CA/B Forum Baseline Requirements v2.8 for Code Signing Certificates
Under the CA/B Forum BRs for Code Signing Certificates v2.8, Sectigo Certificate Services has implemented a hosted key attestation service to ensure the verification of hardware-backed keypairs during the issuance and management of Code Signing Certificates.
This comprehensive document outlines the specifics of Sectigo’s key attestation service and the hardware security modules (HSM) compatible with the successful verification of cryptographic data required for code signing certificate issuance.
The Sectigo key attestation service plays a crucial role by validating the cryptographic data and authorizing the issuance of both OV (Organization Validated) and EV (Extended Validation) code signing certificates.
Recommended: What is Key Attestation for Code Signing Certificates?
At present, Sectigo’s key attestation service supports the verification of Luna HSMs’ public key confirmation packages and YubiKey attestation certificates. These hardware devices have been rigorously tested and proven to meet the necessary requirements for code signing certificate validation.
Key Information of CA/B Forum
The section explains the content and intended audience, outlines the scope of the article, details of the key attestation, and the supported hardware devices for Sectigo’s key attestation service. It also mentions the supported operating systems and browsers.
Here’s a breakdown of the key points:
Assumptions and Intended Audience:
The text assumes the reader is familiar with the CA/B forum baseline requirements for Public CAs. The content is intended for IT or security administrators responsible for managing public certificates and hardware security modules (HSMs) within their company or organization.
Scope of the Blog:
The article focuses specifically on instructions for creating and verifying the key attestation cryptographic data for the supported HSMs.
Key Attestation:
Key attestation can be described as a method to prove possession of a cryptographic key by a cryptographic module to a third party. It is a process used to validate the authenticity and security of the cryptographic data.
Product Support Details:
Coming to listing the hardware devices currently supported by Sectigo’s key attestation service: the Luna Network Attached HSM (Version 7.x) and the YubiKey 5 FIPS Series. These devices have been tested and verified to work with the key attestation service.
Supported Operating System and Browsers:
The document advises referring to the vendor documentation for managing the HSMs’ operating systems. As for browsers, Sectigo’s key attestation service is compatible with Chrome, Firefox, and Edge.
Overall, the text provides background information, clarifies the intended audience, specifies the scope of the document, explains key attestation, and provides details about the supported hardware devices, operating systems, and browsers.
How to Get an Attestation Certificate for YubiKey 5?

The text explains the process and format of generating an attestation certificate for the YubiKey 5 FIPS Series USB tokens.
Here are the key points:
YubiKey 5 FIPS Series:
These USB tokens can generate an attestation certificate. The attestation certificate has the same key as the CSR (Certificate Signing Request) and is signed by the intermediate attestation certificate, which can be downloaded from the device.
The intermediate attestation certificate is, in turn, signed by the YubiKey private root certificate.
Attestation Package Format:
The YubiKey attestations are standard x.509 certificates that contain the key attestation. However, more than the attestation certificate is required to validate the attestation. The device’s intermediate attestation certificate is also required.
Base64 Encoding:
The key attestation service expects a base64 encoded blob that is created by concatenating the PEM encoded certificates. This means that the attestation certificate and the intermediate attestation certificate must be encoded in base64 format and combined into a single blob.
Recommended: What is a YubiKey? How Does it Work? [Detailed Guide]
Steps to Generate an Attestation Certificate & CSR using YubiKey Manager
To generate a CSR (Certificate Signing Request), attestation certificate, and get the intermediate attestation certificate for an ECC keypair using YubiKey Manager on Windows, follow these steps:
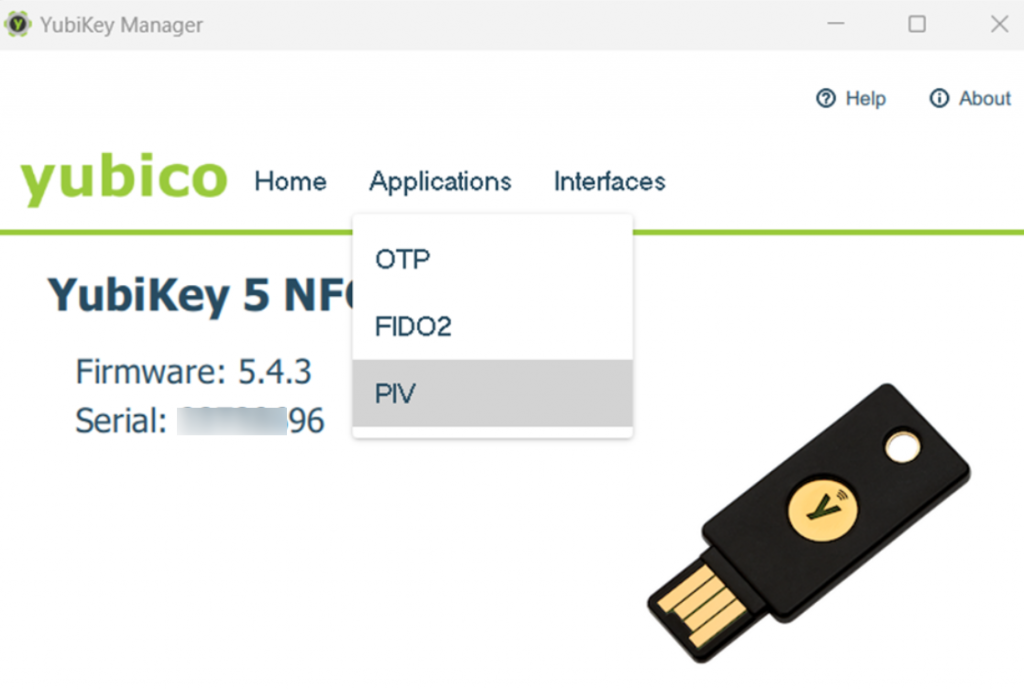
Step 1: Open YubiKey Manager and go to Applications > PIV3. Click on Certificates.
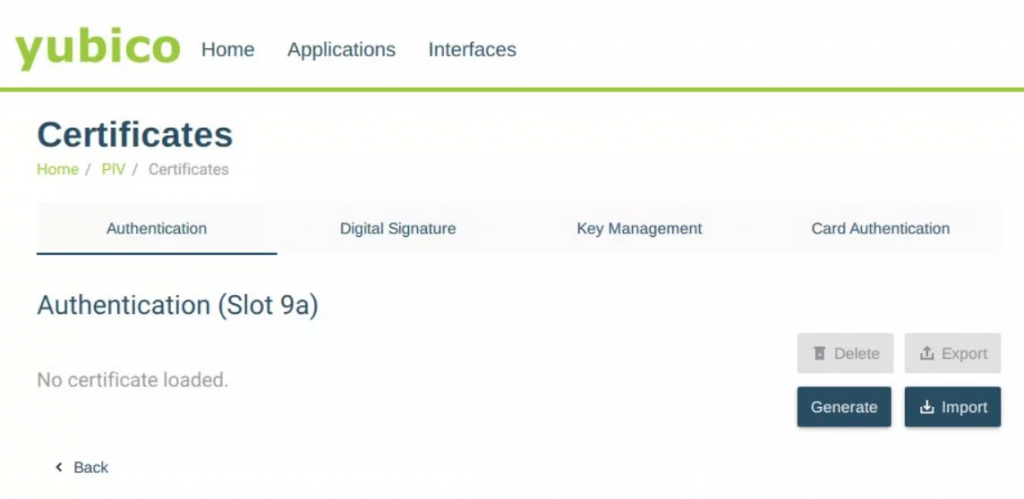
Step 2: Select Authentication (Slot 9a) and click Generate.
Step 3: Choose Certificate Signing Request (CSR) and press Next.
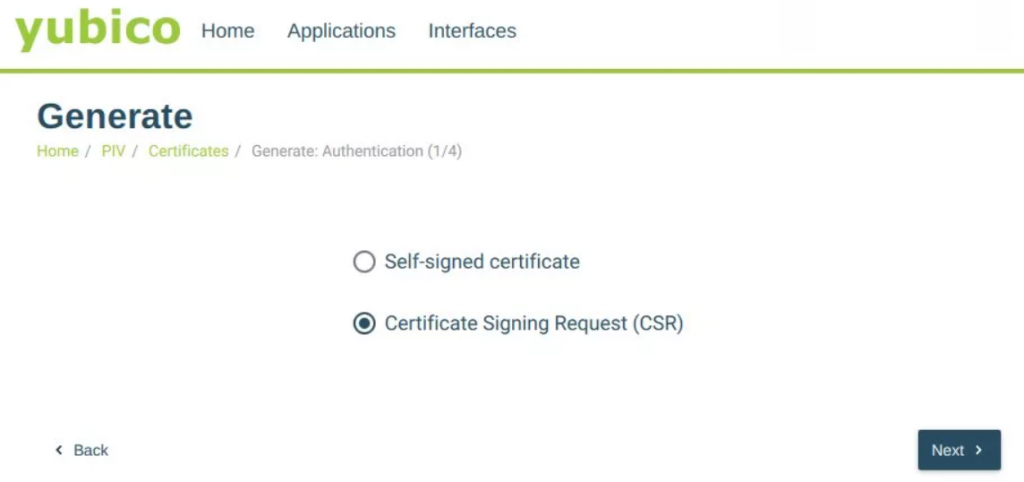
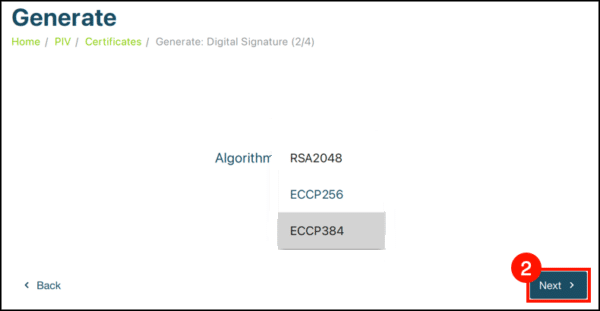
Step 4: Select an algorithm from the drop-down menu and click Next. For EV Code Signing Certificates, choose ECCP256 or ECCP384.
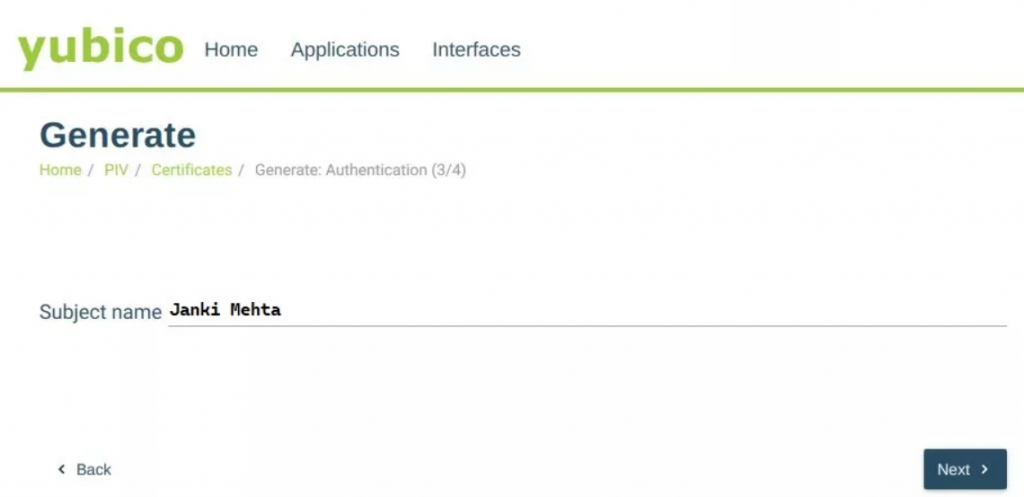
Step 5: Enter a Subject Name for the certificate and select Next.
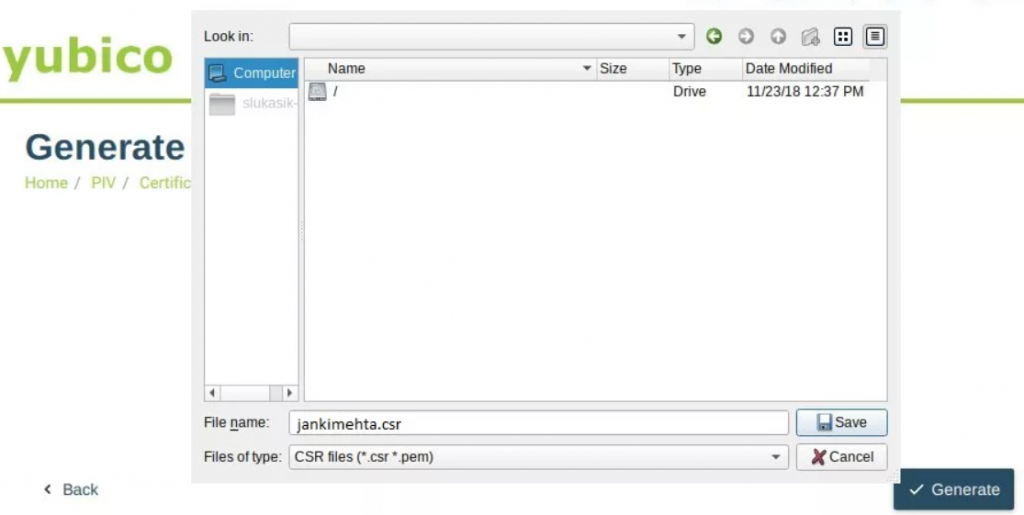
Step 6: Tap Generate and provide the necessary information, including the storage location for the CSR, management key, and PIN.
Step 7: Open a shell as Administrator and navigate to the YubiKey Manager directory. For example:
cd 'C:\Program Files\Yubico\YubiKey Manager\'Step 8: Run the following command to create the attestation certificate, replacing the path to save the attestation certificate as needed:
.\ykman.exe piv keys attest -F PEM 9a attestation.crtStep 9: Execute the following command to export the intermediate certificate:
.\ykman.exe piv certificates export -F PEM f9 intermediateCA.crtStep 10: The attestation service expects the attestation blob to be base64 encoded. Run the following commands to encode the attestation certificates as a single base64 encoded file:
NOTE: Certutil encode inserts a PEM header and footer that should not be included since Findstr removes them.
Combine the certificates into a single file:
type attestation.crt intermediateCA.crt > attestation.pemEncode the combined file in base64:
certutil -encode attestation.pem attestation.b64Remove the unnecessary PEM headers and footers:
findstr /v CERTIFICATE attestation.b64 > attestation.b64Step 11: Submit the CSR and the base64 encoded attestation to the Sectigo key attestation service for verification (From where you ordered).
Please note that these instructions are specifically for Windows. If using a different operating system, refer to YubiCo’s instructions for guidance.
Create CSR and Key Attestation for the Luna Network
Let us discuss the instructions for creating a Certificate Signing Request (CSR) and key attestation for the Luna Network Attached HSM 7.x.
Here, we will mention the attestation package format and provide details about generating a public key confirmation (PKC) file in an RSA key pair context. Coming to the breakdown of the key points:
Luna Network Attached HSM 7.x:

This section focuses on the Luna HSMs and their ability to generate a public key confirmation package (PKC) as the key attestation. The PKC is used to verify that a specific key pair was generated and stored within the Luna HSM.
Attestation Package Format:
Luna HSMs generate PKC files that are DER-encoded PKCS7 files. These files contain the key attestation. The key attestation service expects the PKC file to be encoded in base64 format.
PKC for RSA Keypair:
When generating a PKC for an RSA key pair, there are two possible formats mentioned:
- TC-Trust Center: The PKC contains three certificates in this format, and the certificate chain does not end with a root certificate.
- Chrysalis-ITS: The PKC contains five certificates in this structure, and the certificate chain ends with a root certificate.
Its’s recommended to select the Chrysalis-ITS format because there is documentation available from the vendor, which you can access here.
These pointers are overall mentioned for creating a CSR and key attestation using the Luna Network Attached HSM 7.x. It explains the format of the attestation package and provides options for generating PKC files in the context of an RSA key pair.
How to use the Chrysalis-ITS format for Generating CSR & PKC?
To generate a CSR (Certificate Signing Request) and PKC (Public Key Confirmation) in Chrysalis-ITS format, follow the steps below:
Step: 1 Launch the Luna remote client and log in to the Luna HSM.
Step 2: Generate an RSA key pair on a Luna Partition1 using the LunaCM2 utility. Execute the following command, replacing “LABEL” with the desired key pair identifier:
For Windows:
c:\ cd c:\Program Files\SafeNet\LunaClient
c:\Program Files\SafeNet\LunaClient\> lunacmFor Linux:
>cd /usr/safenet/lunaclient/bin
./lunacmcmu gen -modulusBits=3072 -publicExp=65537 -sign=T -verify=T -label=LABEL -extractable=falseNOTE: The parameters “-extractable=false” and “-sign=T” is mandatory for successful CSR generation since Luna won’t utilize this key to sign the CSR. And for code signing certificates, RSA key size must be at least 3072.
Step 3: Retrieve the handle numbers of the public and private keys by executing the following commands:
cmu list -class public -label=LABEL
cmu list -class private -label=LABELStep 4: Generate a CSR using the following command, replacing “ABC” and “XYZ” with the public and private key handles, respectively:
cmu requestcert -publichandle=ABC -privatehandle=XYZ -C=CA -L=Ottawa -O=Sectigo -CN="PKC Test Cert" -outputFile=rsacsr.pemStep 5: Generate a PKC by running the following command, replacing “ABC” with your public key handle and “attestation.p7b” with the desired file name:
cmu getpkc -handle=ABC -outputfile=attestation.p7b -pkctype=2 -verifyStep 6: Encode the attestation PKC file to base64 format. Use the following commands:
For Windows:
certutil -encode attestation.p7b attestation.b64
findstr /v CERTIFICATE attestation.b64 > attestation.b64For Linux:
base64 attestation.p7b > attestation.b64Step 7: Submit the generated CSR and base64-encoded attestation to the Sectigo key attestation service for verification of the HSM’s authenticity in issuing code signing certificates.
By following these steps, you can generate a CSR and PKC in Chrysalis-ITS format for use in the Sectigo key attestation service.

