Examples of Digital Signatures & Certificates for Organizations

When Should You Use a Digital Signature Certificate?
Digital signature certificates are a must-have for any organization interested in ensuring the authenticity of its data and transactions. As a software developer, you can use them to sign software updates or as a sales manager to authenticate contracts. Digital signature certificates are the ultimate guarantee of security and validity.
Digital signature certificates provide a secure and reliable way to verify and authenticate data. They enable organizations to establish trust and ensure digital documents, transactions, and communications legitimacy. They are used to sign, encrypt data and verify the document’s authenticity or contents, ensuring that the data has not been tampered with.
What do you Understand by a Digital Signature?
Digital signatures, also known as public key signatures, are a cryptographic method of verifying who created a digital asset and ensuring that a third party has not modified it.
Examples of these items include emails, PDFs, Word documents, software code, etc. Commonly, digital signatures are depicted with visual elements, such as a ribbon or badge, in Microsoft Outlook.

For digital signatures, a digital signature certificate is required. It attests to the signer’s identity as an electronic passport. It contains the signer’s public key and other information. A digital signature certificate is issued by a trusted third-party certificate authority (CA) and must be validated.
Digital signatures are becoming increasingly popular for verifying the authenticity of digital documents and are an essential part of secure digital transactions. By using a digital signature, you can be sure that the paper you’re receiving hasn’t been tampered with and that you are communicating with the right person.
Examples of Using a Digital Signature Certificate?
Organizations should use digital signature certificates to authenticate digital documents or transactions.
For example, software developers may need digital signature certificates to sign software updates, or sales managers may require them to authenticate contracts.
Digital certificates also enable organizations to securely and reliably exchange data with other organizations.
To ensure the security and validity of your data and transactions, it is essential to always use digital signature certificates. They provide the ultimate guarantee of authenticity and trust for both the organization and its customers.
Create a Website that your Visitors Trust
As business owners, establishing trust with potential customers can be difficult. Fortunately, a digital signature from a reputable authority such as the Chartered Accountant (CA) organization can make a huge difference. Winning your customers’ belief in a website is essential for any business.
By having a secure and legitimate website, you can ensure customers’ trust and thus increase their engagement. To demonstrate the legitimacy of your website, you need to have a file (e.g., an SSL/TLS certificate) sent from your server to the visitors’ browsers. This file contains the essential information visitors need to trust your website.
You want to give visitors to your website a reason to trust it; you want them to feel safe and secure when interacting with your online presence.
An SSL/TLS certificate is an essential step in building that trust. An SSL/TLS certificate provides authenticity – it verifies that your website is communicating with a legitimate server. This certificate makes visitors more likely to trust your website and your company. Doing so will help build strong relationships and foster customer loyalty.
Under the CA’s digital signature, this widely regarded organization is effectively endorsing you and stating that you have been thoroughly investigated and are trustworthy.
Such a method to demonstrate your company’s legitimacy is fundamental in light of recent Bolster statistics showing that their algorithms spotted approximately 10.7 million phishing and scam pages in 2021 alone.
More concretely, this implies that every day and year, Bolster’s team discovers 29,190 fake pages. This means that your potential customers have to be extra vigilant when it comes to trusting websites, so you must give them an added level of assurance by offering a digital signature from a reputable CA.
By using the CA’s digital signature to validate the safety of your website, you want to give visitors to your website a reason to trust it. This can increase their confidence in your product or service, leading to higher conversions and a better customer experience.
You Require a Means of Uuthenticating your Microsoft Office & PDF files
In today’s cyber landscape, it has become increasingly important to authenticate the Microsoft Office, Excel, and PDF files sent or received over email.
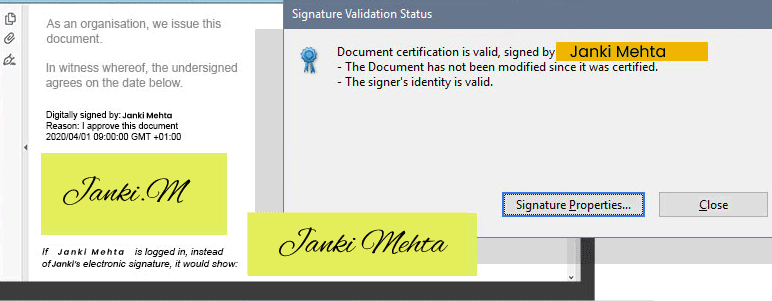
With the prevalence of cybercrime, it is no longer enough to trust that the file being sent or received is genuine. To add an extra level of assurance, you need the means to demonstrate file authenticity.
It is critical to implement tools to validate the authenticity of the file. These tools should focus on ensuring the integrity and authenticity of the file and verifying the author.
Digital signatures, cryptographic hashes, and cryptographic keys are all suitable methods of checking file content, while certificates and encryption can protect the communication channel.
By verifying a file’s authenticity, companies and organizations can ensure the shared data is valid, safe, and secure. Organizations and individuals will be able to have peace of mind knowing that the files received and sent via email are authentic and free from malicious actors. Doing so will also protect the user’s reputation and prevent potential data breaches.
Using a combination of tools and techniques, you can ensure the authenticity of your Microsoft Office, Excel, and PDF files. Not only will this increase security, but it will also provide an extra layer of assurance when exchanging confidential files.
Authenticating without taking the Risks that Come with using Typical Passwords
Authentication has become a necessity in order to protect important materials from cybercriminals. However, as technology advances, so do cybercriminals’ techniques to gain access. Therefore, organizations need to find ways to authenticate securely without taking the risks of using specific passwords.

This is a method of verifying the user’s identity without entering a username or password and being more secure than traditional username and password procedures.
Organizations can also update their authentication mechanisms periodically to stay ahead of cybercriminals. This can include regularly patching systems, implementing strong encryption methods, and employing two-factor authentication.
Honestly, no ideal authentication mechanism that can guarantee security 100%. However, by making yourself as tough of a target as possible increases the likelihood that 99% of cyber criminals will move on and look for easier prey.
This can be done by verifying a user’s identity without entering a username or password and updating authentication mechanisms regularly.
Get Rid of the Alert Messages Customers Get When They Download Your Software
Having your software programs freely downloaded by customers is excellent for business. However, customers often get alert messages when attempting to download your program, such as “My antivirus is blocking this program” or “This file looks suspicious.”
These warnings can damage your reputation as a software developer and make customers think twice before downloading your software.
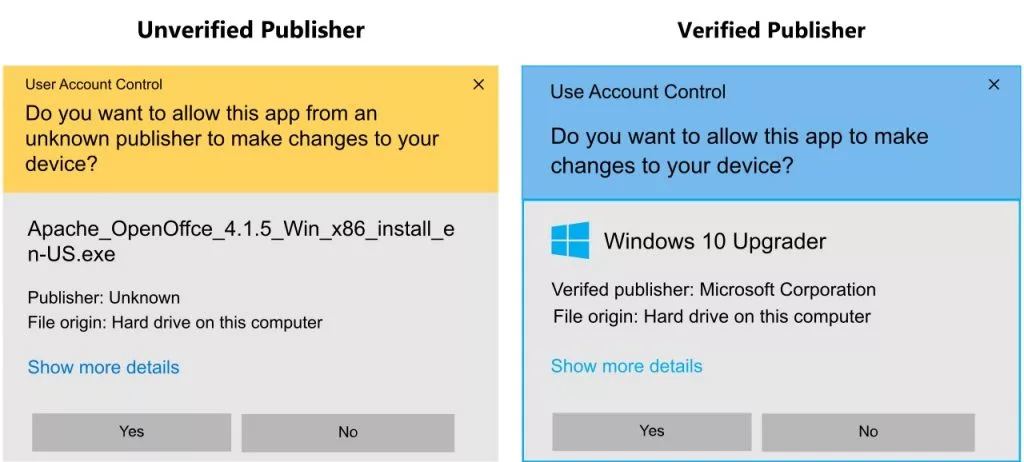
To make sure these alert messages don’t happen, you need to make sure your software is genuine and unaltered. This will give your customer the confidence they need.
The best way to do this is to use a code signing certificate. This certificate verifies the authenticity of your software, and both organizational (standard) and extended validation levels are available.
Recommended: OV vs EV Code Signing: Difference to Know
By using a code signing certificate, you can eliminate the alert messages customers get when they download your software, giving them the peace of mind to proceed with the download. Choosing the right certificate is crucial, so research thoroughly before deciding which one to use.
Confirming the Authenticity of Your Email Messages to Recipients
Phishing is a cyberattack technique hackers use to gain access to your accounts and information. It is a form of social engineering, targeting unsuspecting victims by sending them suspicious emails, often in the form of a fake invoice, receipt, or message from a seemingly legitimate source. These emails can contain malicious links or attachments, prompting recipients to click or download them.
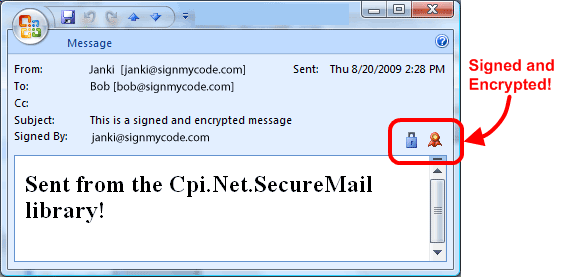
To ensure that your organization and its customers do not fall victim to phishing, you must be vigilant about confirming the authenticity of your emails to recipients.
Every email should be scrutinized to ensure that all links, attachments, and other content are not malicious. You should use a two-step authentication process to prove the legitimacy of the email and its sender.
Another precautionary measure is to include a logo or signature in your emails to indicate that it is coming from your organization. This will provide recipients with a visual verification that it is authentic. Additionally, providing recipients with a phone number they can call to confirm its authenticity will also be helpful.
By taking these steps, you can reduce the risk of a successful phishing attack on your organization and keep customers’ information secure. Remember: Confirm the authenticity of your emails before sending them to ensure that your staff and customers remain safe.
Overall, using a digital signature from an authority such as the Chartered Accountant organization effectively demonstrates that your website is trustworthy and legitimate.
Additionally, it can help your customers feel more confident in their decision to engage with your company, which could lead to increased conversions and improved customer satisfaction.
Wrapping up
Organizations must demonstrate their digital documents’ authenticity and validity in modern communications and commerce.
Digital Signatures and Certificates provide a secure way to prove the validity of Microsoft Office and PDF files and eliminate unknown publisher warnings received when downloading software from a website.
Furthermore, digital signatures provide a way to authenticate emails without the risk associated with conventional passwords. We hope you understood the examples of times when digital signatures and certificates were needed.

