacy and confidentiality.
It guarantees that any devices and services they use fully comply with the highest security standard NIST sets. With this, companies can competently protect their resources and citizens’ data from unauthorized access or manipulation.
Any cryptographic module used in government or military operations must comply with FIPS 140-2 requirements for encryption. Due to its durability and a high degree of security, many commercial and governmental institutions commonly demand it.
Recommended: FIPS 140-2 Encryption for Mobile App Security
The US government has established a set of security standards called FIPS 140-2 that describes the technical, operational, and administrative criteria that cryptographic modules must satisfy in order to be designated as FIPS-compliant.
The Cryptographic Module Validation Program (CMVP) certifies the FIPS 140-2 standard, which is based on the four security levels of Level 1, Level 2, Level 3, and Level 4.
Level 1 is the most basic and is suitable for non-sensitive applications. While coming to the highest Level 4, the security increases and is appropriate for very sensitive data.
How to Validate FIPS?
FIPS 140-2 validation testing is critical for securing cryptographic modules. It is part of the Cryptographic Module Validation Program (CMVP), created by the National Institute of Standards and Technology (NIST) and the Communications Security Establishment (CSE) of the Government of Canada.
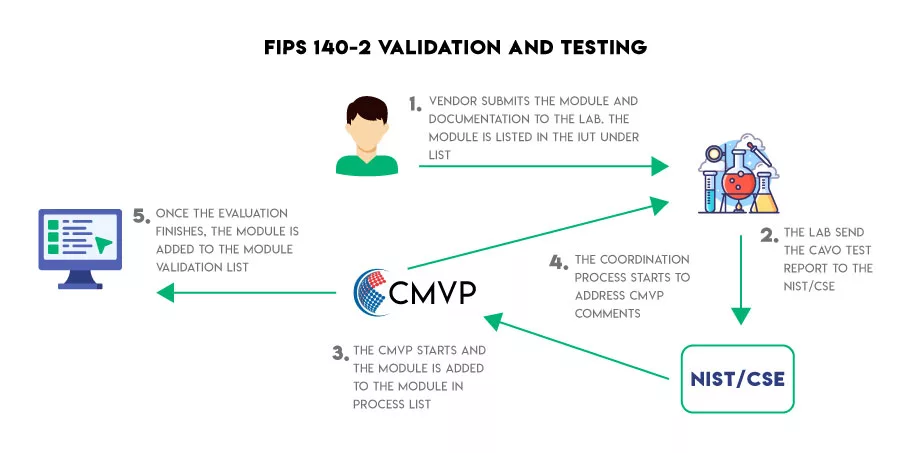
This testing involves a rigorous evaluation of the cryptographic module’s hardware, software, and/or firmware by third-party labs which have been accredited by the NVLAP (National Voluntary Laboratory Accreditation Program) for FIPS 140-1 and FIPS 140-2 testing.
FIPS-140 validation is used to confirm a cryptographic system’s security. It assures that the system complies with the security specifications provided in Federal Information Processing Standards (FIPS) Publication 140-2 because it is based on that publication.
The vendor submits a product sample and its design documentation to the third-party lab for testing. The lab then performs a series of tests to determine if the cryptographic module meets the FIPS 140-2 standard.
These tests include testing the physical security level of the device, checking the security of the software and its underlying design and interface, and validating the random number generator used to generate secure keys. Upon successful completion of all tests, the lab issues a validation certificate.
To complete this process, the product and its accompanying documentation must have the following characteristics:
Finite State Model, Physical Security, Operational Environment, Cryptographic Key Management, Electromagnetic Interference/Electromagnetic Compatibility (EMI/EMC), Self Tests, Design Assurance, and Mitigation of Other Attacks.
The laboratory performs several tests on the item and reviews the supporting documentation to ensure it was created per the specifications outlined in FIPS PUB 140-2.
FIPS 140-2 validation is necessary for storing, transmitting, and receiving sensitive data securely. By ensuring that cryptographic modules meet the FIPS 140-2 standard, organizations can be sure that their data is secure and protected from unauthorized access.
Why FIPS is Important?
FIPS 140-2 compliance is often considered an important security measure for government and defense organizations. This is because the National Institute of Standards and Technology (NIST) set a strict security standard for it.
A set of security specifications called the Federal Information Processing Standard (FIPS) 140-2 apply to developing and using cryptographic modules in government-run and -approved networks and services. The standard is crucial in ensuring the authenticity, non-repudiation, secrecy, and integrity of the government’s sensitive assets.
Due to the high degrees of encryption, FIPS 140-2 compliance is crucial for enterprises that handle sensitive, secret data. The US government established the Federal Information Processing Standards (FIPS) 140-2 guidelines to guarantee reliable, secure data encryption.
To become FIPS compliant, a business must show that its cryptography modules fulfill the stringent guidelines established by the government.
Examples are strong encryption methods, safe key management systems, and appropriate authentication mechanisms. All of this aids in preserving the privacy, accuracy, and legitimacy of data while it is being kept and delivered.
Being FIPS 140-2 compliant might provide an organization an advantage in the market in addition to security advantages. Many businesses now require that their partners be FIPS compliant, particularly those dealing with government data.
Therefore, for businesses to compete in this market, they must comply with FIPS 140-2.
Many organizations, especially the government, have adopted the FIPS 140-2 compliance policy because it lends credibility to their organization and services.
Wrapping up
A validation often takes three months to a year or longer. The type of product being evaluated—whether it’s hardware, firmware, or software—and its complexity, number of algorithms, programming language, etc.—greatly impact this.
Compliance with FIPS is crucial for any firm working with sensitive data and wishing to stay ahead of the competition. Organizations can guarantee the safety of their data.
Also, their clients can trust them with their sensitive information by ensuring that all of their cryptographic modules, key management systems, and authentication procedures adhere to the standards established by the government.
FIPS Compatible Code Signing Certificate
According to the CA/B forum guideline, Now, user’s private key is generated and stored in an HSM (Hardware Security Module) that compliant with FIPS 140‐2 Level 2 and Common Criteria EAL 4+, or equivalent
