How to Check Software Security to Prevent Dangers of Downloading Software?

Since software and applications have become an integral part of our daily lives, internet users constantly lookout for new programs and games to enrich their experiences.
The convenience of accessing a vast array of software is readily available, with authorized gaming platforms, trusted online services, and distribution platforms like App Store, Microsoft Store, and Google Play leading the way. These platforms offer assurance, adhere to stringent security measures, and minimize the risk of downloading infected or malicious software.
However, amidst this technologically advanced ecosystem, a hidden peril awaits those who venture into the uncharted territory of untrusted websites. A different reality unfolds here, with myriad threats lurking in the shadows, posing a significant risk to unsuspecting users.
This article will explore the contrasting realms of trusted distribution platforms and unverified websites, shedding light on the pressing need to safeguard our digital playgrounds from potential viruses and malware.
5 Best Software Security Testing Platforms
Cybercriminals are perpetually devising new tactics to breach network security and compromise valuable information. As the threat landscape expands, the need for robust software security testing tools has become increasingly prevalent.
Performing thorough network security testing and identifying vulnerabilities before hackers do is imperative to safeguarding sensitive data and ensuring a resilient defense against cyber threats.
Among the multitude of tools available for network security testing, we have curated a list of the top 5, each renowned for its efficacy and reliability:
NMAP:
NMAP is a versatile and powerful open-source network scanning tool that allows you to discover hosts and services on a computer network. It is widely used for security auditing and network exploration, enabling you to identify potential vulnerabilities and security issues within your network.
Astra Security:
Astra Security is a comprehensive security testing suite designed to identify and remediate security loopholes in web applications. It includes vulnerability scanning, penetration testing, and security scanning to ensure robust protection against cyber threats.
OpenVAS:
OpenVAS (Open Vulnerability Assessment System) is an open-source vulnerability scanner and manager. It offers a vast database of known vulnerabilities and can be used to perform regular scans to detect potential security flaws in your network and systems.
Wireshark:
Wireshark is a widely-used network protocol analyzer that allows you to inspect and capture data packets on a network. It is a valuable tool for analyzing network traffic, helping to uncover suspicious or malicious activities, and ensuring data integrity.
Nikto:
Nikto is an open-source web server scanner identifying potential security risks and vulnerabilities in web applications. It scans for outdated software, configuration issues, and potential security loopholes, providing valuable insights for enhancing web application security.
With these top-tier software security testing tools, organizations and individuals can proactively assess and fortify their network defenses, reducing the risk of cyberattacks and protecting valuable information from malicious actors.
Unleash the Power of Windows SmartScreen Filter
Today, countless websites and programs beckon users, ensuring our online safety is paramount. Thankfully, modern operating systems, such as Windows, come equipped with robust security tools like the Windows SmartScreen Filter. This built-in system tool is an automatic safeguard, diligently examining websites and downloaded programs for potential threats.
The functionality of Windows SmartScreen Filter is simple but effective. As users venture into cyberspace, it actively scrutinizes websites and programs. If suspicious elements are detected, the filter triggers a warning page, cautioning the user about potential risks. It includes a dedicated warning about potentially harmful software.
What are the Basic Practices of Downloading Software?
When downloading programs, one should always take chances with trusted sources. Before initiating any downloads, it is essential to employ basic best practices. Always verify the website’s credibility from which you intend to download software. Trusted sources, such as authorized stores, should be your primary destinations.
Moreover, be vigilant for telltale signs of unreliability, such as websites with misspelled URLs or lacking proper security measures. Be cautious with links shared by unknown individuals or through chain mail, as they might lead to programs with malicious intent.
Verifying Software Authenticity with Code Signing Certificates
As tech-savvy users, one valuable tool at our disposal is the software certificate, also known as Code Signing. This powerful tool allows developers to sign their code, protecting against unauthorized modifications.
When we encounter software from a Trusted Publisher, we can delve deeper into its authenticity by checking its Code Signing certificate. By doing so, we can gain the assurance that the software remains untampered and virus-free since its initial publication. So, how do we perform this crucial verification process?
Before installing the program, simply right-click on its icon and select Properties. A window will then materialize on your screen, revealing all the essential information about the software and its digital signature.
This information encompasses the software’s origin, the entity responsible for its creation, the time it was signed, and other vital details that bolster our confidence in its trustworthiness.
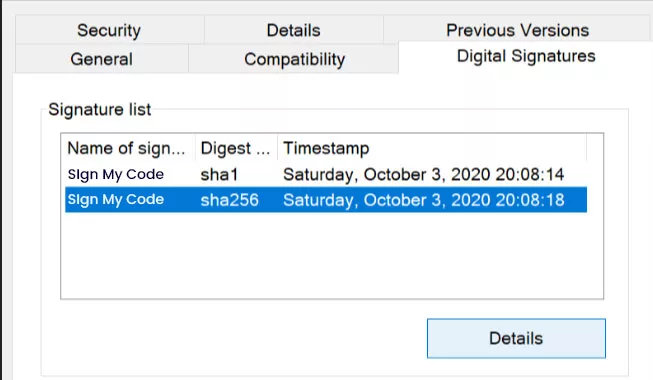
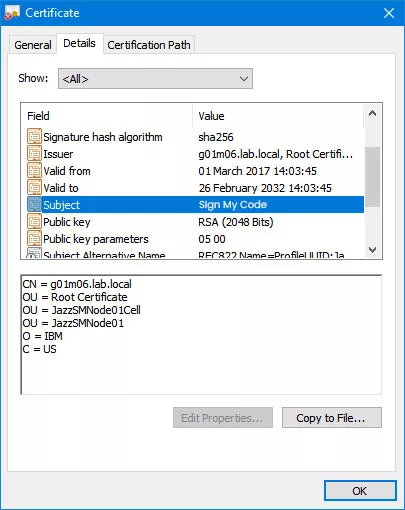
Real Time Example of Digital Certificates
Think of digital certificates as ID cards for software on the Internet. They are essential credentials that identify the code and facilitate its distribution on reputable and trusted platforms.
When we download software bearing a Code Signing certificate from a Reliable Provider, we can rest assured that it meets the stringent security criteria set forth by the signing entity.
Therefore, take the extra step to validate a software’s Code Signing certificate. By doing so, we actively contribute to a safer digital environment, promoting the usage of reliable software while guarding against potential threats.
Prioritize Safety by Preventing Unknown Software Publishers
As responsible users, it is essential to exercise prudence when downloading software, especially from unfamiliar sources. One key aspect to observe is the authorship of the software, which is typically presented at the beginning of the installation process in a distinct window, revealing vital information about the program.
Recommended: How to Fix Unknown Publisher Security Warning?
A critical red flag to heed is an “Unknown Publisher” in the author field. Consider this as your initial warning sign. When a software’s author is listed as an Unknown Publisher, it signifies that the owner is not a publicly trusted entity, lacking positive verification from a Certification Authority and a Code Signing certificate.
While it doesn’t automatically imply that the software is malicious, it raises concerns about the author’s commitment to the code’s integrity and the users’ safety.
The Function of Certification Centers:
Certification Centers are pivotal in enhancing digital security by offering global trust services based on stringent regulations. These reputable organizations validate the identities of online entities, granting them trusted and legitimate electronic certificates, including electronic signatures.
By adhering to these rigorous standards, Certification Centers act as guardians of digital security, fostering a safer online environment for all users.
Always remember to prioritize safety over convenience when downloading software. Avoid programs from unknown publishers and authors, as they can expose you to potential risks. Instead, opt for software from trusted sources with rigorous verification processes, ensuring a safer and more reliable digital experience.
We can confidently navigate the digital landscape by staying vigilant and informed, protecting ourselves and our systems from potential threats.
Rundown of Practices for Security Testing:
- Data protection techniques involve testing the security measures implemented to safeguard sensitive data from unauthorized access, tampering, or theft. It includes encryption, hashing, access controls, and data anonymization.
- SQL Injection and XSS testing focus on identifying vulnerabilities in web applications that could allow attackers to execute malicious code or manipulate database queries, potentially compromising the application and its data.
- This testing technique evaluates an application’s access controls and authentication mechanisms to ensure that only authorized users can access specific functionalities and sensitive data.
- Brute-force attack testing involves assessing the application’s resistance to brute-force attempts, where an attacker tries all possible combinations of usernames and passwords to gain unauthorized access.
- Session management testing verifies the robustness of an application’s session handling process, ensuring that user sessions are secure and protected against session hijacking or session fixation attacks.
- This technique involves focusing on critical or high-risk functionalities within the application, such as payment gateways, file uploads, and administrative features, to identify potential vulnerabilities and weaknesses.
- Error handling testing examines how an application responds to various input errors, ensuring that error messages do not expose sensitive information or assist attackers in exploiting potential weaknesses.
- Organizations can proactively identify and address vulnerabilities in their applications, networks, and systems by employing these top security testing techniques, mitigating potential risks and enhancing overall cybersecurity posture.
Wrapping up
We can fortify our digital defenses and enjoy a safe and seamless online experience. Let us embrace the power of intelligent browsing and empower ourselves against potential cyber threats.

