Software Supply Chain Attacks: Notable Examples and Prevention Strategies

What Is a Supply Chain Attack?
Supply chain attack is a kind of cyberattack which targets the network that is made up of suppliers, vendors, contractors and other business partners that organizations rely on to provide goods and services.
As opposed to directly attacking a target organization’s systems or infrastructure, attackers use supply chain vulnerabilities to gain unauthorized access or compromise the integrity of products or services.
In a supply chain attack, hackers usually exploit a trusted entity of the supply chain, for example a software vendor or a third-party service provider, and compromise their computer systems or networks. They achieve this by introducing malicious codes, malwares, etc into the systems or services supplied by the victim.
The tainted products and services containing malicious payloads become available to their final users or customers; the payloads are then triggered causing the attackers to break the target organization’s systems, steal valuable information, or compromise operations.
How Do Supply Chain Attacks Work?
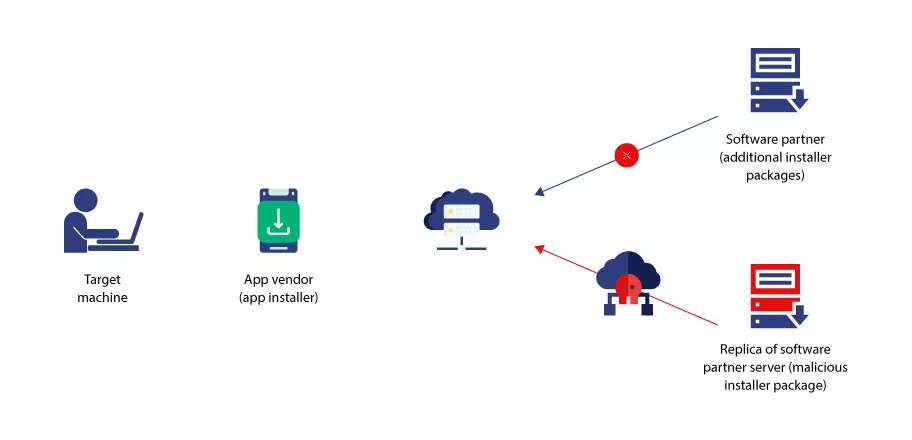
Supply chain assaults are conducted by leveraging for exploitation the vulnerabilities or loopholes of the intertwined network of suppliers, vendors, contractors and partners that organizations depend on to provide goods and services to their customers.
Such assaults usually include several stages and techniques of intrusion into victim systems and theft of sensitive data or assets. Here’s how supply chain attacks typically work:
- Identifying Targets: Attackers search for potential targets from the supply chain: software vendors, third-party service providers, or contractors, who have access to systems or data of the target organization. They may in addition look for the weak points in the supply chain infrastructure like insecure communications or weak authentication methods.
- Initial Compromise: After potential targets are known, attackers try to infiltrate their systems and infrastructure illegally. This may entail leveraging known vulnerabilities, carrying out phishing to steal credentials, or deploying malware to hack the systems. The objective is to find a point of entry in the supply chain network.
- Lateral Movement: Attackers then laterally move within the organization’s supply chain network, trying to achieve access to additional systems or resources. They can also use trust relationships between entities within the supply chain or abuse compromised credentials for privilege escalation to access more sensitive data or systems.
- Introducing Malicious Payloads: Attackers will continue to gain more access within the supply chain network until such a point where they can also introduce backdoors or malware into the products or services provided by the compromised source. This includes manipulation of software updates, insertion of malicious codes in firmware or hardware components, or illegally accessing physical supply chain processes.
Examples of Recent Supply Chain Attacks
1. SolarWinds
The SolarWinds attack (involving supply chain disruption), detected in December, 2020, is one of the most advanced and far-reaching hacking attempts so far. Attacking SolarWinds, the leading IT software provider, the attack aimed at Orion platform, widely used by government agencies, Fortune 500 companies, and organizations at large.
First, hackers managed to bypass SolarWinds’ perimeter defenses and broke into the internal systems. Probably, they distributed malicious phishing emails or exploited vulnerabilities.
Further, they secretly installed a backdoor into Orion updates. The Sunburst or Solorigate backdoor, a malicious program, was covertly installed, sending orders to the command-and-control servers controlled by the perpetrator.
The bad updates were unknowingly distributed to SolarWinds’ vast customer base during standard software updates, therefore involving many government agencies in the U.S. and large corporations.
After the period of dormancy, the backdoor was activated giving attackers a chance to exfiltrate the sensitive high-value data in the system, apart from moving laterally within the networks and possibly deploying new malware.
The discovery of the cyberattack by cybersecurity firm FireEye led to a broader investigation which revealed the magnitude of the attack and prompted a joint effort from the governments, cybersecurity firms, and affected organizations to respond.
The SolarWinds attack did not only compromise data and infrastructure but it also affected SolarWinds’ and its customers’ reputation which demand a combined effort from stakeholders to improve supply chain security practices and safeguard against future threats.
2. ShadowHammer
The supply chain ShadowHammer attack, spotted in 2019, is widely considered a critical episode of cyber infiltration. Targeting on ASUS, a known elaborate computer hardware and electronics manufacturer, the assault exploited its compromised ASUS Live Update Utility tool to pwn over hundreds of thousands of systems around the world.
By breaching into the servers of ASUS the attackers were able to push tainted software updates to ASUS customers that spread a backdoor that could be used to install other malware. Notably, the attackers targeted a specific subset of users in a manner which demonstrates a high level of sophistication and precision.
The ShadowHammer attack reinforces the security risk associated with supply chain infiltration and manipulation, and the need for secure systems and vigilant monitoring to detect and mitigate such events.
Even though ASUS has taken measures to remedy the breach and increase the security controls, ShadowHammer episode constitutes a case in point of how the supply chain remains vulnerable to sophisticated attackers.
3. TSMC
The TSMC (Taiwan Semiconductor Manufacturing Company) 2018 incident revealed supply chain attacks as the basis for the vulnerability of critical infrastructure. TSMC, as the one of the largest of the world’s foundries, is a very key player in the global tech supply chains.
The Wannacry ransomware variant, which spread through TSMC’s computer network, is the cause of the security incident.
The attack impacted TSMC’s production processes, leading to substantial production delays and also financial damages. TSMC initially dismissed the incident’s ramifications, but later admitted the huge disruption caused by the ransomware attack.
This event shed light on the wide impact of the supply chain loopholes in the semiconductor sector and demonstrated the importance of implementing a strong cybersecurity regime to secure the critical assets from evolving threats.
For various industries, like electronics, telecommunications, and also automotive, semiconductor producers TSMC is the backbone. Therefore, they represent very critical targets for the cyber attackers attempting to destabilize global supply chains and also economies.
The TSMC incident is a wake-up call for the organizations across sectors to put supply chain security and resilience at the forefront in a world where connectivity is becoming ever more pervasive.
4. Target
The Target data breach of 2013 is probably the most high-profile supply chain attack. This attack gave insight into the vulnerabilities within a network of retailers and their service providers.
In this high-profile case, cybercriminals used a supply chain vulnerability exploited through a third-party HVAC vendor.
Having gained access to the vendor’s systems, attackers infiltrated Target’s network allowing them to install malware on point-of-sale systems in the retailer’s stores.
This malware captured the payment details effectively having information on more than 40 million customers. The incident not only inflicted substantial financial losses to Target, through litigation and damage to its reputation, but also raised the issues of security practices done by other organizations all through the supply chain.
It is another important aspect in which cybersecurity management for vendors is highlighted and the need for continuous evaluation and monitoring to reduce the risk of supply chain attacks.
The Target data breach was an eye-opening example of what can happen when the interdependent networks that form the foundation of today’s commerce are not adequately secured and thus stresses the importance of remaining alert to the continuing cyber threat.
5. Home Depot
The Home Depot data breach in 2014 is another renowned instance of a supply chain attack that also brought to light security gaps in the retail industry, thus, encouraging the adoption of stronger cybersecurity practices at intertwined systems of suppliers and partners.
This breach was accomplished by cybercriminals taking advantage of a weakness in the Home Depot’s supply chain via a third party vendor. They likely obtained access to the retailer’s network using the credentials of compromised user’s or some other method.
Having penetrated Home Depot’s corporate network the intruders put in place their highly sophisticated malware onto the retailer’s point-of-sale (POS) systems, which are usually located at checkout counters in Home Depot stores in the US and Canada.
Targeting payment card information such as credit and debit cards numbers that was processed and stolen secretly from customers while massaging fraudsters’ excavation.
The breach caused far-reaching effects, as it involved about 45,5 million customers from Home Depot’s stores from several months.
The event also exposed data on personal information such as credit card data and email addresses which resulted in identity theft and financial fraud. In total, the incident caused huge financial losses for Home Depot, including legal settlements, penalties, as well as the costs related to the remediation process and loss of reputation.
6. NotPetya
NotPetya is related to a malicious software attack that happened on the 27th of June 2017. A variation of ransomware, it was one of the fastest computer viruses known, propagating worldwide mainly on Windows platforms.
NotPetya employed several propagation methods, including the exploitation of vulnerabilities in Microsoft Windows and spreading through phishing emails.
Different from typical ransomware which encrypts the files and vindictive extorts for decryption, NotPetya has been deployed with wreckage as the main target rather than profit. It secured the master boot record (MBR) of infected computers with a password, and disabled the boot system.
It also encrypted files and made them undecipherable. But in the end NotPetya’s encryption was found to have been implemented poorly meaning that the recovery of files even with payments was unlikely.
Remember Petya was mainly the installation of its malware in Ukraine but with time has now spread across the world, affecting thousands of systems. It resulted into a serious disruption of the normal operations of businesses, government agencies and the vital infrastructure like banks, airports, and power companies
Who was behind the NotPetya attack is still under dispute by cybersecurity experts. Initial reports have indicated that it was a reason for a typical ransomware attack; in a closer look it was found out that it was destructive in nature and similarity to the before known malware referred to as Petya.
Secure Cyber Consultants believe that NotPetya was probably a state sponsored cyberattack aimed at destabilizing Ukraine, some suggested that it was a financially motivated attack that went wrong.
Regardless of its origin, the NotPetya attack highlighted the need for strong cybersecurity measures, regular software updates and efficient data backup procedures to minimize the disastrous impact of such malicious activities.
7. REvil
The REvil, also known as Sodinokibi, is notorious Ransomware-as-a-service (RaaS) group, that has become known for carrying out a series of devastating supply chain attacks targeting Managed Service Providers(MSPs) and their clients REvil is structured as a well-dressed cyber criminal gang and uses the subscription model, where affiliates pay for the access to the ransomware platform in order to run attacks.
One of the very famous supply chain attacks is attributed to REvil and it happened in July 2021, when the group performed an attack by using a vulnerability in Kaseya’s VSA software that is a remote monitoring & management tool used by MSPs to manage IT infrastructure for their clients.
Compromising Kaseya Software’s update mechanism enabled the REvil group to distribute a malicious software update to more than 1,000 MSPs and a number of their customers, flaunting access to the victim networks.
The incident had long-term outcomes as many as 1,500 organizations were hit, some of which were small and medium-sized businesses, government agencies and a source of the nation’s critical infrastructure. REvil asked for $70m worth of Bitcoin as ransom money for a universal decryption key to untie the tangle of encrypted data.
Ransomware attacks of REvil on Kaseya have brought to attention the real danger the ransomware groups pose to the supply chain ecosystem and the need to secure software supply chains against exploitation.
Incident became a call for service providers and organizations to implement adequate security measures, including software updates, network segmentation, data backups, and complete incident response plan to avoid ransomware attacks.
8. CodeCov
The supply-chain attack of CodeCov, discovered in April 2021, revealed the risks of 3rd-party code dependence compromises and increased importance of supply chain security in software development. CodeCov is a widely used code coverage and testing software provider that delivers tools to measure the quality of a developer’s code testing techniques.
Recommended: NIST Supply Chain Security Guidance for CI/CD Environments
In the described exploit, threat actors managed to acquire unauthorized access to CodeCov’s Bash Uploader script, which was originally developed by developers and is used to send the code coverage reports to CodeCov’s servers.
The attackers tweaked the script so that it included a malicious “code chunk” that stole sensitive data, including environment variables, credentials, as well as tokens, from the CI environments of victims. They are usually employed to login to other services like cloud applications and source code platforms, transferring control to the attackers over other systems and information.
The Bash Uploader script tainted by CodeCov has been pushed to its GitHub repo and the package manager repositories that support languages like npm for Node.js projects.
Consequently, many different entities, among them prominent technology companies and government agencies, inadvertently executed the malicious script without realizing its nature as part of their CI/CD pipelines which has subsequently exposed their confidential data to the attackers.
The Codecov supply chain attack had multiple effects on affected organizations such as data breaches, unauthorized access to internal systems and data and reckless harm to reputation.
It was a stark reminder of the need for diligent dependency raking and securing in the software supply chain with as many security control mechanisms as are available to fight and mitigate supply chain attacks.
Common Types of Supply Chain Attacks
The supply chain attacks form a widespread and advanced type of cyber threat that exploits weak points within joint networks of such entities as suppliers, vendors, contractors, and partners.
Such attacks leverage trust relationships and dependencies existing within the supply chain ecosystem to compromise the systems, steal data, or disrupt operations. Here’s a detailed overview of common types of supply chain attacks:
1. Browser-based Attacks
Browser-based attacks rely on vulnerable web browsers or components to attack the devices of the users or to steal their sensitive information.
These attacks take place when users access malicious or compromised websites where the attackers use techniques such as Cross-site Scripting, Cross-site Request Forgery, drive-by downloads, phishing and browser hijacking to perform malicious activities within the victim’s browser.
Attacks against browsers lead to a number of effects such as loss of data, financial frauds, and unauthorized access to systems that contain sensitive information.
DigiCert Software Trust Manager provides a complete service for the management of the risks that browser vulnerabilities impose.
It ensures the integrity and authenticity of software components and updates thus helping organizations defend against browser-based attacks, protect their critical assets & achieve true and effective cybersecurity.
2. Software Attacks
Software supply chain attacks exploit existing software development or distribution vulnerabilities to corrupt the software with malicious code or malware. Adversaries might attack software vendors, package repositories, or software update mechanisms in order to plant malicious updates or packages into users’ systems.
Attacks of this kind can lead to large scale compromise of systems , data breaches and financial losses to the victims.
The SolarWinds supply chain attack and CodeCov supply chain attack are good examples.
3. Open-Source Attacks
The OSS attack vector targets the vulnerabilities inherent to open-source software libraries and frameworks, which are commonly utilized by developers in the process of application development.
Adversaries might craft malicious code or backdoors for widely used open-source projects that will eventually make their way to downstream applications by stealth. This type of attack can jeopardize the security of many applications and systems that use the vulnerable open-source components.
An illustrative example of this is the event-stream npm package incident. By ensuring the integrity and authenticity of open-source components, Code Signing offers a comprehensive solution to protect your organization from open-source attacks.
4. JavaScript Attacks
In JavaScript supply chain attacks, vulnerabilities in JavaScript languages or libraries used in websites and web applications serve as the target.
Attackers can inject malicious JavaScript code into legitimate scripts or take over third-party JavaScript libraries to perform unapproved activities in the users’ browsers. These attacks can end up in data theft, session hijacking or the deployment of additional malware on the websites compromised.
Magecart attacks form a representative example of the JavaScript supply chain attacks.
5. Magecart Attacks
Magecart attacks particular e-commerce websites and online payment systems by inserting malicious JavaScript into web pages, taking card payment information entered by users after checkout.
Criminals exploit flaws of vulnerable websites or 3rd party scripts such as payment processing tools to perform man-in-the-middle attacks and steal sensitive data.
The data is then leveraged for illicit purposes like credit card fraud or identity theft. The Magecart attack examples that involve British Airways and Ticketmaster are particularly famous.
6. Watering Hole Attacks
Watering hole attacks refer to attackers gaining control of websites popular with target individuals or organizations and injecting them with malware. Attackers identify websites with a high level of traffic, like industry-specific forums, online news websites, or social media platforms, and from these sites they insert malicious code.
When the compromised sites are visited by their targeted individuals or organizations, their equipment is prone to attacks by malware that will enable hackers to gain unauthorized access to delicate information of the victims or cause further attacks.
7. Cryptojacking
Crypto Jacking attacks occur in the hijacking of computing resources of a victim, such as the CPU or the GPU cycles, to mine cryptocurrency without their authorization. Hackers can also exploit websites, web browsers, or software applications to remotely install cryptocurrency mining scripts on users’ devices.
These attacks lower the system’s performance, increase power usage, and put user’s integrity at risk resulting only in financial gains for the attackers.
Ways to Prevent Supply Chain Attacks
Preventing supply chain attacks requires a multifaceted approach that addresses vulnerabilities and risks at various stages of the supply chain ecosystem. Here are some key ways to prevent supply chain attacks:
Run a Third-party Risk Assessment
Performing an assessment of third-party risk is one of the key steps in eliminating the risk of potential weaknesses and security risks that may come as a result of engaging external suppliers, vendors, or partners.
It entails a systematic evaluation of the security posture of the third parties to identify and handle any risks that could be brought about by the third parties to the organization’s assets, data, or operations.
The process usually kicks off with finding out all third parties that work with the company’s systems, networks, or sensitive information. After the discovery, the boundary of the assessment is laid, which specifies the types of risks to be assessed and the level of access each third party has within the organization’s environment.
Each Third party undergoes information gathering, covering organization structure, the services delivered, their regulatory compliance commitment, and security practices.
With the acquired information, a risk assessment methodology or framework is developed which identifies the likelihood and impact of the risks.
The results from the review are thereafter used to create risk mitigation plans, revise the contracts, develop maintenance systems for vigilant monitoring and assessment of the third-party security posture.
Through in-depth third-party risk assessment, companies will be able to take proactive measures in dealing with related security risks inclusive of their business partners, hence, build a secure and consistent supply chain ecosystem.
In today’s interconnected digital landscape, third-party risk assessments are essential for safeguarding against supply chain vulnerabilities. DigiCert Software Trust Manager offers a comprehensive solution to mitigate risks associated with third-party software.
By ensuring the integrity and authenticity of software components, DigiCert empowers organizations to proactively manage third-party risks and fortify their cybersecurity defenses.
2. Implement Zero Trust
A Zero Trust approach towards cybersecurity works to validate and authenticate the access, continuous authentication and the provisioning of privileges only to the subjects that really need them so as to reduce the likelihood of unauthorized users accessing the systems and causing data leakage.
This model is based on the principle “Don’t trust, always verify” meaning that the access to the resources and systems, whether its user, device or application, shall only be allowed if the identity and trustworthiness is verified independently of their location and of the network it’s on.
Organizations will implement two-factor authentication methods like MFA and biometrics authentication for user identification in order to achieve Zero Trust.
Adaptive authentication methods should be applied to monitor the user’s behaviors for the purpose of identifying suspicious activities; and challenge-based authentication can be provided going along with it if conditions require.
Least privilege model must be applied for controlling the resource access through the minimum level of privileges needed to accomplish particular functions. The
micro-segmentation method allows the complete separation of the network into a number of segments, which reduces the area of the possible attack and limits the number of breaches.
Both data encryption and data security measures should be applied to the data in rest, as well as communication. Monitoring and analytics is one of the crucial components of the IT security systems, responsible for the real-time logging and analysis of the user actions, detection of anomalous behavior, and prompt reaction in case of security events.
Adopting the Zero Trust approach and principles, the organizations will improve their security practices, manage how the insiders and outsiders can affect the risk, and maintain control over their organization’s digital assets spread through a number of distributed environments.
As cyber threats evolve, implementing Zero Trust architecture becomes paramount for organizations seeking robust cybersecurity.
3. Use Malware Prevention
These cyber threats mitigation actions are of critical importance as staying protected against malware attacks especially in the relation to supply chain security.
Through the implementation of strong malware prevention tactics, the enterprises can decrease the chance of being affected by malicious software such as virus, ransomware, trojans and other malware types.
Among the most important parts of protecting against malware is installing endpoint protection measures that would be antivirus software and endpoint detection and response (EDR) systems which continuously check the files, processes, and network activity to prevent infection from the malware on all connected to the network equipment.
Moreover, companies must implement email security controls like spam filters and antivirus scanning of attachments to prevent malicious attachments and phishing emails to reach users’ inboxes.
Web filtering solutions are also a group of tools which can deny users access to forged websites and URLs with the sole aim of preventing system file or personal accounts from being impacted by downloaded malware deemed to be malicious or systems falling prey to phishing techniques.
A necessary part of patch management and network security controls, such as firewalls and intrusion detection systems (IDS), is regular patching which covers security gaps and detects and thwarts malware infections at the network level.
Behavioral analysis techniques and user education programs complement defensive malware prevention initiatives by identifying and containing previously unknown threats and through educating users in the importance of raising awareness and reporting of the said suspicious activities.
4. Adopt Browser Isolation
Browser isolation is a preventive action by which organizations can strengthen their cybersecurity systems to prevent the occurrence of supply chain attacks. Browser isolation is the process of conducting web browsing activities in a separate, isolated environment so that malicious code is not able to compromise endpoints and critical systems.
Through isolation of web browsing sessions from the underlying operating system and network infrastructure organizations can drastically lower the risk of malware infections, drive-by downloads, and phishing attacks running from compromised or malicious websites.
Browser isolation tools employ sandboxing techniques, virtualization technology, or remote browsing environments to create a secure boundary between web content and the rest of the system, thus preventing any malicious code encountered during the browsing sessions from executing on the endpoint.
Besides that, browser isolation protects sensitive data and credentials from getting intercepted or stolen by malicious actors during web-based attacks. Implementing browser isolation as part of its cybersecurity strategy, an organization can reinforce its defenses against web-based threats and reduce the likelihood of compromise from supply chain attacks.
5. Detect shadow IT
Identifying shadow IT is a crucial part of running effective cybersecurity within organizations, evident in the context of supply chain breaches prevention. Shadow IT is the practice of using unapproved software, applications, or cloud services by employees, without the IT department being aware of this.
Unauthorized tools and services raise serious challenges to the security, since they often have no adequate security controls and there is little or no compliance with corporate guidelines and procedures. To spot shadow IT organizations may apply network traffic analysis, EDR solutions, and CASB tools to track unauthorized usage of cloud services and unapproved software installations.
Through the continuous and real-time monitoring of network traffic along with endpoint activity, organizations can identify unauthorized access to cloud services, abnormal data transfers and suspicious applications usage that would be the cases of shadow IT.
Moreover, establishing user education and awareness programs will create awareness about the risks associated with shadow IT and motivate employees to report any unauthorized software or services to the IT department early enough.
Through the act of monitoring for shadow IT and correcting it, organizations can effectively avert security risks, keep up with legislations requirements and minimize the possibility of supply chain attacks coming from unauthorized or insecure software and services.
6. Enable Patching and Vulnerability Detection
The most important part of a cybersecurity defense strategy is the enabling of patch and detection of vulnerabilities. This is especially critical in the prevention of supply chain attacks. Patching involves regularly fixing weak points in software, programs and operating systems to remove known vulnerabilities, flaws and threats.
Updating systems regularly against the latest security patches reduces the potential for resource exploitation by cybercriminals and protection against successful supply chain attacks.
Implementing vulnerability detection instruments helps entities to discover and deal with potential vulnerabilities that can be acted upon by the attackers even before they are accessed.
This entails utilization of vulnerability scanning tools, automated patch management solutions, and security assessment methods to locate vulnerabilities in software and systems, categorize remediation actions based on the risk level, and deploy security patches at comprehensive and early stages.
Organizations can fortify their defenses against supply chain attacks via patching and vulnerability detection that in turn will lower the risk of compromise of critical assets and data thereby, preserving a secure and stable IT environment.
7. Prevent Zero-day Exploits
Zero-day exploits prevention is one of the main goals for organizations seeking to protect their systems from cyber threats that can be classified as advanced like those offered by today’s supply chain attacks. Zero day exploits are vulnerabilities in software or hardware which affect vendors that have no available patches or fixes in place.
To stop zero-day exploits, businesses should maintain security posture. Starting with installing high-quality endpoint protection solutions that are equipped with heuristic and behavior-based detection capabilities, one can succeed in identifying and blocking zero-day malware and exploits in real-time.
Furthermore, IDS/IPS systems can detect zero-day attacks through early detection of suspicious activities and strangeness of its behavior related to network attack.
Applying whitelisting and least privilege access control can reduce the target of an attack and minimize the impact of zero-day vulnerabilities through restricting unauthorized software execution and user privileges.
What is more, to keep abreast of new and zero-day threats, organizations must continually adjust their security controls and response strategies by means of threat intelligence feeds and security advisories.
Good implementation of these preventive measures along with the existing proactive security posture can help organizations in averting zero day exploits as well as ensuring resilience against supply chain attacks and other advanced threats.
Best Practices to Protect Against Supply Chain Attacks
-> Mitigating supply chain attacks needs a comprehensive strategy of prudence in most of the security facets. One critical activity is implementing strong and effective vendor risk management processes, performing detailed checks and audits to determine the security posture of third-party suppliers, vendors, and partners.
-> It is critical to ensure integrity of software like secure software development practices help achieve it through digital signatures and cryptographic hashes. Frequent monitoring and detection mechanisms are required for real-time identification and response to supply chain security events, while employee education programs contribute much to the overall cyber hygiene.
-> Ensuring incident response planning, regulatory compliance adherence, and extending security controls to every feature of the supply chain ecosystem are the same priority. In addition, facilitating collaboration and knowledge exchange within trusted networks leads to the creation of situational awareness around emergent threats and vulnerabilities.
By adhering to these best practices, companies will be able to reinforce their defenses against supply chain attacks, in this way risks will be minimized, thus important assets, data, and operations will be protected.
In the ever-evolving landscape of cybersecurity, protecting against supply chain attacks requires a proactive and comprehensive approach.
By ensuring the integrity and authenticity of software components, DigiCert empowers organizations to mitigate the risks associated with supply chain attacks effectively.
Conclusion
Preventing supply chain assaults should be a prerequisite for the organizations interested in protecting their assets, information and operations from the continuously developing cyber threat environment.
As outlined in this article, ensuring cybersecurity practices like vendor risk management, secure software development, and continuous monitoring are held robustly would go a long way in mitigating threats emanating from the supply chain.
DigiCert Software Trust Manager leverages advanced cryptographic methods, code signing, and secure code execution mechanisms to ensure the end-to-end integrity, authenticity, and trustworthiness of software from initial deployment to the end of life.
Organizations can check the digital signature of software publishers, determine the integrity of software updates, and ensure compliance to security policies using fine-grained control over the software supply chain.
Frequently Asked Questions
1. What is the most famous supply chain attack?
The SolarWinds supply chain attack belongs to the well-known incidents of this decade. This smart cyberattack tackled the software supply chain at its core, infecting thousands of companies all over the world with corrupted software updates, underscoring the acknowledged widespread risk that supply chain flaws pose.
2. What is an example of a software attack?
An example of a software attack is the NotPetya ransomware outbreak in 2017. Petya infection started with a compromise of an update to the popular Ukrainian accounting software called M.E.Doc. Around the world, thousands of systems were maliciously infected and data was encrypted, rendering the systems thus unusable. The NotPetya attack resulted in huge financial loss and other disruption in many organizations from all industries.
3. How common are supply chain attacks?
Attacks targeting supply chains are growing in frequency, and they are a serious threat against many organizations across industries. These attacks are made possible by the software supply chain vulnerabilities leading to the actualization of advanced cyberattacks through infiltrations into systems.

