Identify Malicious Code: Examples to Defend Your SDLC

What is Malicious Code?
A malicious code, commonly known as malware is simply a software created to harm computer systems and applications, make changes to networks, and the victim completely unaware.
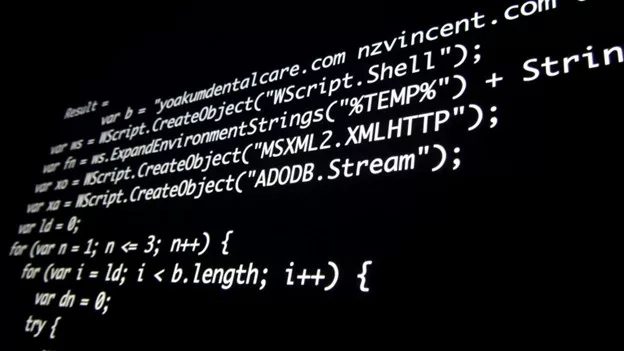
Unlike accidental security flaws and applications’ configuration failures, which are occurring because of irrelevant mistakes like coding mistakes or other mistakes during development activities, deliberate code is purposely designed in order to cause some harm.
Recommended: What is a Malicious Code? How Can an Organization Protect Against Malicious Code?
Hence, malware can enter the life cycle of software development (SDLC) through many ways, such as contaminated dependencies, the environment providing compromise, social engineering activities, software supply chain attacks or the exploitation of zero-day vulnerabilities.
What does Malicious Code look like? How to Identify Malicious Code?
The malicious code detection involves vigilance, keenness and many security tools & techniques employed together. You should keep the following points in mind while identifying malicious codes:
1. Unusual Behavior
Whatever unusual behavior might appear from the system such as the sudden performance drop, frequent crashes, system reboot or unusual system changes as well as messages popping out and error messages should not be ignored. With any of the symptoms below, you could find the device having the malware on it.
2. Strange Files or Processes
Monitor your system often for the presence of unidentifiable files and processes undermining the system. Monitor the processes currently active and their resource use by using processes manager and other system monitoring tools.
Attempt searching for any computer tasks that are named suspiciously, or are marked with an unusual file extension, and are found in system directories or temporary files. Check whether the objects that raise suspicion possess honest digital signatures or belong to the well-known legitimate software.
3. Antivirus Alerts
Be sure to run current and updated antivirus scans of your system on a regular basis. Pay attention to the messages generated by your antivirus, such as warnings and notifications. Be proactive in isolating or blocking whoever out of those who is identified.
Remember that some sophisticated malware may try to turn off or bypass security software this way so using anti-virus along with additional safety measures is a good idea.
4. Unsolicited Downloads
Try to avoid unintended downloads or installs, especially if they are initiated by nefarious-looking websites, or suspicious links in emails, or peer-to-peer networks. Don’t fall for suspicious links and files from dubious senders, instead try to use sources from trusted centers.
Recommended: Top 10 Security Tips to Prevent Downloading Malicious Code or Data
5. Phishing Attempts
Watch out for phishing mails, messages, or websites that expect you to access your financial, personal or business information or malicious files. Ensure the validity of any information or instruction transmitted through any channel before taking action.
How to Prevent and Mitigate a Malicious Code?
Malicious software prevention and minimization are not only a defensive, but also proactive steps by means of a cybersecurity that includes some preventive measures and familiar security practices.
Here are some strategies to help prevent and mitigate the impact of malicious code:
Install and Maintain Antivirus Software:
Put established and credited antivirus software on all devices and do remember to update them with the most recent virus definitions regularly.
Antivirus software being able to detect and remove many types of malware acts as a very strong layer of prevention of malware from getting into the certain system.
Keep Software Up-to-Date:
Pursue the latest security patches and updates for the operating systems, applications, and software.
The developers quite frequently upload software updates that contain the features capable of fixing the existing vulnerabilities which are utilized by the malware to explore systems.
Exercise Caution with Email Attachments and Links:
Be careful with email attachments or with link clicking, especially when you do not know you should click or open them.
Vicious codes can be transmitted by the phishing emails that have infected documents and inactive links to fraudulent websites.
Enable Firewalls:
Implement the use of firewalls on network devices and endpoints to block internet communication to and from computers.
Firewalls can use processes of preventing/rejecting unauthorized attempts and also stop malicious code from communicating with remote servers.
Malicious Code Examples to Defend Your SDLC
Backdoors
A backdoor is the way of bypassing the authentication procedure (usually) by deploying a core entry point to networks, software or systems, launched by malicious intruders to break into a computer. It is imperceptible to the authorized users but helps an unauthorized person get more access rights.
They present major security issues to intended machines and even an attempt to such tries have to be made rigorous analysis to assess the state of danger and react against exploitation as soon as possible.
The mechanism of a backdoor comprises a multi-stage procedure that involves a malicious adding of stealthy features or flaws into software products, systems, or networks.
This unauthorized entry point is commonly installed by developers either intentionally or through hacking and manipulation by external actors during the producing or sending process.
if user == "admin" and password == "password123":
grant_admin_access()According to the code snippet, the backdoor is quite primitive. It confirms if the username is “admin” and password is “password123”. When the conditions are fulfilled then it permits administrative access without a proper authorization.
Cross-Site Scripting (XSS) Attacks
Cross-Site Scripting (XSS) is a malicious practice, which involves taking advantage of trusting websites in order to inject harmful JavaScript code into pages which are sent to the users. When this illicit code is run in the user’s browser, then the attacker gets the right to control how the user interacts with the application.
The results are vast and horrendous for XSS attacks. They may lead to data theft, session hijacking or unauthorized access of sensitive data.
In addition, these hacks destroy the faith of users in the websites attacked, injure the reputation of web applications and they may even lead to legal consequences according to the GDPR (General Protection Regulation) and CCPA (California Consumer Privacy Act).
<script>
alert('Hello, this is a malicious script!');
</script>This is a malicious JavaScript script that contains the following lines that make the malicious script used to get an alert box displayed by getting “Hello, this is a malicious script!” observed:
It shows by the way of such an ordinary example how an XSS attack works, when it is used to take away the security of website users on not sufficiently protected web-sites.
Insecure Authentication and Session Management
In most cases, the cause of insufficient authentication and session management problems is an IAM approach that does not fully comply with modern requirements.
In terms of IAM strategy, users must be granted the bare minimum necessary permissions, accompanied by enhanced verification identities, such as Multi-Factor Authentication (MFA).
Along with use behavior observation, credential management and promptly addressing any irregularities are important too. The failure in application of these rules can make room for security gaps, thus malicious actors can take advantage of the breach and steal essential data.
// Insecure session ID generation
String sessionId = request.getParameter("sessionID");The code gets a session ID from a request using the parameter that is named “sessionID” according to a client. Nevertheless the approach has no security because the former directly believes a user’s input without validation or verification.
The possibility of the attackers to take control of session IDs is here and if it is the case, they will be in position to forge or manipulate session IDs that will then lead to unauthorized access or session hijacking.
Remote Code Execution (RCE)
RCE stands for Remote Code Execution and it is a way that attackers execute commands on remote systems. It usually takes place over a network connection to a computer or to the internet.
Such attacks might be based on software or hardware vulnerabilities or they could simply be made by tricking the user into launching malicious codes. Via the RCE possible safeguard breach, hackers obtain the right to execute and convert entire devices.
Runtime.getRuntime().exec("rm -rf /");These lines of code invoke the system to perform the following command run rf / command , which is a recursive command that deletes all files and directories from the root directory.
Because it’s an extremely dangerous form of unlawful access, it can leave a system unable to repair or cause data loss if it did occur.
SQL Injection
SQL injection is one of the most common cyber-attack types when intruders use SQL injection method to insert unlawful SQL code into the input fields, for example web forms or URL addresses, that may break web application security.
These actions, which are performed to bypass the set security parameters, allow attackers to read, modify or audit the data stored on the database of a web application.
SELECT * FROM users WHERE username = 'admin' OR 1=1; --' AND password = 'password123';In the above code, the select will display all users from the “users” table if the condition username=’admin’ or where the condition 1=1 is true, respectively. In SQL, comments are placed using the ‘–‘ form (double hyphens), making the rest of the query remain ignored.
The vulnerability issue of query and SQL injection is also involved, which through injecting the given condition 1=1, the attacker can get through or ignore the authentication system so that all password concerns will be dropped.
XML External Entity (XXE) Vulnerability
XML External Entity (XXE) is a nasty attack that is aimed at systems that process the XML files. It is when a poorly configured XML reader built into a program allows remote files stored in the server or any URL to be referenced.
When an XML document is parsed and referenced elements are uncovered, the application may unwittingly conduct them, resulting in security concerns, such as revealing confidential information, disrupting services, and initiating unauthorized server activities and accessing other system components.
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM "file:///etc/passwd">
]>
<data>&xxe;</data>This code snippet specifies XXE “xxe” external entity within the DTD declaration. It references a file “passwd” located in the “/etc” directory of the server using the “file://” protocol.
While analyzing XML document, “&xxe;” entity is expanded leading to the insertion of the entire contents of given file into “data” element.
This may result in the arrival of sensitive information, like user account information from “/etc/passwd” file.
Man-in-the-Middle (MitM) Attack
Man-in-the-Middle (MitM) attacks are usually launched in between the two sides communication channels that are set up secretly by the attackers, intercepting their data exchange. This unlawful activity provides a chance not only to listen-in on data communications, but also manipulate data.
One of the most common types of cyberattack is the local network, where an attacker can be placed between a user and the network portal. Through such a position, they can steal sensitive information, such as login details or personal communication, without the user knowing.
Trojan Horses
Trojan horse belongs to the category of malware that is composed of deceitfully innocent files that is used to infiltrate the computer system to eventually create, propagate, and multiply destructive effects.
They trick users through the very fact of mimicking the normal ones by eventually inflicting harm on the system and making away with any of the secret data.
The fact that they were able to slightly disguise their real nature makes them the biggest danger to cybersecurity.
# This is a legitimate-looking Python script
def display_cute_kittens():
print("Here are some cute kittens:")
# Display images of cute kittens here
# The code below appears unrelated to the above function
def steal_sensitive_data():
with open("sensitive_data.txt", "r") as file:
data = file.read()
# Send the stolen data to a remote server controlled by the attacker
# The following code is intentionally hidden
display_cute_kittens()
# Unbeknownst to the user, the Trojan horse performs malicious activities
steal_sensitive_data()While having a look, it seems completely harmless, with a function “display_cute_kittens()” presumably just displaying images of cute kittens. It is important to mention that this function is exacting but it has a hidden function “steal_sensitive_data()” that reads data from a file named “sensitive_data.txt“.
It then sends it to a remote server controlled by an attacker. This second quality acts like a Trojan horse as it tricks the users into believing that this thing behaves normally while it does all the terrible things itself backstage.
Credential Stuffing
Credential stuffing is said to put people at risk constantly because as a result of the habit of reusing email addresses and login credentials over many websites.
Hackers gain control of systematically hacked passwords and apply brute force robotized techniques against usernames on different resources in order to steal passwords and gain unauthorized access to accounts.
Unvalidated Redirects and Forwards
URL Redirection attack where the attacker tampers with the URL and then sends it to the victim. Any time the victim clicks on the link, they are redirected to a site specified by the attacker, which can either be a malicious site or just a wrong one.
Such kind of unusual chains gives attackers an opportunity to change the processing of an application.
@WebServlet("/UnvalidatedForwardServlet")
public class UnvalidatedForwardServlet extends HttpServlet {
protected void doGet(HttpServletRequest request, HttpServletResponse response) {
String destination = request.getParameter("destination");
if (destination != null && !destination.isEmpty()) {
try {
// forward the request to the specified destination
request.getRequestDispatcher(destination).forward(request, response);
} catch (Exception e) {
e.printStackTrace();
}
} else {
// Inform users if the destination is invalid
response.getWriter().println("Invalid destination");
}
}
}In the above code, in the doGet() method it operates on a parameter named “destination” which is sent implicitly by the HTTP request.
Servlet then checks if the parameter is not null and not empty. If it passes this test, servlet uses getRequestDispatcher() method to forward the request to the destination mentioned.
But, there is no refinement at the target parameter and thereby it gives the criminal the leverage to manipulate the parameter such that the user can be redirected to somewhere that is not meant to be or to a malicious or exploitative location.
The servlet shall send “Invalid destination” as a message in case of invalid or missing destination to the user.
Conclusion
Defending against malicious code threats requires a multi-layered approach encompassing proactive measures, vigilant monitoring, and robust security practices. Understanding the various types of malicious code is crucial for implementing effective defense strategies.
Preventive measures include installing and updating antivirus software, keeping all software up-to-date, exercising caution with email attachments and links, enabling firewalls, conducting security awareness training, and implementing strong authentication and access controls.
Regular security audits and vulnerability scans are also essential for identifying and addressing security gaps. DigiCert Software Trust Manager helps you in identifying the malicious codes which helps you to defend your SDLC.

