What is a YubiKey? How Does it Work? [Detailed Guide]

Aren’t you a tech junkie? It does not matter anymore with YubiKey! But you must be thinking about how. This comprehensive guide dedicated to Yubikey will describe and update every necessary detail.
As a reader, you must seek a one-stop solution for all your needs and asks about this device. And we have made sure to be mindful of it and curate content below that can surely answer your questions and doubts.
What is a YubiKey?

YubiKey is a remarkable device designed to streamline the two-factor authentication process. It makes YubiKey incredibly user-friendly. Unlike traditional methods, YubiKey simplifies the process with a single press.
Each YubiKey is embedded with a unique code, vital in generating authentication codes that verify your identity. By pressing the button on your YubiKey, you gain seamless access to your accounts, making login procedures more efficient and secure.
Embrace the convenience and peace of mind that come with the straightforward functionality of YubiKey.
How YukiKey’s Two-Factor Authentication Enhances Security and Convenience?
It wouldn’t be wrong to say that relying solely on passwords for securing accounts is becoming increasingly risky. Passwords are vulnerable to hackers’ guessing tactics, and even strong ones lose their efficacy once they are leaked, which is a common occurrence.
Recognizing these limitations, two-factor authentication (2FA) emerged as a solution to bolster account security.
Two-factor authentication requires two elements for signing in your password, as usual, and an additional factor that verifies your identity.
You may already be familiar with two standard methods of implementing 2FA:
SMS or Email Codes:
Applications send you a code through SMS or email, which you must enter to complete the login process. This method is convenient since it requires no additional software or hardware.
However, it is considered less secure as email and SMS transmissions are encrypted and resistant to compromise.
Authentication Apps:
Certain apps prompt you to enter a code generated by an authentication app installed on your phone, such as Google Authenticator or Authy.
This method is more secure than relying on SMS or email codes, but it can be less convenient as it involves retrieving your phone, opening the app, and manually entering the code.
Hardware authentication is a third and superior approach to two-factor authentication that YubiKey exemplifies. With hardware authentication, applications prompt you to connect a YubiKey device to your device and press a button. The YubiKey then transmits a unique, lengthy code to verify your identity.
This method provides increased security due to the complexity and length of the codes generated. Moreover, it offers enhanced convenience, eliminating the need to enter codes manually. By embracing 2FA, you can safeguard your accounts effectively while enjoying a streamlined authentication process.
What is YubiKey Used for?
We already understand that YubiKey is a versatile device with various applications across domains. Check the following to explore some common uses of YubiKey.
No Password Login:
YubiKey supports password-free login, offering a more convenient and secure alternative to traditional password-based authentication. With public-key cryptography, YubiKey enables users to log in to supported services without remembering or entering a password.
Secure Remote Access:
You can get more secure remote access to systems and networks. It provides extra authentication, ensuring only authorized individuals with the physical YubiKey can access sensitive resources remotely.
Identity Verification:
YubiKey is also a reliable identity verification tool. It helps to verify users during sensitive operations, such as online transactions, digital signatures, and secure document sharing. It overall aids in mitigating the risks of unauthorized access and fraudulent activities.
Password Managers:
Now, integrate with password manager applications, such as LastPass and KeePass, adding an extra layer of security to password storage and retrieval. The YubiKey is the second factor in the authentication process, protecting access to critical password vaults.
Hardware Encryption:
Some YubiKey models support hardware-based encryption. They can be used to encrypt files, emails, and other sensitive data, providing an additional level of protection against unauthorized access or data breaches.
Online Services and Platforms:
YubiKey is compatible with various online services and platforms, prioritizing security. This includes popular platforms like Google, Microsoft, Dropbox, and GitHub, allowing users to strengthen their account security with YubiKey authentication.
Compliance Requirements:
You can also fulfill the compliance requirements of organizations and industries that demand robust security measures. Since YubiKey helps you meet regulatory standards and best practices for data protection and access control. People in the financial, healthcare, and government sectors can take most of the advantages.
How does Yubikey work?
Now that we know YubiKey quite well let us understand its functioning. YubiKey operates based on two-factor authentication (2FA) principles and cryptographic protocols. So, we will quickly move on to a simplified explanation of YubiKey’s working mechanism:
YubiKey is a small hardware device that typically connects to a computer or mobile device via a USB port, although some models also support wireless connectivity, like NFC (Near Field Communication).
Each YubiKey is manufactured with a unique identifier and cryptographic keys embedded in its firmware during production. This ensures that every YubiKey has a distinct identity.
PRO TIP:
Before using YubiKey, it must be initialized and associated with the user’s accounts or services supporting YubiKey authentication. This typically involves registering YubiKey’s identity with the desired services or applications.
About the Authentication Process of YubiKey
When the user attempts to access a protected account or service, the authentication process begins:
User Action: The user initiates the authentication process by inserting or tapping the YubiKey device or bringing it close to the NFC-enabled device, depending on the YubiKey model and connectivity option.
Recommended: Set Up Your YubiKey for Two-Factor Authentication for GitHub Security
One-Time Password (OTP):
The YubiKey generates a one-time password (OTP), a time-limited code based on YubiKey’s unique identity and secret keys. The OTP is not stored or transmitted to the server.
Delivery Method:
The YubiKey delivers the OTP to the device through a simulated keyboard input or wireless communication, depending on the device and operating system. It mimics the keystrokes of the OTP, ensuring it reaches the correct input field without compromising security.
Recommended: Code Signing Certificate Delivery Methods (Private Key Storage Options)
Verification:
The server or application receiving the OTP verifies its authenticity by decrypting it using the secret keys stored in the server’s database and YubiKey’s public key. If the decryption process succeeds, the authentication is deemed valid.
Robust Security:
YubiKey employs industry-standard cryptographic algorithms and protocols, including asymmetric encryption, public-key cryptography, and secure key storage. This ensures the integrity and confidentiality of the authentication process. It also protects against phishing, password theft, and man-in-the-middle attacks.
Recommended: Token Based Code Signing Certificates at Cheapest Price!
Compatibility:
YubiKey is designed to work seamlessly with various online services, platforms, and applications that support 2FA or YubiKey authentication. Major service providers and platforms, such as Google, Microsoft, Dropbox, and many others, have integrated support for YubiKey.
Combining the above factors helps YubiKey provide a reliable and convenient means of authentication. It enhances security by requiring the physical presence of the YubiKey device. It also makes it significantly more difficult for unauthorized individuals to access protected accounts or systems.
What if Yubikey is Lost: Troubleshooting Methods
If your YubiKey is lost, we are What if Yubikey is lost: Troubleshooting Methodswith the steps you can take to ensure the security of your accounts and minimize the risk of unauthorized access.
Deactivate your YubiKey Device:
For precaution, you should immediately deactivate or remove the lost YubiKey from any associated accounts or services. Most platforms that support YubiKey authentication provide options to manage or remove YubiKeys from your account settings.
Change the Password:
Modifying the passcodes of accounts linked to the lost YubiKey is a must. This adds a layer of security, as the lost YubiKey alone can only access your accounts with the corresponding password.
Recommended: How to Keep Your Digital Signature Credentials Safe with YubiKey?
Enabling Backup Authentication:
As mentioned earlier, YubiKey is often used as a second factor in two-factor authentication. In case of a lost YubiKey, ensure alternative backup authentication methods are enabled, such as SMS codes, email verification, or authentication apps. This allows you to access your accounts securely while replacing the lost YubiKey.
Contact Service Providers:
If your YubiKey is associated with specific online services or platforms, we advise you to contact that support or security team. Inform them about the situation and follow their recommended procedures for handling lost or compromised authentication devices.
Obtain a Replaced YubiKey:
Once you have taken the necessary precautions and ensured the security of your accounts, you can obtain a replacement for your YubiKey device.
Contact the vendor or retailer from which you originally purchased the YubiKey, or visit the official Yubico website, to purchase a new device. Ensure you follow the setup and registration process to associate the new YubiKey with your accounts.
QUICK NOTE: The security implications of a lost YubiKey depend on the specific configurations and protections you have implemented. It is essential to act promptly, follow the recommended steps provided by service providers, and maintain reasonable security practices to protect your accounts even when you lose your YubiKey device.
Setting up Your YubiKey: A Step-wise Tutorial
Setting up your YubiKey is Setting up Your YubiKey: A Step-wise Tutorial, similar to configuring app-based two-factor authentication. Follow the steps below to begin using your YubiKey device:
Connect Your YubiKey:
Plug your YubiKey into a USB port on your device. Ensure it is properly connected and recognized.
Visit Yubico.com/Setup:
Open your web browser and navigate to Yubico’s official website. Go to the Yubico.com/setup page.
Select Your Device:
On the Yubico setup page, locate and click on your specific YubiKey model from the list of supported devices.
Choose Apps to Secure:
Review the available list of supported applications and services. Pick the app you want to secure with YubiKey.
Follow the Instructions:
Follow the provided instructions specific to the chosen application. We can take Google, for example. Click on the instructions for adding your YubiKey to your Google account.
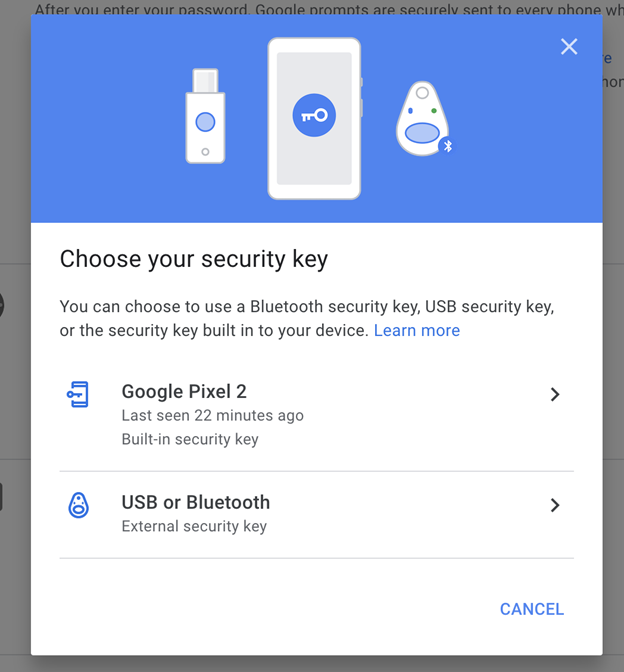
Authenticate with YubiKey:
The process may depend on the app you use. But for Google, you’ll be prompted to plug in your YubiKey and press the button on the device.
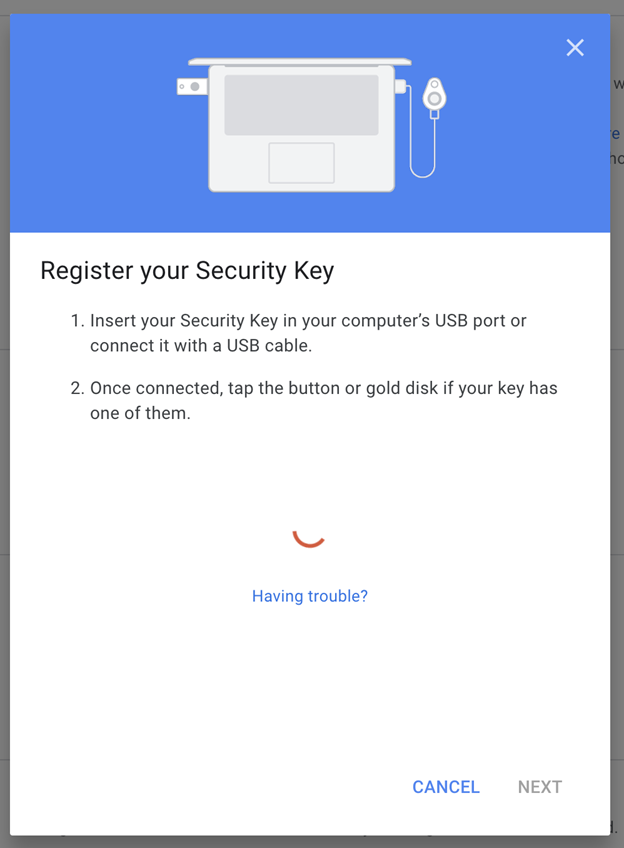
Grant Browser Permission:
Your web browser might ask for permission to access your YubiKey. Grant the necessary permission to proceed.
Confirmation and Optional Naming:
Once the setup is complete, you should receive a confirmation message indicating that your YubiKey is successfully configured.
PRO TIP: You can consider assigning a name to your YubiKey. Why? Because it is helpful if you use multiple keys.
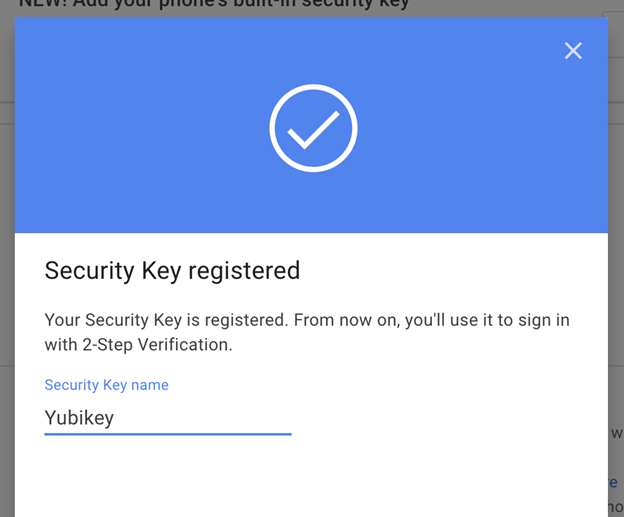
Repeat for Other Accounts: Repeat the setup process for each account you wish to secure with your YubiKey. This ensures consistent and robust protection across multiple platforms.
So, the above steps can help you log in YubiKey securely to your Google account on any device.
QUICK NOTE: Apply this setup process to all the accounts you want to safeguard using your YubiKey. Enjoy the enhanced security and peace of mind provided by your YubiKey authentication.
YubiKey 5 FIPS Series: All you need to Know!
Over time, YubiKey has gained recognition as a leading provider of hardware-based authentication solutions. It offers a range of key series and devices designed to bolster security across various applications.
Let’s dive into the different offerings and explore their features.

YubiKey 5 Series:
The YubiKey 5 Series represents the flagship lineup, providing robust authentication capabilities for individuals and organizations. These devices support multiple authentication protocols, including OTP, FIDO2, smart cards, and more, ensuring versatile compatibility with a wide range of services.
YubiKey 5 FIPS Series:
The YubiKey 5 FIPS Series is designed to meet Federal Information Processing Standards (FIPS) for environments with stringent regulatory requirements. These devices adhere to the rigorous security guidelines mandated by government and industry regulations.
YubiKey Bio Series:
YubiKey Bio Series incorporates biometric authentication, adding an extra layer of security. With built-in fingerprint sensors, these keys provide a seamless and secure user experience by combining something the user knows (e.g., a password) with something the user is (biometric data).
Security Key Series:
The Security Key Series offers a simplified yet effective authentication solution. These keys support FIDO2 and WebAuthn protocols, making them ideal for passwordless login and strong authentication across multiple platforms.
YubiKey 5 CSPN Series:
The YubiKey 5 CSPN (Certification de Sécurité de Premier Niveau) Series complies with French security certification standards. These keys provide high-level security assurance and are commonly used in French government and enterprise settings.
YubiHSM 2 & YubiHSM 2 FIPS:
In addition to the YubiKey lineup, Yubico offers the YubiHSM 2 and YubiHSM 2 FIPS. These hardware security modules (HSMs) provide cryptographic protection and key management capabilities, safeguarding sensitive data and strengthening overall security infrastructure.
What is a YubiKey Authenticator?
The YubiKey Authenticator is a software application that complements YubiKeys, enabling easy configuration and management of OTP credentials. It allows users to generate OTP codes for supported services without the need for additional hardware or devices.
YubiKey’s range of key series and the YubiHSM 2 devices offer comprehensive solutions for varying security needs. Whether it’s the versatile YubiKey 5 Series, FIPS-compliant options, biometric authentication with the Bio Series, simplified Security Key Series, CSPN-certified keys, or the YubiHSM 2 for cryptographic operations, Yubico caters to a diverse range of security requirements.
Wrapping up
Individuals and organizations can now easily fortify their systems, protect sensitive data, and mitigate the risks associated with password-based authentication. But how? Of course, by leveraging YubiKey’s hardware-based authentication and cryptographic capabilities.
With YubiKey, enhanced security is within reach, making it a go-to choice for those prioritizing robust and user-friendly authentication solutions.
Recommended: How To Use YubiKey To Sign Windows Executable File?
Secure your Code Signing Certificate with YubiKey
Code Signing Certificates ensure the software integrity and authenticity. Whereas YubiKey is a hardware-based authentication device for code signing certificates security.
