What is X.509 Certificate? How it Works and How to to Obtain it?

An X.509 certificate holds immense significance in digital security, functioning as a digital certificate conforming to the universally accepted ITU X.509 standard.
This standard defines the structure and format of public critical infrastructure certificates. X.509 certificates play a vital role in managing identity and ensuring security.
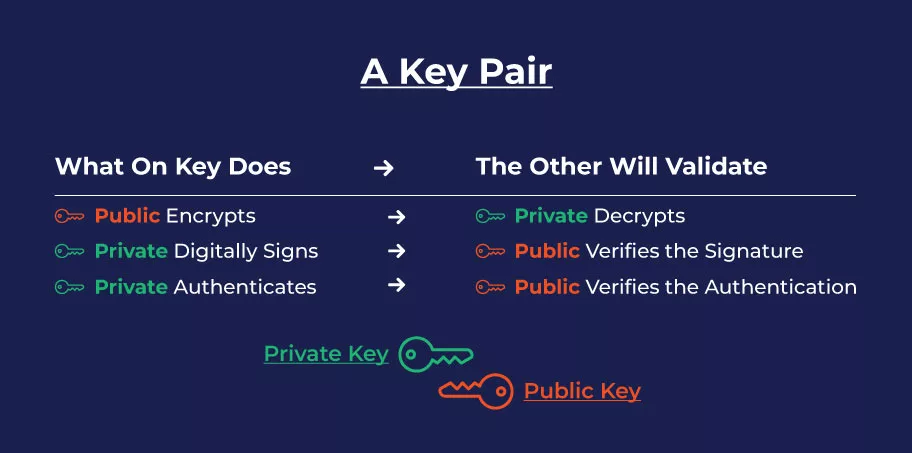
The strength of X.509 certificates lies in their underlying architecture, which utilizes a key pair composed of a public key and a private key. This cryptographic mechanism employs the key pair to encrypt messages, ensuring the sender’s authenticity and the transmitted information’s confidentiality.
Why do you Need an X.509 Certificate?
The primary application of X.509-based PKI is observed in Transport Layer Security (TLS) and Secure Socket Layer (SSL) protocols, forming the foundation of secure web browsing through the widely standard HTTPS protocol.
Nevertheless, the versatility of the X.509 protocol extends beyond web security, encompassing code signing for application security, digital signatures, and various critical internet protocols.
The history of X.509 certificates traces back to their initial publication in 1988. At that time, the Telecommunication Standardization Sector of the ITU (ITU-T) sought to establish standardized rules for issuing certificates.
Consequently, they devised a hierarchical system for distinguished names, drawing inspiration from the global telephone numbering systems and adapting it to meet the dynamic organizational requirements of the Internet age.
Subsequently, in 1996, version 3 of the X.509 standard introduced significant updates by incorporating multiple extensions that remain instrumental in supporting the expansion and evolution of internet applications.
Recent Updates on Buying Code Signing Certificates
The standard is version 9, defined in October 2019, reflecting the continuous advancements in digital security practices. The Internet Engineering Task Force (IETF) working group is responsible for public-key infrastructure.
PKIX, which adopted the X.509 v3 certificate standard. It is developed via Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile standard.
So, X.509 certificates are indispensable components of modern-day digital security, operating on the globally accepted ITU X.509 standard. They ensure secure communication over the Internet and facilitate identity verification.
By embracing a robust keypair system, X.509 certificates empower encryption and decryption processes, safeguarding the integrity of online interactions. The X.509 standard adapts to new requirements as technology advances, fortifying our digital ecosystems.
Recommended: CA/B Forum Baseline Requirements v2.8 for Code Signing Certificates
How can Digital Certificates Advantage you?
X.509 certificates offer numerous benefits that contribute to establishing trust and scalability in the digital realm. These certificates are the fundamental building blocks of digital identities, ensuring trust in various connected processes, including websites, applications, endpoint devices, and online documents.
Without X.509 certificates, the assurance of a website’s authenticity, such as www.amazon.com belonging to Amazon, would be compromised.
Another significant advantage of X.509 certificates lies in their scalability. The certificate-based approach, facilitated by the Public Key Infrastructure (PKI) architecture, enables the secure exchange of billions of messages daily within organizations and across the internet.
This scalability is achieved through the vast and open distribution of public keys without compromising the private key’s confidentiality required for message decryption. This robust infrastructure ensures malicious actors cannot access sensitive information despite the vast volume of digital transactions.
X.509 Certificates: Enabling Trust for Companies
The trustworthiness of X.509 certificates stems from their functionality and issuance process. The certificate’s fundamental usage architecture verifies a public key’s association with the corresponding hostname/domain, organization, or individual listed in the certificate.
Moreover, the trust is further reinforced when the certificate is signed by a widely recognized Certificate Authority (CA) like Sectigo, Comodo, Certera or by being self-signed.
When a trusted CA signs a certificate, it instills confidence in the certificate user that the certificate’s owner or associated hostname/domain has undergone thorough validation. Conversely, self-signed certificates possess less trust as they do not undergo additional validation before issuance.
Recommended: Self-Signed vs. Publicly Trusted CA Code Signing Certificates: What to Choose?
Operating X.509 Certificates for Digital Signing
X.509 certificates are built on the X.509 standard, which uses the Abstract Syntax Notation One (ASN.1) interface description language. ASN.1 specifies data structures that can be serialized and deserialized across platforms.
ASN.1 supports message encryption and decryption inside the X.509 certificate format by utilizing a matching public and private key pair.
X.509 certificates commonly employ three widely used algorithms to generate public keys.
Rivest–Shamir–Adleman (RSA):
This algorithm is named after its creators, Ron Rivest, Adi Shamir, and Leonard Adleman. It is based on the mathematical properties of prime numbers and the difficulty of factoring large numbers. RSA generates a robust public key that can be used for encryption and a private key for decryption.
Elliptic Curve Cryptography (ECC):
ECC is an encryption scheme. It leverages the mathematics of elliptic curves to provide strong security with relatively shorter key lengths compared to other algorithms. ECC-based public keys are widely used in X.509 certificates for their efficiency and effectiveness.
Digital Signature Algorithm (DSA):
DSA is a cryptographic algorithm used for generating digital signatures. It relies on the discrete logarithm problem in a prime modulus group to provide secure signatures.
While DSA is primarily used for generating digital signatures in X.509 certificates, it can also generate critical pairs for encryption and decryption.
RSA, ECC, and DSA algorithms are the most common in X.509 certificates for generating secure public keys. The choice of algorithm depends on factors such as security requirements, computational efficiency, and specific use cases.
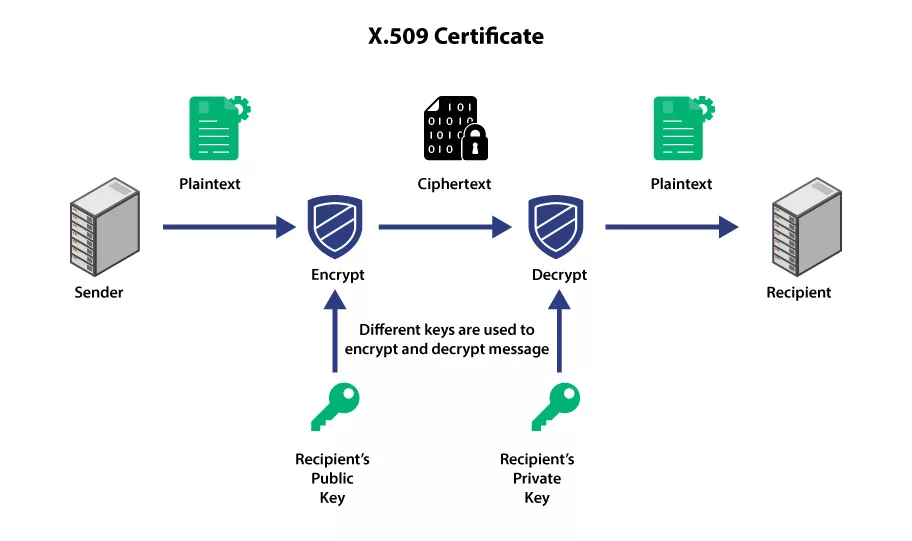
Functioning of Public and Private Keys in Encryption
For encryption, public and private keys are crucial in securing communication and safeguarding sensitive information. The public key, consisting of a sequence of random numbers, encrypts a message.
The intended recipient can only decipher and read this encrypted message with the corresponding private key. Like the public key, the private key is also a long string of random numbers. However, it remains confidential and is exclusively known to the recipient.
The publication of the public key is an essential aspect of its functionality. It is made available to the world, allowing anyone to access it.
Recommended: Differences Between Encryption and Signing?
However, the encryption mechanism ensures that only the intended recipient possesses the means to decrypt the encrypted message. It uses their private key. Provide adversary gains access to the public key, so they cannot decipher the message without the corresponding private key.
To ensure the security of public key encryption, complex cryptographic algorithms are employed to create public keys. These algorithms generate random numeric combinations of varying lengths, making it extremely difficult for attackers to exploit the keys through brute force attacks.
This approach intends to provide substantial protection, ensuring that unauthorized individuals cannot deduce the private key from the public key, thus maintaining the confidentiality and integrity of encrypted messages.
About Certificate Revocation Lists (CRLs) and Certificate Encoding
In compliance with the X.509 standard, certificate authorities (CAs) can utilize a certificate revocation list (CRL) to maintain records of digital certificates revoked before their scheduled expiration dates. Revoked certificates are considered invalid and should no longer be trusted for secure communications.
CRLs serve as a means to distribute information about these revoked certificates, providing a simple way to check the validity of a certificate against the list.
Recommended: What is a Certificate Authority & Key Role of Certificate Authority
However, it’s worth noting that popular web browsers and clients are gradually deprecating the use of CRLs. Instead, alternative mechanisms such as the Online Certificate Status Protocol (OCSP) and OCSP stapling are being favored due to their ability to provide real-time certificate revocation status.
While the X.509 standard specifies various aspects of digital certificates, it does not explicitly define how the contents should be encoded for file storage.
The two commonly used encoding schemas are prevalent for storing digital certificates in files:
Distinguished Encoding Rules (DER):
DER is the most commonly used encoding schema for digital certificates. It addresses the encoding of various data objects in a certificate. Certificates encoded in DER format are binary files and cannot be easily read using text editors.
However, they can be efficiently processed by web browsers and many client applications, making DER the preferred choice for certificate storage and transmission.
Privacy Enhanced Mail (PEM):
PEM is a standard for email encryption that can decode DER-encoded certificates into text documents. PEM-encoded certificates are represented in Base64 encoding, allowing them to be easily read and handled as text files. This format facilitates compatibility with text-based systems and simplifies certificate management tasks.
Depending on the specific use case and requirements, DER and PEM encoding schemas offer advantages. DER provides optimal efficiency and compatibility, while PEM allows for human-readable representations and interoperability with systems relying on text-based formats.
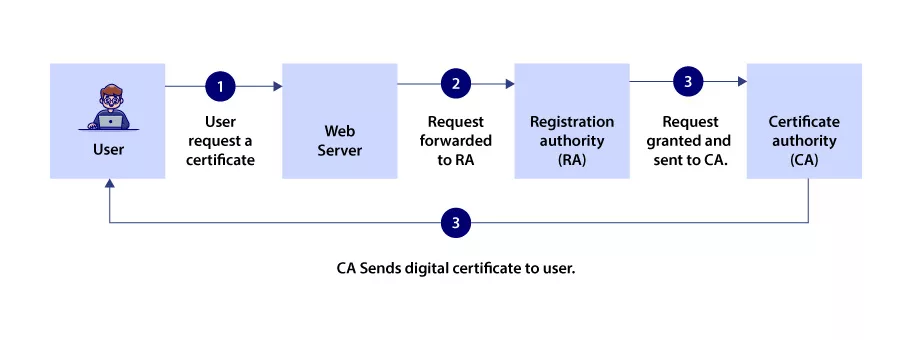
The Process to Obtain an X.509 Certificate: Trusted CA
To acquire an X.509 certificate, engaging with a trusted certification authority (CA) or agent responsible for issuing certificates and managing the associated public keys is crucial.
- A reliable CA ensures that senders can establish secure connections using the correct public key associated with the recipient’s private key, mitigating the risk of interception and misuse of sensitive information.
- Certification authorities function as trusted third-party entities that serve as CAs. However, many enterprises and technology providers act as their own CA, responsible for issuing certificates internally. In such cases, they may also employ self-signed certificates.
- Regardless of the approach chosen, the certificate authority must instill trust by thoroughly verifying the identity of all senders whose public keys they publish. This verification process ensures that the published public keys are genuinely associated with the corresponding private keys of the senders.
- The role of the CA extends beyond identity verification. They are also responsible for maintaining robust information security practices within their organization to safeguard against malicious attacks. By prioritizing security measures, CAs help uphold the integrity and reliability of the entire X.509 certificate infrastructure.
- Choosing a trusted certification authority is essential to establish a secure and trusted environment for issuing and managing X.509 certificates.
- Whether organizations rely on reputable third-party CAs or establish their own internal CA, the core principle remains the same; Ensuring the legitimacy and trustworthiness of the CA!
It is paramount to enable secure communications and protect sensitive data from unauthorized access or misuse.
How Does Key Size in Public Key Cryptography Ensure the Power of Protection?
In public key cryptography, the key size or bit length of public keys is critical in determining the strength of cryptographic protection. A more significant key enhances security against malicious attacks and unauthorized decryption attempts.
For instance, the use of 2048-bit RSA keys is prevalent in various applications such as SSL certificates, digital signatures, and other digital certificates.
Selecting a specific key size is crucial as it directly impacts the complexity and computational effort required to crack the encryption algorithm. With a larger key size, the number of possible combinations significantly increases, making it exponentially more challenging for hackers to break the encryption by brute force.
As a result, more extended key sizes provide a higher level of cryptographic security, ensuring the confidentiality and integrity of sensitive information.
Recommended: Examples of Digital Signatures & Certificates for Organizations
Standards organizations, like the CA/Browser Forum, play a vital role in establishing baseline requirements for supported key sizes.
These organizations define industry standards and guidelines that govern the minimum key sizes considered secure for various cryptographic operations. Organizations and certificate authorities contribute to a more secure digital ecosystem by adhering to these standards, reducing the risk of successful attacks and unauthorized access.
Popular X.509 Certificate Extensions
X.509 version 3 introduced various extensions to support expanded functionalities for client applications in the digital landscape. Among the commonly used X.509 certificate extensions today are Subject Alternative Name (SAN) and Key Usage.
Subject Alternative Name (SAN) Extension:
The Subject Alternative Name extension enables the association of different identities with a certificate’s public key. This extension includes various entities within a single certificate, such as alternative domains, DNS names, email addresses, and IP addresses.
By leveraging the SAN extension, Certificate Authorities (CAs) can issue multiple-domain certificates, often called SAN certificates. These certificates offer enhanced flexibility by accommodating multiple identities within a single certificate, simplifying the management of diverse digital environments.
Key Usage Extension:
The Key Usage extension defines limitations on the cryptographic key’s usage for specific purposes. For instance, it can designate a key as “signing-only,” indicating that it should only be utilized for digital signing operations, not encryption or other purposes.
This extension allows fine-grained control over how the keys within a certificate can be used, enhancing security and aligning with specific requirements or policies.
Recommended: Top Best Practices for Storing X.509 Private Keys
Using the above Key Usage extension, organizations can enforce strict usage constraints on their certificates, ensuring that the keys are utilized appropriately and following predefined guidelines.
These two X.509 certificate extensions, Subject Alternative Name and Key Usage provide expanded functionality and flexibility in digital certificate management.
The SAN extension enables the inclusion of different identities within a certificate, facilitating multi-domain certificates. In contrast, the Key Usage extension allows precise control over crucial utilization, ensuring adherence to specific usage policies.
What are the Components of X.509 Certificate Fields?
X.509 certificate fields contain essential information about the certificate’s recipient and the issuing Certificate Authority (CA). These fields are crucial to establishing trust and ensuring the certificate’s integrity. Some of the standard fields found in X.509 certificates include:
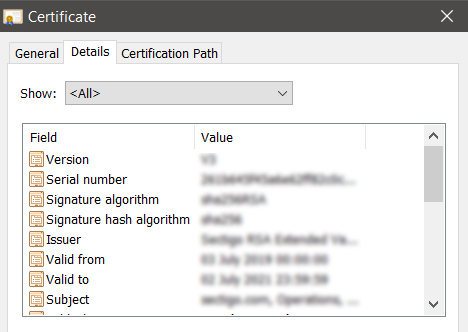
Version:
The version field denotes the specific X.509 version applicable to the certificate. It indicates the format and structure of the certificate and helps determine its compatibility with different systems and protocols.
Serial Number:
A unique serial number assigned by the CA distinguishes each X.509 certificate from others. This identifier aids in differentiating and tracking individual certificates, preventing confusion or ambiguity.
Algorithm Information:
This field provides details about the cryptographic algorithm employed by the CA to sign the certificate. It specifies the algorithm’s parameters, ensuring the integrity and authenticity of the certificate.
Issuer Distinguished Name:
The issuer distinguished name field contains the name of the CA responsible for issuing the certificate. This information helps establish the authority and credibility of the certificate, as it confirms the identity of the issuing entity.
Validity Period:
The validity period field specifies the start and end dates and times during which the certificate is considered valid and can be trusted. This period signifies the duration for which the certificate can be utilized for secure communication and authentication.
Subject Distinguished Name:
The subject distinguished name field refers to the name of the entity to which the certificate is issued. It identifies the recipient of the certificate, providing crucial information about their identity.
Subject Public Key Information:
This field contains details about the public key associated with the identity mentioned in the subject distinguished name field. It enables verification and encryption processes, as the public key allows for secure communication and message encryption.
How do you Establish Trust through Hierarchical Certificate Chains?
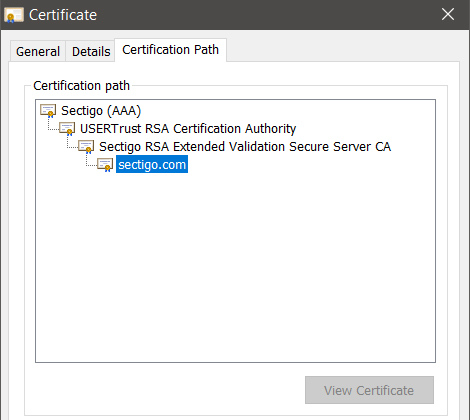
Hierarchical trust chains are crucial in reinforcing the trustworthiness of identities. These chains consist of multiple digital certificates, forming a hierarchical structure incorporating several verification layers. A
s mentioned, each certificate within the chain must undergo the X.509 verification process and be signed by an issuer Certificate Authority (CA).
The CA is responsible for signing a certificate explicitly identified and stored in the certificate’s root. However, the trust chain can also include intermediate certificates, which must be validated to ensure the integrity and authenticity of the certificate.
To illustrate this process, consider a scenario where a web browser client encounters a certificate. To establish trust, the client must follow the hierarchical path of certification, taking into account any intermediate certificates required for validation.
This recursive validation process returns to the root CA in the client’s trust store. By completing this verification, a complete chain of trust is formed.
These hierarchical certificate chain organizations enhance the trustworthiness of digital identities. Each certificate within the chain, from the leaf certificate to the intermediate certificates and, ultimately, the root CA, contributes to the overall validation process.
This hierarchical structure allows for a systematic and layered approach to identity verification, bolstering the security and reliability of digital communications.
Wide Range of Applications for X.509 Public Key Infrastructure
The X.509 public key infrastructure (PKI) is widely utilized in various applications across the internet, playing a crucial role in ensuring security and establishing trust. Here are some typical applications of X.509 PKI technology:
Web Server Security with SSL/TLS Certificates:
One of the primary applications of X.509 certificates is securing web servers by implementing SSL/TLS protocols. SSL certificates authenticate the identity of web servers and enable secure connections using HTTPS.
Without SSL certificates, cybercriminals could exploit vulnerabilities and intercept sensitive information through attacks like man-in-the-middle. SSL/TLS certificates based on X.509 provide a vital layer of protection for secure browser connections.
Digital Signatures and Document Signing:
X.509-based certificates are also employed for digital signatures and document signing. Digital signatures leverage PKI to authenticate the signer’s identity and ensure the signed document’s integrity.
By encrypting a hash of the document using the sender’s private key, digital signatures bind the signature to the original message, preventing alteration or duplication. It enables the verification of sender authenticity and ensures the document’s integrity.
Code Signing:
Code signing is another application of X.509 certificates that provide assurance and integrity for software programs. Developers digitally sign applications, drivers, and software using certificates, allowing end users to verify that a third party has not altered or compromised code.
Code signing certificates include the developer’s signature, company name, and timestamping, instilling trust and mitigating risks associated with malicious code.
Email Certificates:
S/MIME certificates based on X.509 technology validate email senders and encrypt email content, protecting against advanced social engineering and spear phishing attacks.
S/MIME certificates enable the encryption and decryption of email messages and attachments while verifying the sender’s identity, ensuring the email’s authenticity and integrity.
SSH Keys:
X.509 certificates are also employed as SSH keys for secure access to the SSH protocol. SSH keys are widely used for communication in various environments, including cloud services, network settings, file transfer tools, and configuration management tools.
Organizations utilize SSH keys to authenticate identities and safeguard services from unauthorized access and potential threats. These keys enhance security, enable automation, and facilitate single sign-on (SSO) and identity and access management.
Digital Identities:
X.509 digital certificates play a critical role in authenticating digital identities. Securing identities becomes paramount as data and applications expand across diverse networks and devices.
X.509 certificates effectively authenticate devices, individuals, data, or applications, improving security by replacing vulnerable passwords. These certificates enable organizations to establish secure digital identities, ensuring trusted access to resources and protecting against unauthorized access.
Wrapping up
We know that X.509 certificates bring forth many advantages. They establish trust for various organizations, enabling secure interactions across their platforms.
Their scalability provides a reliable framework for organizations to exchange messages securely, safeguarding valuable data. X.509 certificates are pivotal in digitally maintaining virtue and security, contributing to online processes’ seamless functioning.

