What is a Malicious Code? How Can an Organization Protect Against Malicious Code?

In today’s digital era, billions of online data and information are processed on the web. Individuals, businesses and organizations actively rely on the web network.
With such huge reliance on the digital network, it is evident that malicious code poses a high risk to the systems and information processed. There are many types of malicious code, trojans and viruses that affect the networking system across the globe.
Did you know? Over 5,60,000 pieces of various malicious malware are detected daily. Moreover, over 58% of Trojans account for computer network malware.
While it is astonishing to know that there are about 1 billion malware programs across the globe. This makes malware a major threat to businesses and organizations.
However, malicious code, often called malware, encompasses a variety of harmful software designed to compromise the security of computer systems, steal sensitive information, or disrupt normal operations.
This article will briefly make you understand what malicious code is, signing certificate code how organizations can protect against these malicious codes and much more.
What is a Malicious Code?

Simply put, malicious code refers to a category of online software applications or code scripts made to cause harm or destruction to the operation of a computer system. This includes a variety of perilous elements, including trojans, ransomware, viruses, spyware, and other tools crafted with malicious intent.
The main aim behind developing and distributing these malicious codes can vary, ranging from financial profit and data theft to political or ideological agenda.
In other words, malicious code can cause various problems, such as deleting or encrypting sensitive files, leaking or stealing crucial information, redirecting web traffic, displaying irrelevant ads, installing backdoors, capturing keystrokes, or taking control of the system.
How Can an Organization Protect Against Malicious Code?
Mitigating the serious threat posed by malicious code to computer systems and data involves adopting various preventive measures. Organizations can boost their defense against such threats by applying these prevention techniques:
Be Careful with Links and Attachments:
Ensure you are vigilant when interacting with links and attachments in emails, social media, and websites. Clicking on seemingly legitimate links or opening attachments can unintentionally attract malicious code.
Install Antivirus Software:
Make sure you have a trusted antivirus software and ensure it is regularly updated. This software plays a crucial role in detecting and eliminating malicious code from both individual computers and network environments.
Use Code Signing Certificates:
It is important for software publishers and distributors to use code signing certificate to sign their code digitally to verify and boost code integrity. This digital signature ensures the authenticity of downloaded or executed code, assuring users that it has not been tampered with by malicious agents.
Limit Permissions for Web Browsing:
Accounts in use should have restricted permissions while browsing the web to minimize the potential impact of malicious code exploiting vulnerabilities. This practice limits access to administrative privileges, curbing the spread and damage caused by such code.
Block Pop-Ups:
Avoid the risk associated with malicious code in pop-up ads by using pop-up blockers in web browsers. This measure helps prevent the automatic execution of code when users interact with pop-up advertisements.
Regularly Change and Strengthen Passwords:
Protect against password-related threats by changing passwords regularly and adopting strong, unique combinations. This practice mitigates the risk of malicious code stealing or cracking passwords for unauthorized access.
Use Firewalls and VPNs:
Having good firewalls and virtual private networks (VPNs) enhances network security. Firewalls block unauthorized or suspicious network traffic, while VPNs encrypt online activity, protecting against malicious code attempts.
Backup Data Files:
Regularly back up critical data to ensure that organizations can restore their systems and minimize the impact in case of ransomware attack or data loss. This can help mitigate the huge impact of the compromised file by malicious codes.
Implement Network Security Measures:
Strengthen network defenses against malware by employing firewalls, network segmentation, email filtering, and encryption. These measures restrict or block access by malicious code to both the network and connected devices.
How Can You Avoid Downloading Malicious Code?
It is important to know and learn how to avoid downloading malicious codes on your computer systems.
Here are a few crucial points to consider avoiding malicious codes from being downloaded into your systems.
- Avoid downloading files from unsecure or public Wi-Fi networks. Public networks can be more vulnerable to malicious activities, and downloading files in such environments increases the risk of exposure to harmful code.
- Verify the legitimacy of download sources. Use official websites, reputable app stores, or trusted vendors to download software, avoiding third-party sites that may host compromised or fake applications.
- Avoid clicking on links in emails, pop-ups, or websites that appear suspicious or redirect to unfamiliar domains. Malicious code can be hidden behind these harmless links.
- Be aware of social digital tactics used to trick users into downloading malicious code. Take precautions with unsolicited messages, enticing offers, or requests for personal information.
Recommended: Top 10 Security Tips to Prevent Downloading Malicious Code or Data
Types of Malicious Code
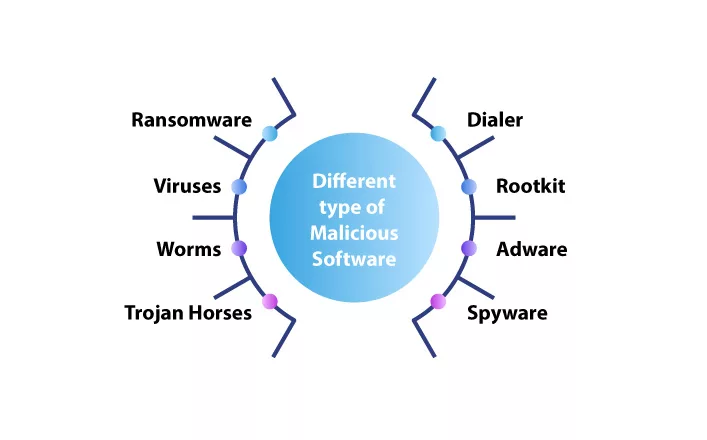
Here are the various types of malicious codes that can harm your computer and network systems.
Worms:
Worms are self-replicating code that spreads across networks without requiring user interaction. They exploit vulnerabilities in network protocols and operating systems to propagate often causing widespread damage by using network bandwidth and system resources.
Viruses:
Viruses are malicious programs that attach themselves to crucial files and replicate when those files are executed. They can spread through infected files, removable media, and network connections, causing damage to files and systems.
Ransomware:
Ransomware encrypts files on the targeted system, making them inaccessible. The attacker then demands financial gain in exchange for the decryption key. This type of malicious code like ransomware is majorly created in high-profile attacks on individuals, businesses, and critical infrastructure like financial or govt. entity.
Trojans:
Trojans hide and showcase themselves as authentic software to trick users into installing them. Once installed, they create backend attacks for attackers, allowing unauthorized access to the infected system. Trojans are used for various malicious purposes like data theft and system manipulation.
Adware:
Adware shows irrelevant advertisements on a user’s system. While it may not always be risky, adware can destroy and compromise network system performance. In many cases, it can lead to a heavier online security breach.
Spyware:
Spyware is created in such a way that it gathers sensitive information about end-user activity without them having an idea about it. It monitors keystrokes, captures screenshots, and collects sensitive information like card details, addresses etc, posing a serious threat to user privacy.
What Are the Sources of Malicious Codes?
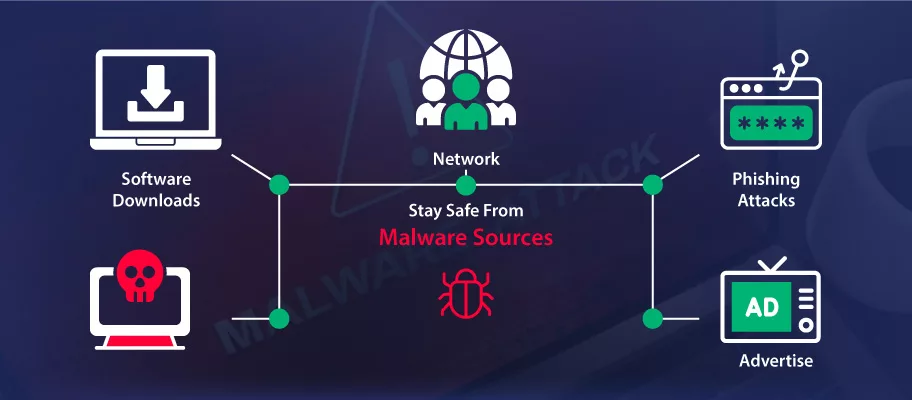
Malicious code can originate from various sources. It is important to keep a watch on such sources through the measures given below.
Here are some of the common sources of malicious code:
Untrusted Websites
Visiting untrusted websites can expose users to downloading risky files, where malicious code is executed without user consent.
Infected External Devices
Removable media such as USB drives or external hard drives can carry malicious code from one system to another.
Compromised Software Application
Software vulnerabilities can be exploited by attackers to integrate malicious code into authentic applications, compromising the security of the software and the systems on which it runs.
Email Phishing Attachments and Links
Phishing emails often contain malicious attachments or links and when clicked, can download, and start malicious code attacks on the user’s system.
Recommended: Best Safe Download Checker Tools to Protect Your Devices from Threats
Conclusion
Having briefly explained various parameters of malicious code, we can now understand that securing against the use of threats and suspicious downloads of malicious code is paramount for ensuring the security of digital network systems.
By taking the best industry approach and practices, individuals, businesses, and organizations can significantly reduce the risk of falling victim to such malicious cyber code threats.
Verifying download sources, maintaining up-to-date security software, and exercising caution with email attachments and suspicious links are fundamental steps in this regard.

