What is AWS CloudHSM? Everything to Know About

Amazon Web Services are constantly leading the charts by providing exceptional cloud services to their global customer base. One of their services is CloudHSM – a cloud-based hardware security module. In recent years, the usage of encryption and cryptography has rapidly increased, and so has the usage of AWS CloudHSM.
The CloudHSM from AWS is a well-developed and secure platform that every professional prefers. So, let’s learn about it to understand what it is and why experts are recommending it.
What is AWS CloudHSM?
AWS CloudHSM is a combination of two technologies: the AWS cloud service and the HSM (Hardware Security Module). In general, HSM is a physical USB device that helps to run cryptographic functions and store cryptographic keys for code signing and SSL certificates.
If you only use an HSM, you are required to secure the physical device. It also restricts you from using the digital certificates remotely if the USB is not available to you. However, with AWS CloudHSM, such restrictions are eliminated.
AWS CloudHSM offers the functionality of using a cloud-based HSM module to execute cryptographic functions and securely store the keys. In addition, it’s accessible from anywhere and also aligns with the required administrative, regulatory, and industry standards.
Features of Amazon Cloud HSM (AWS CloudHSM)
The features of AWS CloudHSM are highly impressive, benefitting the organizations with:
Compliance with FIPS 140-2 Level 3
For digital certificates, CA/B has defined the HSM to be FIPS 14-2 Level 2 compliant. But AWS is a step ahead. It provides HSM aligning with FIPS 140-2 Level 3 to provide more security and flexibility in using the cryptographic keys and algorithms.
E2E Encryption is hidden from AWS Cloud
In the HSM case, having more responsibility in handling the HSM is an added advantage. All the end-to-end encryptions performed at the data plane are hidden from AWS and out of the scope of IAM roles. Thus, you will have complete control.
Complete Control of the Key and Associated Component
In AWS CloudHSM, you receive 100% control of the keys and algorithms. It enables you to store, import, export, and manage all kinds of keys, including token keys, asymmetric keys, symmetric keys, session keys, and more. Moreover, you can also control the threading, app language, and the physical existence of your software.
Seamless Migration
Migrating to AWS CloudHSM is an easy and quick task. Regardless of the public key infrastructure, you can migrate and use the AWS-based HSM functionalities. It’s highly compatible with PKCS #11, JCE (Java Cryptographic Extension), CNG (Cryptographic API: Next Generation), and KSP (Key Storage Provider).
Compatibility with Cloud Code Signing Certificates
AWS CloudHSM works efficiently with a cloud code signing certificate. You can directly import your digital certificate from CA to the AWS HSM storage. It will save you time and leverage, improve collaboration, and ensure the utmost private key security.
How it Works?
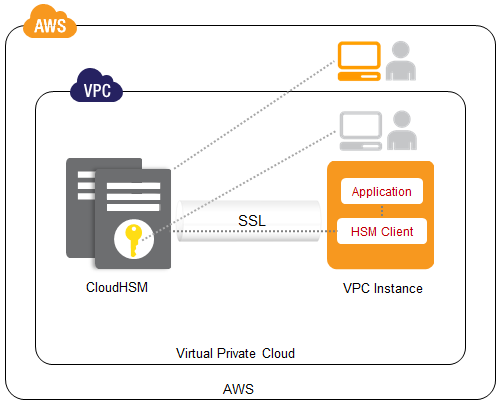
To use the AWS CloudHSM, you need to configure a Virtual Private Cloud (VPC) on the platform. Further, you need to perform the following operations in the defined sequence.
Cluster Configuration >> Adding of HSM >> User and Key Creation >> HSM and App Integration using the Client SDKs.
All these components work in collaboration to enable the HSM user to access the HSM through SDKs and utilize the key stored in it for encryption, decryption, and cryptographic processes.
Following this configuration, you can integrate and utilize other AWS services, such as CloudWatch and AWS CloudTrail, to log and monitor the CloudHSM.
To understand it more thoroughly, let’s have a look at all the configured components.
Cluster
In AWS, the collection of numerous individual HSMs is known as a cluster. The main aim of configuring a cluster is to maintain the synchronization and availability of every HSM to the end user. The maximum capacity of the cluster is 28 HSMs. Also, it will automatically update and maintain the HSMs per your goals and usability.
HSM Keys
You can use the AWS CloudHSM to store, import, and export any type of symmetric, asymmetric, token, and encryption key. And when you will need it, you can access the HSM to perform your operations. In addition, AWS offers you the advantage of defining who owns the key, controlling key access, choosing from algorithms, and managing the keys.
HSM Users
If you want to use AWS CloudHSM, you need to create HSM credentials for it per the policies defined by the AWS platform. These users are different from IAM users and have the authorization to manage HSM and modify its configurations. However, you need to be an IAM user to create an HSM user account.
Client SDKs
To use the AWS CloudHSM and execute cryptographic operations, you need to use the client SDKs (Software Development Kits). Primarily, PKCS #11, JCE, OpenSSL Dynamic Engine, and KSP SDKs are available. You can use any one or all the SDKs per your convenience and requirements.
Cluster Backups
Every HSM present in the cluster creates a backup of the keys, users, and defined policies. These backups are created periodically for the utmost availability and durability of all the CloudHSM features and functionalities. Moreover, to ensure backup security, AWS stores all the backup data in an encrypted format.
When to use AWS CloudHSM?
AWS CloudHSM can fulfill all significant requirements, and you can prefer using it for the following needs:
- When you are required to handle multiple hardware security modules.
- When you want secure remote access to the cryptographic keys.
- When you want to import and export the cryptographic keys.
- When you need to share the HSM between your time or with any other authorized user.
- When you want to constantly comply with security and industry standards.
- When you are required to integrate HSM with applications.
- When you want additional security controls and policies for the HSM security.
What is the Difference between AWS KMS and CloudHSM?
To efficiently understand the difference between AWS KMS and CloudHSM, let’s undergo an overview of AWS KMS.
AWS KMS refers to the Key Management Service. This AWS service provides you the features to generate, store, and manage the encryption and cryptographic keys and also perform the operations associated with them. In addition, it’s integrated with CloudTrail service, aiding in logging every detail on the platform and monitoring operations executed by all users.
Further, there are three types of KMS services available:
AWS-owned, AWS Managed and Customer Managed KMS services.
You can use any of the methods per your requirements and leverage the benefits as follows:
- Management of cryptographic key automatic rotation.
- Message verification with asymmetric key.
- ABAC (Attribute-based Access Control) control for keys.
- Configuration of key policies and more.
For better clarification, let’s look at the differentiation table.
| Basis | AWS KMS | AWS CloudHSM |
| Followed Standard | Complies with FIPS 140-2 Level 2 | Complies with FIPS 140-2 Level 3 |
| Tenant | Multi-Tenant | Single Tenant |
| Support for Master Key | It supports three master keys: AWS Managed, Customer Owned, and AWS Owned | Only the HSM Master Key is supported |
| Accessibility of Key | Multi-region accessibility | Only accessible in the Virtual Private Network |
| Management | Managed by AWS | End-user/Customer Managed |
| Other AWS Service Integration | Enables integration of all other AWS services | AWS integrations are limited |
| Price | Affordable as compared to CloudHSM | Moderate Cost |
| Acceleration of Cryptographic Functions | Nil | TDE and SSL/TLS Acceleration |
Exclusive AWS CloudHSM Use Cases
You can use AWS CloudHSM to fulfill all your significant objectives. It can be used in the following cases:
#1: To Comply with Regulatory Standards
According to the security standards, every organization has to utilize an HSM aligning with a minimum of FIPS 140-2 Level 2 standards. But, by using AWS CloudHSM, you can leverage a FIPS 140-2 Level 3 HSM to store the private keys. In addition, AWS ensures compliance with PCI-DSS and PCI-3DS, adding an extra layer of security.
#2: To use Private Keys for Software Signing
You can use AWS CloudHSM to store the private key associated with a code signing certificate. Certificate authorities have made HSM compulsory for all digital certificates.
But, if you don’t want to handle a physical device and require a secure 24/7 availability of the private key, AWS CloudHSM is a perfect solution. In addition, by purchasing a DigiCert EV Code Signing Certificate, you can directly receive the private key in your cloud HSM.
#3: For Data Encryption and Decryption
As we know, encryption and decryption are performed using private and public keys. You can use the AWS CloudHSM to store, secure, manage, and utilize such keys. With the help of client-side SDKs, you can access the HSM and execute encryption/decryption operations.
#4: To Authenticate Messages
With AWS CloudHSM, you can store and manage the symmetric keys used in CMACs (Cipher Message Authentication Codes) and HMACs(Hash-based Message Authentication Codes). It will help you ensure the message’s authenticity and integrity while they are transmitted over an insecure network.
#5: To Efficiently Manage Multiple Keys
While undergoing the working of AWS CloudHSM, you know that a cluster is created, which supports you in managing a total of 28 HSMs simultaneously. So, if you need to handle multiple sessions, cryptographic, token, symmetric, and asymmetric keys, you can use the CloudHSM from Amazon Web Services.
#6: To Configure Reliable TDE (Transparent Data Encryption)
Transparent data encryption is configured for databases to store every data bit in an encrypted format. Whenever the database receives an input, it uses the TDE master encryption key to secure the information. You can use the AWS CloudHSM to store that TDE encryption key securely. In addition, you can configure the database to access the key from CloudHSM and then use it.
#7: For Offloading SSL/TLS
By integrating AWS CloudHSM, you can reduce the load on your web server to use the public and private key for HTTPS connections. The CloudHSM processor will execute all the encryption algorithms, speeding up the SSL operation and saving server resources.
#8: For Random Number Generation
Random number generation is a crucial operation under the encryption umbrella. You can use the AWS CloudHSM to create random numbers and configure their access, authorization, and authentication controls per the required business needs.
Common AWS CloudHSM FAQs
Here are the answers to some of the most asked AWS CloudHSM questions. Undergoing them will help you clear your additional queries about this AWS service.
Is it necessary to create a VPC to configure CloudHSM?
The VPC or Virtual Private Cloud is the primary requirement to use CloudHSM. It helps to isolate the HSM procedures and secure the keys from IAM and unauthorized users. Thus, VPC is a must for CloudHSM.
What exactly is an HSM (Hardware Security Module)?
An HSM is a physical device used to store cryptographic and encryption keys to retain their integrity, confidentiality, and availability to legitimate users. These physical devices are tamper-resistant and consist of their own processors to execute the encryption, decryption, and cryptographic operations.
Recommended: What is a Hardware Security Module? Role of HSMs for Digital Signing
Does my HSM and Application have to be in the same VPC?
No, it’s not necessary to configure HSM and application in the same virtual private cloud. But you need to ensure that your app and HSM are reachable by each other. There must be IP connectivity between the two for communication.
You can use VPC peering, VPN (Virtual Private Network), and Direct Connect to establish communication.
How can my custom application use the CloudHSM?
To enable custom applications, use the AWS CloudHSM, which allows you to integrate the standard APIs. AWS provides support for the following:
- PKCS #11
- Java Cryptography Architecture
- Java Cryptography Extension
- Microsoft CAPI
- Microsoft CNG
What are the Charges for using CloudHSM?
All the CloudHSM users are charged on an hourly basis. If your cluster does not have any HSM, then you will not be billed. However, the hourly charges are different for every region. You can check by visiting the AWS website or using the AWS service calculator.
Do I have to Manage the HSM Firmware and Compliance by myself?
No, you are not required to manage the hardware’s firmware and compliance. Amazon web services will handle the firmware aspect. The HSM provided to you will be updated per the latest technologies and policies and will also comply with FIPS 1402-2 Level 3. For extended safety, NIST will be checking the compliance of all HSMs powered by AWS.
Concluding Up
AWS CloudHSM is a reliable technology for organizations dealing with cryptographic and encryption keys. It reduces your efforts to manage multiple HSMs and maintain their compliance with FIPS standards. In addition, it enables the storage of all kinds of keys in a secure and isolated environment, accessible through special user credentials.
Furthermore, it can be used with your custom applications to support SSL/TLS offloading and crypto key generation, storage, and management. Therefore, AWS CloudHSM is an all-in-one solution for all significant public-private key use cases.
Recommended: How to Use Microsoft SignTool with AWS CloudHSM to Digitally Sign Authenticode Files?
