What Is Software Supply Chain Security? Comprehensive Guide
Software supply chain security is on the highest priorities list of an organization. It consists of every major and minor stakeholder, tool, application, and resource associated with a software development project.
However, some organizations still need clarification about it or need to know how exactly they can maintain it and prevent attackers from exploiting the supply chain.
But now, with this blog, everything will be cleared within minutes. It will help you understand the need for software supply chain security, causes for exploitation, best practices to use, and an advanced solution for seamless management.
So, let’s get started to secure the supply chain.
What is Software Supply Chain Security?
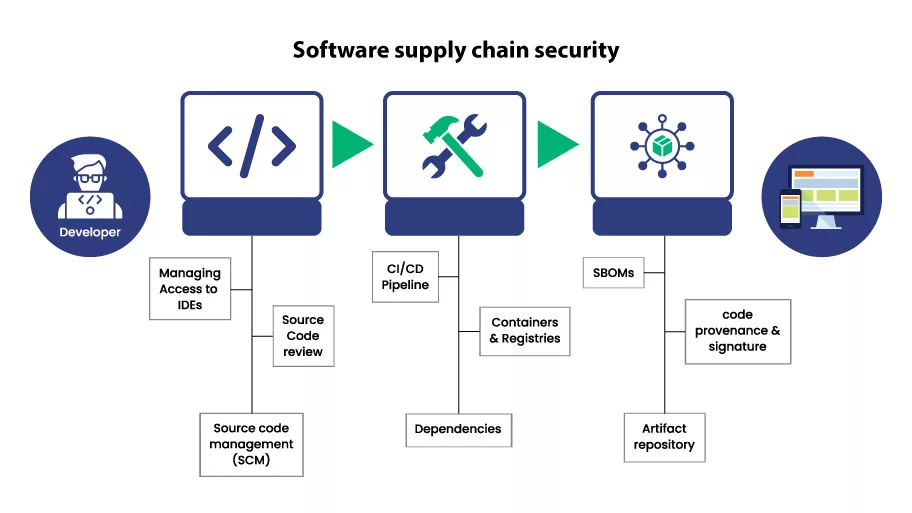
To learn about software supply chain security, it’s necessary to undergo the definition and overview of the software supply chain or SSC.
The software supply chain is regarded as the complete software development lifecycle, including the associated stakeholders, tools, activities performed, and operations executed. The SSC covers each and every minor and major aspect associated with SDLC.
Now, let’s come to Software Supply Chain Security.
The procedures, tools, and resources (hardware, software, and human) incorporated to secure the software supply chain come under the umbrella of software supply chain security. In addition, the techniques, tools, and strategies used to analyze, detect, and mitigate cyber security are also involved in SSC security.
Therefore, the primary purpose of software supply chain security is to secure the overall software development procedure and not let any illegitimate actor interfere at any point. SSC security objectives are achieved when your software is created, released, and maintained with utmost security assurance.
The Need for Software Supply Chain Security
The need for software supply chain security is in every industry, specifically for organizations aligning with the following use cases.
Use Case #1:
The software development company, offering offshore services to other firms.
Use Case #2:
The organization has an in-house software development team handling the development and maintenance of the business website and application.
Use Case #3:
The firms offering software like ERP solutions to other organizations.
Use Case #4:
The organizations avail of the software development services but are going to maintain the application by themselves only.
Further, once SMEs and enterprises start to use the software supply chain security, they will leverage the benefits as follows:
- The software development resources will be secured from cyber-attacks.
- The code integrity and confidentiality will be maintained.
- A secure and well-functioning software will be released for the end-users.
- Vulnerabilities will be reduced, leading to minimizing the possibility of exploitation.
The Causes of Software Supply Chain Attacks
According to software and infrastructure security professionals, numerous major and minor causes of a software supply chain attack can exist. But, the following are the top reasons upon which you should surely focus.
#1: Lack of Security Controls
The lack of security controls is a primary cause of supply chain attacks. It leads the hackers to discover vulnerabilities in your operating systems and applications. Further, they try to exploit the vulnerable loopholes for deleting, locking, forging, or modifying the data available on your machine.
Besides this, a lack of physical security controls can also be a primary reason. If you don’t have ID cards, biometrics, RFIDs, and CCTVs, then an attacker can enter the premises to perform illegitimate activities.
#2: Writing Insecure Code
Not following the coding standards is one of the main factors in writing insecure and incompatible code. When the developer adds additional methods, instances, and classes, it increases the load on the processor and unleashes an extended attack surface.
Due to non-compliance with coding standards, the following circumstances occur:
- It becomes easy for attackers to crash the server through DoS and DDoS attacks.
- The hackers find more vulnerabilities to exploit, impacting the software performance, security, and stability in the long run.
- The software maintenance efforts, cost, and time are increased.
#3: Not Verifying the Source
While developing software, several third-party IDEs, tools, and APIs are used to integrate all the services and functionalities. However, if any of the components are downloaded from a forged site, it can open backdoors, malware attacks, and data breaches.
Recommended: How to Check Software Security to Prevent Dangers of Downloading Software?
If there are no defined guidelines for the development team to check the source of every tool, API, and application, the possibility of a supply chain attack is relatively high. So, you should always consider the source verification factor while analyzing the attack’s root cause.
#4: Using Self-signed Code Signing Certificate
The developer itself generates the self-signed code signing certificates, and there’s very minimal possibility of the latest algorithm being used. Due to this, the illegitimate actor avails of a benefit to breach the software, reverse the weak encryption algorithms, and modify the executable file.
Recommended: Self-Signed vs. Publicly Trusted CA Code Signing Certificates: What to Choose?
As a result, the software released for end-users will comprise of malware, leading to:
- The creation of backdoors.
- Lowering down your business reputation.
- Display of Windows SmartScreen warnings.
- Non-compliance with regulatory and administrative standards.
#5: Deploying to Open Repository
To manage the overall software development and maintain collaboration, online repositories, such as GitHub, are used. However, if the development team doesn’t ensure proper repository security control configuration, it can cause a supply chain software attack.
Also, if an open repository is being used, then others can see the code interfere with its core methods and classes. Moreover, whole software can be forged, modified with malware, and combined with a spoofed certificate to jeopardize the organization’s reputation and resources.
Most Common Software Supply Chain Attacks
Now, you know the main causes behind the software supply chain attacks. So, let’s learn about the types of attacks you should be listing during risk analysis to prevent them.
Here, we have listed the top five attacks, but there can be more per the IT infrastructure, procedures, and tools used by the development team.
#1: Breached Certificates
The vulnerabilities in your software development lifecycle can enable an attacker to steal your code signing certificates. If this happens, the illegit actor can use that certificate to sign malware-infected files and distribute them across online platforms.
Further, the following will be the result of the breached certificate attack:
- People will don’t trust your software.
- Operating systems will show warnings for your software.
- The company’s reputation will be at stake.
- Malware can infect your internal system if any of your employees download the malicious software, thinking of it as a legitimate one.
Recommended: Top 10 Security Tips to Prevent Downloading Malicious Code or Data
#2: Compromised Tools
Even before you start the software development process, hackers can be in your system through non-verified tools and applications.
For instance, suppose you need a paid IDE to write the codebase. But, to save money or for any other reason, you downloaded the cracked version of that IDE app from a third-party website. Now, there’s a high probability that malware can be integrated into the installation package, enabling attackers to take control of your machine.
Recommended: Best Safe Download Checker Tools to Protect Your Devices from Threats
Similarly, any other tool, API, or template available on a third party of the unspecified website can be a hacker waiting for you to download the custom malware.
#3: Privilege Escalation
When your systems and enterprise network don’t have appropriate security controls, it leverages an attacker to impersonate and exploit.
Most probably, hackers can do the following after breaching into your company’s network:
- The systems with single-factor authentication can be compromised and converted to bots.
- Backdoors and spyware can be installed on computers.
- Employee’s personal devices can be targeted by exploiting the access points in the building.
- The code used for developing software can be modified, and logs can be deleted for that.
#4: Malware Affected Devices
Your device can contain malware before you even start using it. There can be many reasons behind it, such as:
- If you use second-hand devices, the first owner can be an attacker.
- The devices can be modified in between the transfer from the seller’s location to yours.
- The parts of the computer that can be modified by the manufacturer are purchased from third-party vendors.
In all these circumstances, malware can enter your network; hackers can breach your data and exploit the software supply chain.
Must To Follow Software Supply Chain Best Practices
To prevent software supply chain attacks and patch the associated loopholes in your software supply chain, consider implementing the following best practices, mechanisms, and approaches.
#1: Secure Code Signing at Enterprise Level
You should always use an authentic Code Signing Certificate to secure your software and other executable files. For enterprises, it’s always recommended to use an EV Code Signing Certificate from a reliable CA, such as DigiCert, Comodo, Sectigo, and Certera.
| Certera EV Code Signing | $269.99/yr |
| Comodo EV Code Signing | $274.99/yr |
| Sectigo EV Code Signing | $274.99/yr |
| DigiCert EV Code Signing | $519.99/yr |
The signing certificate will help you hash the entire codebase and encrypt it with the latest algorithms. It will prevent the attackers from accessing the code and modifying it. As a result, your released software will be secured and in compliance with industry standards.
#2: Vulnerability and Threat Detection
Conducting a risk analysis is always recommended before starting any software development project. Every firm should consider executing a qualitative and quantitative risk assessment to understand the type of risk, threat actor, exploitation level, associated vulnerabilities, and mitigation mechanism.
As the output of risk analysis, you will know about the loopholes in your software supply chain. Further, it will become easy to make relevant modifications to implement a secure software development approach.
#3: Strict Enterprise Policies
Policies are highly crucial to making the software supply chain secure. You should always define the following policies:
- Always scan every system before using it for software development.
- All the actions will be logged and secured on a separate server.
- No developer can access the project files on personal devices.
- Personal devices are not allowed in the working area.
- Passwords configured on systems must be of 12 characters and a combination of alphabets, numerical values, and special characters.
In addition, network policies must be implemented to restrict the excessive usage of the internet. Moreover, a background check must be performed for every employee to avoid insider attacks. Further, you can define the policies per your requirements and security objectives.
#4: Constantly Update Infrastructure
New cyber-attacks are also being released with the release of new software, hardware, and tools. You should update yourself on the global cyber environment. It will help you efficiently update the IT infrastructure per current trends, requirements, and standards.
Additionally, use only legitimate software and hardware products to receive all the required updates directly from the vendor.
#5: Prevent Publishing Sensitive Details
Always remember to classify the information as confidential, secret, and top-secret. This technique introduced by the American military will prevent you from publishing sensitive details on the internet. Also, configure the authentication, authorization, and access controls while using online repositories for code storage and collaboration purposes.
As a result, you will prevent hackers from learning about your organization and plan an accurate attack.
#6: Configure Multi-Factor Authentication
In SMEs and large enterprises, multi-factor authentication is a necessity. Whether you provide or receive software development services, authentication must be configured. It will enable only legitimate actors to access the system and execute modifications.
You can use the following multi-factor authentication approaches:
- Password + RFID
- Password + OTP on phone number
- Password + OTP on mail
- Password + Notification on the phone to confirm the login
- Password + Biometrics
- Password + Hardware Security Module
You can choose any of the multi-factor authentication mechanisms and even combine them for more solid security.
#7: Check the Vendor’s Posture and Integrity
Before buying any software and hardware, check the integrity of the vendor. Nowadays, all the devices come with a barcode on their boxes. You can scan them to validate their originality. In addition, to ensure that all the components are legit, you should undergo the SBOM (Software Bill of Materials).
SBOM will provide you with the details about the components used by the vendor and their sources. You can also use this information in your risk analysis to mitigate significant vulnerabilities and threat actors.
#8: Align to NIST Defined Standard
Professionals recommend the SSDF NIST 800-218 framework to secure the software development lifecycle and software supply chain. It offers the guidelines and practices to be followed by an organization to prevent attacks and secure its infrastructure.
The four primary components of the NIST framework include:
- PO (Prepare the Organization)
- PS (Protect the Software)
- PW (Produce Well-Secured Software)
- RV (Respond To Vulnerabilities)
An overview of all these components is that you should conduct risk analysis, use legitimate resources, follow coding standards, patch vulnerabilities, and thoroughly test the software before launching.
DigiCert Software Trust Manager: A Complete Solution To Prevent Software Supply Chain Attacks
In addition to the best practices, using the DigiCert Trust Manager to maintain software supply chain security is highly recommended. It’s an all-in-one software solution from DigiCert, which can help you reduce code risks, prevent compromises, enforce policies, and maintain collaboration.
The DigiCert Software Trust Manager provides an interface for centralized management of all the necessary software supply chain resources and components.
Also, its use cases are quite extended, including:
- Software publication
- Committing code to repositories
- Containerization
- Tool security
- IoT software security and more
Additionally, you can integrate it with all significant platforms, libraries, operating systems, HSMs, and plug-ins. With this one solution, your software supply chain security will stand out from others.
Concluding Up
Software supply chain security is a broad umbrella comprising all software development and maintenance components. A company should always consider its security as a priority and implement the best practices as mentioned.
Also, the causes and attacks should be considered during the risk assessment to be secure and prepared for the future. Additionally, the DigiCert trust manager solution should be used to conduct every necessary operation from the centralized interface.
