Top 10 Security Tips to Prevent Downloading Malicious Code or Data

Malicious code is an unwanted file or program that causes harm to a computer or compromises data stored on a computer. Generally, it (malicious data) enters a system when a user clicks on a vulnerable link or downloads an infected file.
Once a system is infected, it can cause a computer to – slow down, become unresponsive to keyboard inputs, overheat, get bombarded with ads, and more.
Malicious code or data can conceal itself in innocuous-looking software components and can appear in numerous forms like – viruses, worms, spyware, trojan horses, logic bombs, etc. Sometimes, it’s so well-concealed by social engineering and other shady practices that it even gets incredibly challenging for trained cybersecurity professionals to see through its deception.
So, are there ways or security practices that we can follow to prevent ourselves from downloading such malicious code? The answer to this query is – “Yes, there are!” In this article, we will be exploring – “The top 10 security tips to prevent downloading malicious code or data.”
How To Avoid Downloading Malicious Software?
Follow below tips and tricks for safe, secure browsing and downloading on internet.
Use Trusted Download Sources
When downloading software, apps, or files from the internet, always rely on reputable sources. Official websites, app stores (like – Google Play and Apple App Store), and trusted repositories are your safest bet. Avoid downloading software or files from random websites or third-party sources, as these are often breeding grounds for malicious code.
Beware of “cracked” or “pirated” versions of paid software, as these are frequently bundled with malware. To stay safe, pay for legitimate software or use open-source alternatives.
Recommended: Best Safe Download Checker Tools to Protect Your Devices from Threats
Be Cautious with Email Attachments and Links
Email is a common vector for – malicious code distribution. Thread actors often send “Phishing Emails” to mislead or deceive recipients into downloading harmful attachments or clicking on malicious links. To avoid falling victim to these scams:
- Confirm the sender’s email address and be cautious of unanticipated or suspicious emails.
- Don’t open attachments or click on links in links in emails from unknown sources.
- Hover over links to preview the URL before clicking, ensuring they lead to legitimate websites.
- Watch for minor spelling errors or other alterations designed to mislead you.
- Use advanced email filtering and anti-phishing tools like – MailWasher Pro, RSA FraudAction, Avanan, etc., if available and necessary.
Employ DNS-Level Traffic Filtering
While avoiding non-secure websites that don’t use https:// is a good start, advanced malware can slip through even on seemingly safe sites. To ensure you catch every potential threat, implement advanced content filtering at – HTTP, HTTPS, and DNS levels.
By blocking unsecured sites at a DNS level, you’ll avoid downloading malicious code by preventing certain domains from loading in the first place and avoiding DNS hijacking.
You can also utilize solutions like – Heimdal Threat Prevention, with DarkLayer guard and VectorN Detection technology, that can actively hunt, detect, and prevent malicious code, ensuring your network and endpoints remain secure.
Block Pop-Up Ads
Pop-up ads, besides being annoying, can also contain malicious code. Therefore, blocking pop-ups across all devices is a prudent security measure to stay protected from these threats. Some browsers, like -Google Chrome, Mozilla Firefox, etc., offer the option to block pop-ups and redirects in their Settings menu.
Regarding third-party tools, you can use the StopAll Ads browser extension that helps block the ads and safely browse the web. Furthermore, with this extension, you can also avoid being tracked and set ad filters to authorize ads to be displayed only on your favorite websites.
Be Cautious of Free Software
Beware of free software offers, especially those that seem too good to be true. Some websites may offer you a cash prize or a chance to win free software in exchange for downloading their product or filling out a form; don’t fall for such cases as it’s a trap to lure unsuspecting users and make a fool out of them.
To avoid downloading malicious code, always search the internet to confirm whether an offer is legitimate. It’s also recommended to visit the official website to get accurate information.
Recommended: How to Check Software Security to Prevent Dangers of Downloading Software?
Stay Away From Unsecured Sites
Unsecured websites are breeding grounds for – Trojans, viruses, worms, and other forms of malware (malicious code). To maintain a safe online environment, avoiding such sites is paramount. But a question arises: “How do we identify whether a website is secure or unsecured?”
Fortunately, it’s relatively easy to identify secure websites. Look for the keyword – “https://” in the URL, indicating the presence of an SSL (Secure Socket Layer) cert.
(SSL certificates create a secure, encrypted connection, protecting your data from malicious interception.) Websites using the older “http://” protocol are no longer considered secure, and all actions like – downloading stuff, entering confidential data, etc., on these sites should be avoided.
Install a Firewall
A firewall is security software designed to monitor network traffic & prevent malware infection by intercepting malicious traffic. If your Windows firewall is in – “Off Mode,” then a malicious actor can gain unauthorized access to your computer by sending malicious scripts to your computer; hence, enabling malicious traffic-blocking capabilities of a firewall is a must.
Follow the steps mentioned below to enable Windows Firewall:
- Click Search, type Control Panel, and press Enter.
- The Control Panel window will appear.
- Click System and Security.
- Click Windows Defender Firewall.
- In the left pane, click “Turn Windows Firewall on or off.”
- Click the Turn on Windows Firewall radio button for both (Private and Public) network settings.
- Click OK.
Apply Software Patches Immediately
No software package is completely immune to malware. That is why software vendors provide patches and updates regularly to address whatever new vulnerabilities show up.
As a best practice and as per the Cybersecurity and Infrastructure Security Agency (CISA), it is important to validate and install all new software patches as soon as possible.
Also, regularly update your operating systems, software tools, browsers, and plug-ins. Implement routine maintenance to ensure that all software is up to date and check log reports for signs of malware or malicious code.
Disable External Media AutoRun and AutoPlay Features
AutoRun and AutoPlay are features developed to make it convenient for users to access the data stored on removable media like – CDs, DVDs, USB drives, etc.
Although these features are convenient, sometimes, they can also pose a potential security risk. Disabling these features prevents external media infected with malicious code from automatically running or getting downloaded on your computer.
Install Antivirus
Antivirus software is necessary to shield your local machine (computer) from viruses, spyware, etc. If you don’t have an antivirus installed, choose the one that recognizes a broad range of malicious code and has regular updates to its virus definitions to stay current with emerging threats.
Opting for a next-generation antivirus (NGAV) that provides a blend of antivirus, firewall, and anti-spyware software is recommended instead of using each separately.
How Can You Tell If Your System is Infected With Malicious Code?
You can tell if your system is infected with malicious code if you notice:
- Sudden and noteworthy decrease in your computer’s performance.
- Constant redirection to unfamiliar websites, especially when browsing.
- Frequent system or application crashes without an apparent cause.
- Files become inaccessible or display errors.
- An influx of intrusive pop-up messages or ads.
- Noticeable increase in Internet data usage.
- Your antivirus or firewall software is turned off without your consent.
- Unfamiliar icons appear on your desktop.
- You can’t access or make changes in the control panel.
- Frequent and unusual browser errors and warnings.
- Suspicious shortcuts or icons appear on your desktop or in your files.
How to Remove Malicious Code From the System?
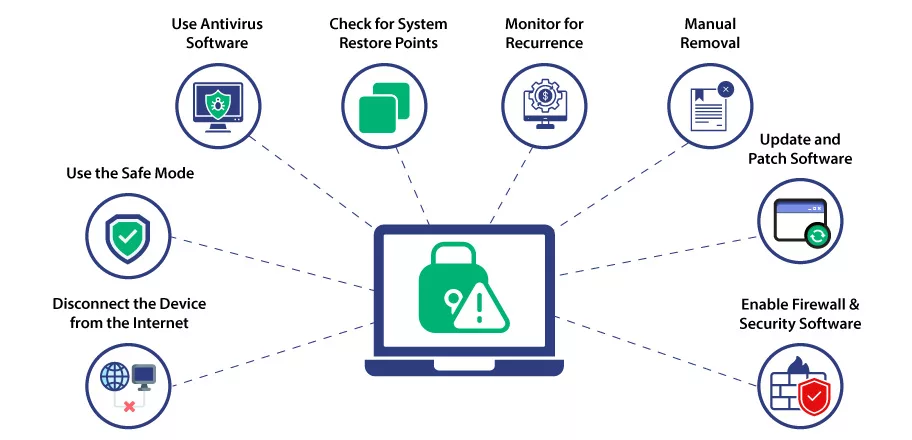
If you suspect or know that your system has malicious software, here are the steps you should take immediately:
Disconnect the Device from the Internet:
Unclog your network cable or disable WI-FI to stop the malware from communicating with its control server or spreading further.
Use the Safe Mode:
Boot your computer in Safe Mode. Doing so limits malicious code from functioning while it’s being removed.
Use Antivirus Software:
Run a complete scan. Follow the software’s onscreen instructions to quarantine detected threats.
Check for System Restore Points:
If your operating system supports it, use a restore point from a time before the infection occurred. This can revert your system to a clean state.
Manual Removal:
If you are experienced, you can attempt the manual removal of malware by identifying and deleting malicious files, registry names, and processes. Be cautious not to delete critical system files.
Update and Patch Software:
Verify whether your OS, browsers, software, etc., are up-to-date or not. If not, then download the latest version.
Change Passwords:
If any of your account(s) were compromised during malware infection, alter the passwords for that account(s).
Enable Firewall & Security Software:
If security solutions were disabled during the infection, re-enable them.
Monitor for Recurrence:
Keep an eye on your system’s behavior for a while to ensure the malware doesn’t return. Frequent scans with security software can help.
Conclusion
Cybercriminals or malware authors can spread malicious code that infects devices and networks through diverse physical and virtual means. As a result, it is preferable to take the precautions discussed above rather than be sorry later.
Furthermore, if you suspect yourself to be a victim of a malicious software attack, check for the signs we discussed above, and if your suspicion stands correct, perform the steps outlined under the heading – How to remove malicious code from the system.

Code Signing Certificates
Add a digital signature on a file, program, software, or driver using Trusted Code Signing Certificate from trusted root certification authority using a secure public key infrastructure (PKI).
