What is a Hardware Security Module? Role of HSMs for Digital Signing
HSMs for Digital Signing: How is it Done?
Imagine signing an important digital document, only to realize that your signature has been compromised and your sensitive information is now at risk. Scary, right? That’s where Hardware Security Modules (HSMs) come in!
They are the unsung heroes of digital security, ensuring that your digital signatures remain safe and secure.
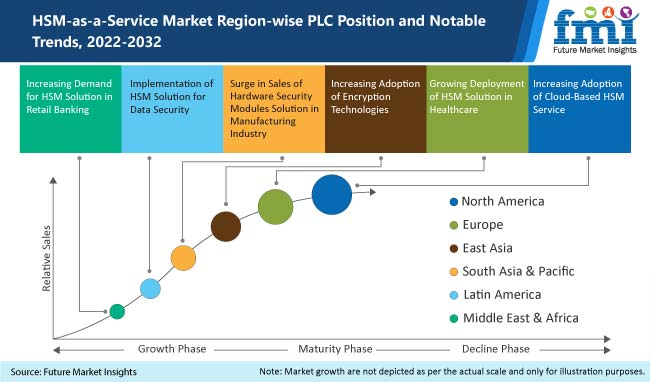
According to a study, the market is expected to reach US$ 1,667.4 Mn by 2032, exhibiting growth at 14.3% CAGR between 2022 and 2032.
But what is it? Let’s find out and understand its application in digital signing.
Hardware Security Module: Explanation
Let’s say you are running an online store that accepts credit card payments from customers. However, to accept payments, SSL certificates are required to encrypt all the payment information and digital signatures to authenticate the transaction.
To generate and manage these digital certificates and signatures securely, you can use an HSM. It is a specialized hardware device that is designed to provide secure storage and management of digital keys and sensitive data.
So when a customer makes a payment on your website, their payment information is encrypted using the digital certificate and transmitted to your payment processor. The payment processor then verifies the authenticity of the transaction using the digital signature generated by the HSM.
Without an HSM, the private keys used to generate these digital certificates and signatures would be vulnerable to theft or tampering, potentially exposing sensitive payment information to malicious actors. But with an HSM, you can rest assured that your customer’s payment information is safe and secure.
How Do HSMs Works to Keep Your Data Safe?
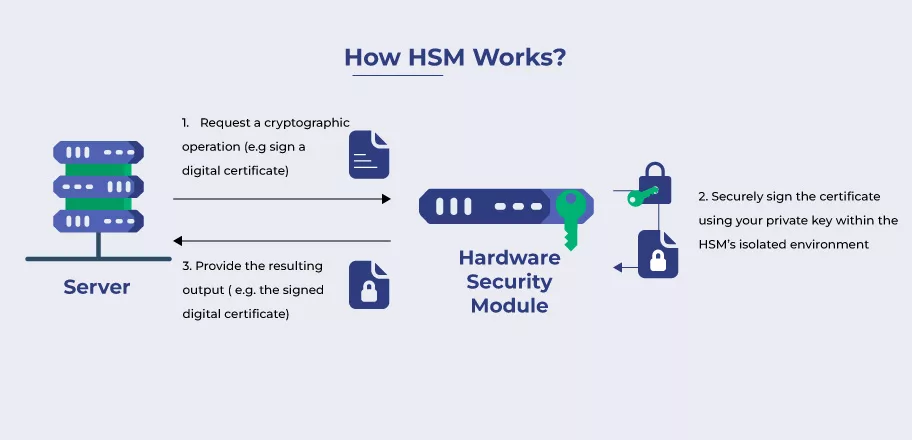
HSMs play a key role in actively managing the lifecycle of cryptographic keys as it provides a secure setting for creating, storing, deploying, managing, archiving, and discarding cryptographic keys.
These are the series of processes that take place for HSM functioning.
- The first step is provisioning. HSMs use a true random number generator to create keys, ensuring their uniqueness and unpredictability.
- Once created, a copy of the key is made and securely stored. This is done for times when the original key gets compromised. Note that before being stored, HSM makes sure that the private keys are encrypted.
- The next step is deployment. In this, the key is installed in HSM, ensuring that the key is only accessible by authorized personnel.
- HSMs provide a range of management functions to in iOS and an organization’s internal policies. Key rotation is a critical function as the process involves deployment of new keys on the expiry of old ones.
- Archiving is the process of decommissioning keys and storing them offline in long-term storage. This helps in accessing the old data that was encrypted with that key.
- The final phase of a key’s life cycle, disposal, involves securely destroying the key once it has been established that it is no longer required.
Types of HSMs:
The usage of Hardware Security Modules (HSMs) is growing in popularity as a means of securing sensitive data. HSMs are an excellent option for any corporation wishing to safeguard its data further since they offer an extra layer of security for storing and processing sensitive data.
There are two types of HSM:
- Payment and Transaction HSMs
- General-purpose HSMs
General-Purpose HSM:
The most popular HSMs are general-purpose ones, which work best for crypto wallets, public key infrastructures, and other kinds of sensitive data. These HSMs offer PKCS#11, CAPI, and CNG encryption methods.
General-purpose HSMs are used in a number of applications, including SSL/TLS, VPN, PKI, and database encryption. They are made to handle a broad range of cryptographic operations. They are frequently employed by businesses and government organizations that need strong cryptographic protection because they provide high security.
Payment and Transaction HSM:
Payment and transaction HSMs are made primarily to safeguard sensitive transaction data like credit card numbers. For sensitive data that is sent or kept in a payment system, they provide an additional degree of protection.
HSMs can successfully safeguard the private data you care about, whether you’re trying to secure your personal data or give customers a secure platform. Finding the optimal solution for your needs begins with understanding the many types of HSMs that are now available.
On the other hand, payment HSMs are meant to safeguard cardholder data during transactions and are particularly created for the payment sector.
They support payment protocols like ISO 8583 and APACS and are in accordance with industry standards like PCI-DSS and EMV. Banks, financial institutions, and payment processors utilize payment HSMs to guard against fraud and guarantee the reliability of electronic transactions.
Difference Between 2 Major HSMs:
Let us have a look at the comparison table of General Purpose HSMs and Payment HSMs:
| FEATURES | GENERAL PURPOSE HSMs | PAYMENT HSMs |
| Applications | SSL/TLS, VPN, PKI, database encryption, and other general-purpose cryptographic services | Securing cardholder data during electronic transactions |
| Standards Compliance | Compliant with general industry standards such as FIPS, Common Criteria, and HIPAA | Compliant with industry-specific standards such as PCI-DSS and EMV |
| Security Features | Robust cryptographic protection, secure key storage, and secure key management | Secure storage and management of encryption keys, secure transaction processing, and tamper evidence |
| Cost | General Purpose HSMs are typically more expensive than Payment HSMs | Payment HSMs generally have lower costs due to their limited application scope |
| Performance | General Purpose HSMs typically have a higher performance due to their broader application scope | Payment HSMs have a lower performance due to the need for transaction processing and compliance with specific industry standards |
What are the Advantages of HSM?
Hardware security modules (HSMs) offer enterprises safe cryptographic key storage and automated cryptographic key lifecycle duties. Using HSM, companies may ensure that their sensitive data and cryptographic keys are secure, protected, and impossible to mess with.
Additionally, they give high levels of trust and authentication and adhere to tight security rules and requirements.
HSMs offer a number of benefits, including the following:
Enhanced Security:
For cryptographic activities, HSMs offer a high level of security. They provide secure key distribution, key creation, and key storage and administration. This lowers the possibility of unwanted access to private data and aids in preventing data breaches.
Compliance:
HSMs are made to adhere to a number of industry and governmental requirements. Organizations find it simpler to comply with regulations and avoid fines as a result.
High Performance:
HSMs are built to handle enormous amounts of data fast and efficiently during high-performance cryptographic processes. For applications that require low-latency encryption and decryption, this is crucial.
Scalability:
HSMs are easily expandable to accommodate the requirements of expanding companies. As a result, businesses may grow without compromising on performance or security.
Centralized Management:
HSMs may be centrally controlled, which makes it simpler for businesses to handle cryptographic keys and restrict access to critical data.
Recommended: What is a Cloud Hardware Security Module? How to Choose the Right Cloud HSM?
Cost-Effectiveness:
Over time, HSMs can save money since they lower the risk of data breaches and fines for non-compliance. Additionally, they assist businesses in avoiding the expense of maintaining their own cryptographic infrastructure.
Features of HSM that Empower Security Infrastructure
Here are some key features of HSMs that make them an ideal choice for securing sensitive data:
Tamper-Resistance
HSMs are designed to be physically tamper-resistant, with advanced measures such as tamper-evident seals, sensors, and shields. This ensures that the HSM cannot be easily breached, even in the event of a physical attack.
Cryptographic Protection
HSMs provide strong cryptographic protection for the keys and data stored within them. They use advanced algorithms and protocols to encrypt and protect sensitive information from unauthorized access.
Key Management
HSMs offer a robust and secure environment for key management, ensuring that keys are generated, stored, and used in a secure manner. They also provide key backup and recovery services, making it easier to recover lost or compromised keys.
Recommended: Azure Key Vault: Key Management and Difference
Digital Signing
HSMs are commonly used for digital signing, providing a secure environment for generating and storing digital signatures. This ensures the authenticity and integrity of digital documents, protecting against fraud and tampering.
Compliance
HSMs are designed to meet stringent security standards and comply with industry regulations such as PCI DSS, HIPAA, and FIPS 140-2. This ensures that organizations can meet their compliance requirements and protect sensitive data from breaches.
What is Digital Signing, and How Does HSM Help in Doing it?
A unique code created by a cryptographic technique and associated with a document is referred to as a digital signature. This ensures that any alterations to the document will be recognized. Therefore, a user’s digital signature verifies a document’s integrity and authenticity.
Digital Signature is a critical aspect of securing sensitive documents, such as legal contracts, financial transactions, medical information, and other confidential data.
So how does HSM play a role in it?
When a user initiates a digital signing process, the HSM generates a unique digital signature using the private key stored within the device. The private key is kept securely within the HSM and is inaccessible to anyone except the authorized user.
This ensures that the digital signature is tamper-proof and cannot be altered or compromised by cybercriminals.
Best Practices or Key Points While Using HSM
HSMs (Hardware Security Modules) are crucial for securing your private PKI and other sensitive data. These hardware-based solutions offer better security than software and may be used to manage authentication artifacts, store encryption keys, and carry out cryptographic operations.
When utilizing HSMs, it’s important to have the following in mind:
Make Sure to Add HSMs to your own PKI right now:
This gives you more control over authentication and encryption procedures and enables you to store all of your private keys and digital certificates safely.
Encrypt Keys:
For further security, encrypt extractable encryption keys. As a result, even if an attacker were to access the HSM, they would not be able to access the keys or the data they guard.
Improve the Security:
Safeguard your authentication artifacts and procedures. HSMs can be used to manage the authentication process, store user credentials, and encrypt keystroke data.
Recommended: What is AWS CloudHSM? Everything to Know About
Use an MPKI:
You can try using an MPKI product or service with a built-in HSM. This will provide you the ability to offload cryptographic activities, manage authentication procedures, and securely store your digital certificates.
Boost Server Performance:
Doing this by outsourcing cryptography. You may provide an HSM with the labor-intensive tasks associated with encryption, decryption, key generation, and digital signatures by employing an HSM.
In general, you must maintain HSM security for them to be successful. Use encryption keys that are only available through the HSM, keep the HSM in a secure location, and check for updates on a regular basis.
By adhering to these fundamental guidelines and recommendations, you can ensure that your HSM is used most effectively.
How HSMs Improve IT and Data Security?
HSMs are a valuable asset in enhancing IT and data security. They offer a secure and scalable solution for managing cryptographic keys and protecting sensitive information, making them an essential component of any comprehensive security strategy.
Secure Environment for Cryptographic Key Storage
HSMs offer a secure environment for storing and managing cryptographic keys, which is one of their main benefits. Unlike software-based key storage, HSMs ensure that keys are not accessible to unauthorized users, even if the system is compromised. This feature is critical in securing sensitive information, such as financial transactions, personal data, and intellectual property.
Vast Variety of Security Features
HSMs offer a range of security features, such as digital signing, data encryption, and secure boot. These capabilities help enterprises to defend their IT systems and data from a wide range of security threats, including malware, phishing, and data breaches.
Compliance with Industry-Standard Cryptographic Algorithm
Moreover, HSMs support industry-standard cryptographic algorithms, such as AES, RSA, and ECC, making them compatible with a wide range of IT systems and applications. This compatibility enables organizations to implement a robust security infrastructure without disrupting their existing IT ecosystem.
Scalability
HSMs also offer scalability, which is critical in today’s fast-paced digital environment. Organizations can easily add or remove HSMs to meet their changing security needs without impacting their overall IT infrastructure.
Recommended: EV Code Signing without Hardware Token – Is It Possible?
Hardware Security Modules vs Trusted Platform Modules: Difference
There are several similarities between Hardware Security Modules (HSM) and Trusted Platform Modules (TPM). Both are specialized hardware components that safeguard information and services across international networks.
Both products use tamper-resistant features to safeguard their integrity while providing a hardware root of trust, which is a safe foundation for authentication, code signing, and encryption. However, there are several significant distinctions between HSMs and TPMs.
TPMs are often built into individual devices and are unique to a given system or device. HSMs, on the other hand, are external devices with more flexibility and scalability that may be utilized across applications. HSMs are able to handle tasks requiring greater encryption levels and provide bulk data encryption and decryption.
In other words, HSMs are external devices with broader uses for managing network activities, including many devices and applications.
TPMs are essentially computer chips that are physically attached to the motherboards of specific devices to safeguard their PKI keys and keep them apart from the CPU memory of the devices. They support maintaining the integrity of the device and offer an isolated setting for the device’s cryptographic processes.
HSMs, on the contrary, are hardware components that multiple systems may use. They are designed to be used at scale by servers and apps throughout your company.
So, consider your operations’ scalability, adaptability, and security requirements when deciding between a Hardware Security Module and a Trusted Platform Module for your purposes. An HSM is the best option for most enterprises to guarantee secure operations.
Final Words
When we talk about modern IT security infrastructure, Hardware Security Modules have become an essential part of it as they provide a secure environment for managing cryptographic keys. Also, they offer a range of security features to protect data and systems from threats and support industry-standard cryptographic algorithms.
HSMs are scalable, compatible with existing IT systems and applications, and offer a tamper-resistant solution for securing sensitive information.
As organizations face increasing cybersecurity threats, HSMs are becoming a necessary investment to protect against breaches, unauthorized access, and data theft.
By leveraging the benefits of HSMs, organizations can confidently secure their data and IT systems, ensuring business continuity and maintaining the trust of their customers.
Hardware Token is a lead component, as an organization doesn’t sign the software without it. Use EV Code Signing Certificate, as the Token aids in maintaining security and performing core operations.
