What is HashiCorp Vault and How Does it Work?

With technological advancements, organizations are moving to the public cloud, which has resulted in a major concern: data security.
Traditional methods of managing secrets and sensitive information are proving inadequate, especially when there is a high volume of private data.
Here comes the need for HashiCorp Vault: a solution that offers a centralized and robust system to safeguard sensitive information.
In this blog, we will explore HashiCorp Vault’s purpose, benefits, and use cases.
What is HashiCorp Vault?
HashiCorp Vault is a powerful tool that helps businesses securely store and manage secrets (such as API encryption keys, passwords, and certificates) in modern computing environments.
Before providing access to secrets or stored sensitive data, it validates and authorizes clients (users, machines, apps). (as shown below)
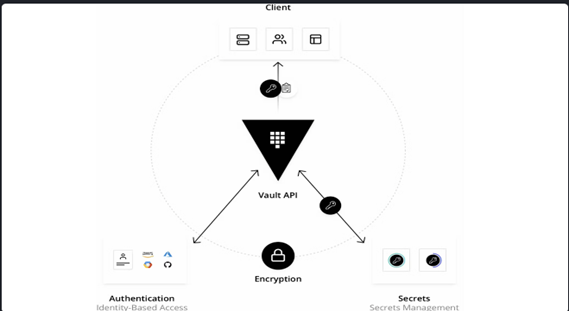
What Can I Do With It?
HashiCorp Vault offers a wide range of capabilities that can address various security and secrets management needs within an organization.
Keep reading to know more about this!
Features and Benefits of HashiCorp Vault
Below are some of the features of HashiCorp Vault.
Data Encryption:
It provides encryption as a service to encrypt and decrypt data without storing it in Vault. This simplifies the management of encryption keys and majorly proves useful for applications that can’t handle the intricacies of key management.
Identity-based Access Management:
HashiCorp Vault offers a range of methods for users and applications to verify their identity, such as using tokens, username/password combinations, or integrating with cloud IAM. Once authenticated, it uses policies to determine the level of access each user or application has to specific secrets.
Revocation:
Vault supports secret revocation. What does this mean? You can revoke secrets before lease expiry, whether they’re a single secret or a “tree of secrets.”
For instance, if a specific user or application is compromised, it will quickly invalidate all the secrets that were accessed by that user or application.
Authorization:
Vault offers various authentication methods, such as GitHub, LDAP, and AppRole, each serving specific purposes. These methods verify clients’ identities before they can access Vault. Once authenticated, it generates a token, which serves as proof of the client’s identity and grants access to the requested secrets or operations.
Centralization of Secrets:
To ensure all your secrets are up to date and secure, Vault provides a central point through which you can manage and update Secrets across multiple environments.
Audit Log:
Vault keeps thorough records of every access and modification made within its system. These logs are essential for conducting security audits and ensuring compliance with regulations and standards.
Secure Storage of Secrets:
Vault securely stores your sensitive information, like passwords and keys, by encrypting them before saving. This ensures that even if an individual tries to access the storage directly, your secrets stay safe.
How Does Vault Work?
Vault primarily works with tokens that are associated with the client’s policy. Each policy, structured around paths, dictates the actions and access levels permitted for each client.
Vault’s core workflow can be broken down into four key stages, as explained below.
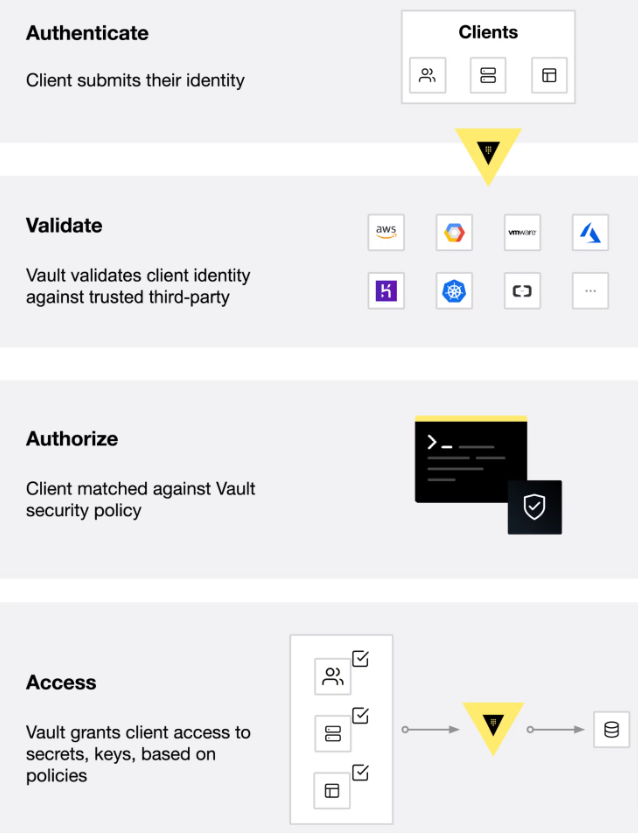
- Authentication: This is the initial step where the client provides information that Vault further uses to verify their identity. After authentication is done through an aun method, it generates a token and associates it with a policy.
- Validation: Vault validates the client’s identity against trusted sources such as GitHub, LDAP, or AppRole to ensure that only authorized clients are given access.
- Authorization: Next, Vault matches the client against its security policy. These are sets of rules that define which API endpoints a client can access with its Vault token.
- Access: Finally, Vault grants access to secrets, keys, and encryption capabilities by issuing a token based on the policies associated with the client’s identity. This token can then be used by the client for subsequent operations within Vault.
Why Do We Need Secrets Vaults?
Secrets vaults serve as highly secure repositories for storing critical information about a company’s operations. They go beyond basic usernames and passwords, encompassing a range of sensitive data such as cryptographic keys, tokens, and certificates – collectively referred to as “secrets.”
Traditional methods of managing these secrets are both risky and inefficient. That’s why organizations are switching to secret vaults. Reason?
- Vaults provide a centralized and highly secure environment for managing and safeguarding sensitive information.
- They can also be integrated with other systems and tools for seamless automation of processes.
- These help organizations monitor and control access to their secrets effectively.
- Secrets vaults offer advanced security features such as password rotation and the removal of unnecessary privileges.
Use Cases of HashiCorp Vault
Here are some of the use cases of HashiCorp Vault.
General Secret Storage
Vault securely stores sensitive information like passwords and encryption keys. It ensures that only authorized individuals can access this information, reducing the risk of data breaches.
Static Secrets:
These secrets are long-lived and static and are not changed frequently. For example, the passwords used to access the database can be stored in Vault because they remain unchanged for a long period of time.
Dynamic Secrets:
Dynamic secrets are generated on-demand and are unique to every client. These credentials are created for specific tasks and automatically expire after a defined period.
Data Encryption
Organizations deal with two types of data, i.e., data at rest and data in transit.
What exactly does these terms mean?
Data at rest is stored in a particular location and is not transferred or accessed, e.g., hard drive or database. On the other hand, data in transit is actively transferred between devices or networks.
HashiCorp Vault encrypts both data at rest and in transit against unauthorized data breaches. Here’s how!
When data is stored in Vault, it undergoes encryption. This process essentially scrambles the data, adding an extra layer of security. So, even if someone unauthorized tries to access it, they won’t be able to make sense of it. (Below is the graphical representation)
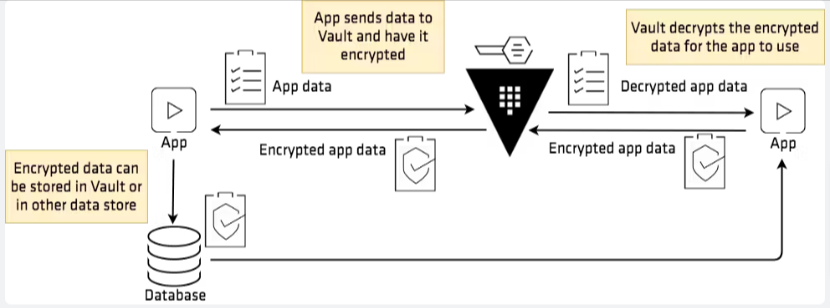
Key Management
Vault’s Key Management Secrets Engine provides a streamlined process for distributing and managing encryption keys across various cloud providers.
With Vault, organizations can centralize control over their keys while still benefiting from the cryptographic capabilities offered by their chosen KMS providers.
Recommended: Azure Key Vault vs HashiCorp Vault: Comparison
In a nutshell, HashiCorp Vault maintains a high level of security and ensures a high level of confidentiality and integrity of data across cloud environments.
Identity-Based Access
As organizations use more and more different cloud services and systems, they run into a problem called “identity sprawl.” This means there are lots of different ways for people to prove who they are across all these different systems. Managing all these things can be very hectic.
But not any more with HashiCorp Vault!
It uses different authentication methods to verify users and integrates all those different ways of proving identity into one system. This way, organizations can use any trusted resource identity to regulate and manage system and application access.
Now, let’s see how some of the big companies, including Yahoo and Wix, are making the most of HashiCorp Vault.
Yahoo has over 80 million users and is one of the biggest informational websites in Japan. As their users grew, so did the need to securely manage various keys and credentials across multiple data centers.
Instead of building their own secret management system, which would take a long time, they looked for a ready-made solution and chose HashiCorp Vault. Why?
Because it can handle several requests without crashing and works seamlessly with Hardware Security Modules (HSMs).
Outcome of this Collaboration:
- Compared to the previous key management systems, Yahoo now achieved higher safety and functionality.
- The system was delivered and developed much quicker.
Wix, a popular website-building platform, runs lots of Vault instances to keep their secrets secure. Whenever a new version of Vault comes out, it’s a big job to update all those systems. But Wix didn’t want to interrupt their website services while doing upgrades.
To address this issue, Wix implemented a Continuous Deployment (CD) pipeline that automates the upgrade process for all Vault clusters. As HashiCorp Vault can have multiple instances work in parallel, this approach enables seamless upgrades without disrupting website services.
Conclusion
In conclusion, HashiCorp Vault is a powerful solution for securely managing secrets and sensitive data. By providing a centralized platform for secrets management, encryption, access control, and dynamic secrets generation, it helps organizations enhance their security posture and comply with regulatory requirements.

