What is Token Signing Certificate and How Does it Works?

Code Signing Certificates with Token: A Comprehensive Guide
The most crucial component of any federated partnership is the token-signing certificates, which serve as a key validation method to guard against malicious tampering and security token fraud.
These certificates employ a private/public key pairing to authenticate that a legitimate partner federation server issued a security token and confirm that the token was not altered in transit, these certificates employ a private/public key pairing.
Organizations can successfully stop attackers who might otherwise try to obtain unauthorized access to federated resources by demanding token-signing certificates.
Organizations wouldn’t be unable to trust the security token and may unintentionally give access to bad actors without a safe and trustworthy certificate.
Prerequisites for Token Signing Certificates
You must follow specifications for a token-signing certificate to be configured properly.
- A private key must be present in the certificate.
- The initial setup often takes care of this, but it’s crucial to confirm that the AD FS service account has access to the token-signing certificate’s private key in the local computer’s personal store.
- The AD FS Management snap-in should be used to ensure this access if you modify the certificate at a later time.
- You can be sure that your token-signing certificate will function properly if these conditions are met.
Working on Token-based Signing Across its Partners
The security of digital transactions between two partners relies on the use of token-signing certificates. These certificates contain cryptographic private and public keys used to sign security tokens digitally.
The account partner uses the private key to sign the security token cryptographically. This signature then guarantees the authenticity of the token and is verified by the resource partner using the public key.
In this way, the certificate helps to enable trust and secure communication between partners without needing a third party or trusted intermediary.
In addition, using token-signing certificates helps ensure that the token has not been tampered with or altered in any way. Overall, token-signing certificates help ensure secure data transmission between partners and protect the integrity of digital transactions.
Digital certificates called token-signing certificates authenticate communication between partners or between organizations securely. In order to protect the integrity of data, it is often issued by a root certificate authority (CA) and used to sign and validate digital signatures.
Recommended: What is a Certificate Authority & Key Role of Certificate Authority
The digital signature is validated using a partner’s token-signing certificate’s public key component. When the signature is confirmed, the resource federation server produces its own security token for its organization and signs it with its own token-signing certificate.
The certificate revocation list (CRL) of the token-signing certificate must be available to reliant parties and web servers that trust the federation server to provide trustworthy authentication of the certificate.
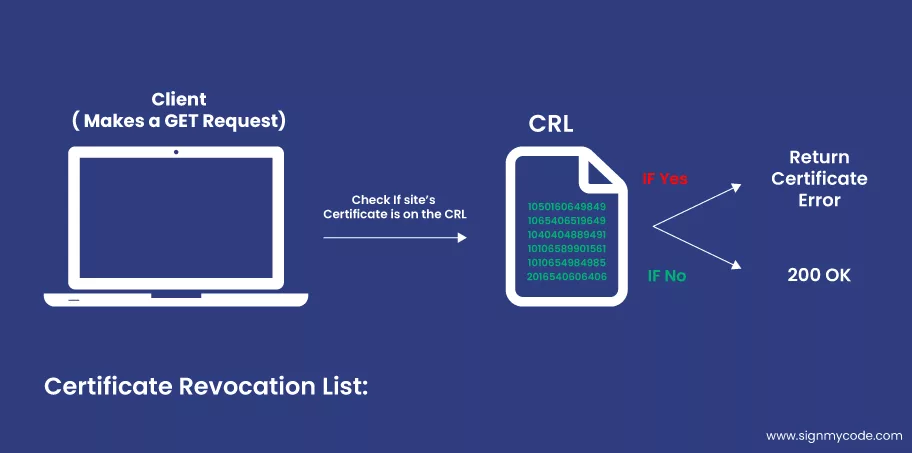
To completely authenticate the token-signing certificate, the dependent parties, and web servers must also trust the root CA certificate. This procedure contributes to the validity and dependability of any digital signatures produced by the token-signing certificate.
The resource partner’s web server employs the token-signing certificate’s public key to verify that the resource federation server signs the security token. The Web server then grants the client the necessary access.
How to Deploy Your Code Signing Certificates with Token?
When deploying the first federation server in a new AD FS installation, you must obtain a token-signing certificate and install it in the server’s local computer personal certificate store.
The method you choose to get the certificate influences the amount of security and trust your environment provides.
To get a token-signing certificate, you have three choices:
- Request one from an enterprise CA
- Request one from a public CA
- Create a self-signed certificate.
The maximum degree of trust and security is provided by requesting a token-signing certificate from an enterprise CA. This option assures that the certificate is issued and signed properly by a trusted, well-known organization. It also ensures that the certificate issuer monitors any potential certificate abuse or revocation.
Requesting a token-signing certificate from a public CA is a viable alternative for firms that do not have access to an enterprise CA or who want a certificate for a limited duration. Public CAs are reputable organizations, and partners and clients commonly acknowledge their certifications.
Recommended: Code Signing with USB Tokens: A Comprehensive Guide
Organizations without access to a reputable CA can create their own self-signed certificates. However, it’s critical to understand that a certificate not issued by a reputable CA is not as secure as one that is. Additionally, AD FS does not support it.
It is crucial to consider your environment’s particular requirements and limitations when deciding how to get your token-signing certificate. Spend time weighing each choice’s advantages and disadvantages before deciding which is best for your company.
Steps of Consideration for Deployment
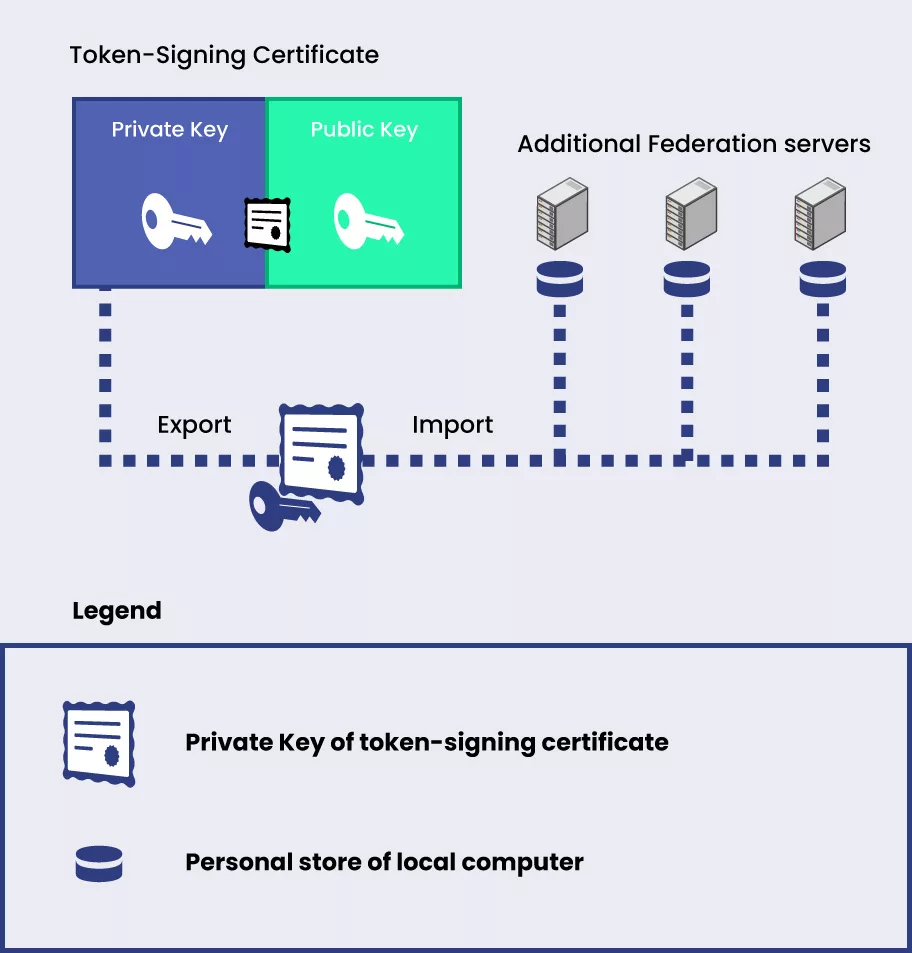
When installing token-signing certificates in a federation server farm, it is crucial to consider the effects of using a single token-signing certificate to sign tokens on different servers.
One private key from the token signing certificate may be exported and shared by all of the federation servers on the farm, which makes this structure simple.
The entire system’s security might be compromised by any system compromise that exposes the private key, even if this deployment methodology may be feasible.
Deploying distinct token-signing certificates on each federation server is recommended to lower the danger of such an attack.
Note: All federation servers in a farm can share the private key from a single token-signing certificate.
How Does Signing a Token Work?
When we look up online, token-based authentication is becoming increasingly common, and its effectiveness depends on how tokens are signed.
Step 1:
To sign a token, one must first create a distinctive digital signature that can be used to validate the signer’s identity. A public/private key pair is typically used for this, with the public key being kept on the server and the private key being kept safely on the user’s device.
Step 2:
When a user submits a request for access, the server receives the token and uses the public key to check the token’s authenticity and the user’s signature.
Step 3:
The private key on the user’s device is then compared to the token, and access is permitted if the two match.
Step 4:
A safe and dependable authentication mechanism is provided by signing tokens, which guarantees that only the individual making the access request truly has access.
Four-step Process for Token Signing Authentication
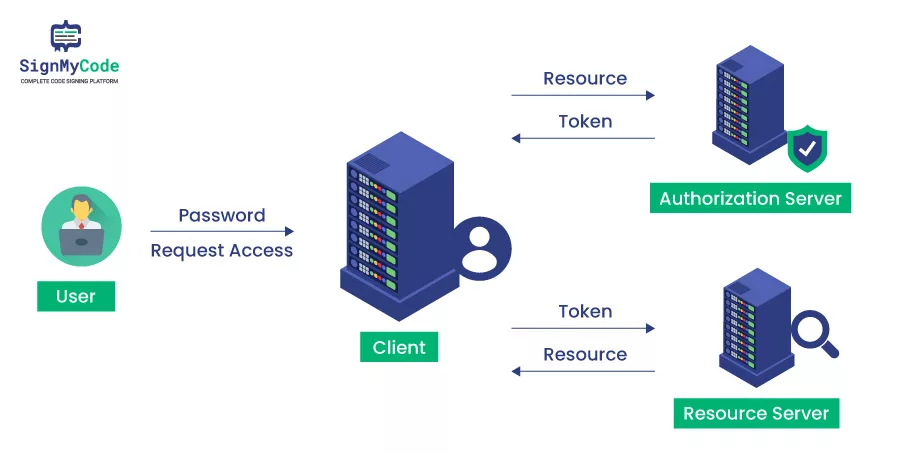
Online token authentication is gradually replacing other authentication methods. It offers high security and is easy to use and secure. The four simple stages for token authentication are as follows:
Step 1: Request Access
The user submits a login and password or another verification form to request access to a protected resource.
Step 2: Authentication
The server checks the credentials against the username or uses another method to confirm the user is authorized to access.
Step 3: Communication
After the authentication tool, such as a ring, phone, or another object, confirms that the user is truly the one who requested access, the server gives a token for usage.
Step 4: Authorization
While the user works, the token is delivered to the server and saved in their browser. The token ensures the user can access the information and resources they seek.
Making ensuring that only authenticated users may access your protected resources is a breeze with token authentication. It is a safe technique to safeguard your data and resources and is simple to set up.
Why are Authorization Tokens a Must for Code Signing?
For code signing, authorization tokens are a crucial security tool. A safe and trustworthy method of demonstrating ownership over software programs and code is provided by tokens. They are growing in popularity as they provide a safe and dependable way to protect code integrity.
Tokens offer a distinctive identity that is linked to a particular user, enabling access restriction and revocation as required. This is especially helpful when a system’s user access varies depending on the day, the hour, or the occasion.
In addition to user credentials, tokens can assist in giving more granular access by giving access depending on particular document features.
Additionally, authorization tokens add another level of security to systems that house sensitive data, making them less susceptible to hacker attacks. Potential hackers will have a lot tougher time gaining access because tokens are a far more secure alternative than a straightforward password.
Ultimately, authorization tokens are a formidable method of safeguarding code and data, allowing secure access, and guarding against potential attacks. Therefore, they are a great resource for providing users access to crucial files and programs.

Wrapping up
When it comes to securing safe access to critical data, Token-based signing is a fantastic tool. When your user base changes due to events or other factors, tokens can help manage user access effectively and offer more granular access control.
Tokens are also very rarely the target of hacking efforts, which makes them perfect for protecting your code and data. Authorization tokens act as the cherry on top. They are the way to go if you want to safeguard your code while yet enabling people to access it easily.
Important Note
Due to new CA/Browser Forum requirements All Code Signing Certificates is now required to store private key in Hardware Security Module compliant with FIPS 140 Level 2, Common Criteria EAL 4+ or equivalent from June 1st, 2023.
