Set Up Your YubiKey for Two-Factor Authentication for GitHub Security

Compatible Devices and Prerequisites to Set Up YubiKey
To utilize the YubiKey for authentication, you must ensure a compatible browser version is installed on your computer.
The following browsers support the use of YubiKey:
Google Chrome:
YubiKey support has been available since version 38.
Mozilla Firefox:
YubiKey support has been available with the starting version 60.
Opera:
YubiKey support has been available since version 40.
Microsoft Edge:
YubiKey support has been available since the beginning of build 17723.
QUICK NOTE: We advise you to use the latest browser version of any browser that you are selecting.
Apart from having a compatible browser, there are a few other requirements to use YubiKey effectively:
Computer with a USB port:
YubiKey is a physical device that connects to your computer via a USB port. Ensure that your computer has an available USB port.
U2F-enabled Security Key:
You will need a U2F-enabled security key to use YubiKey. Some compatible YubiKey model include YubiKey 5 NFC FIPS..
Mobile Phone for OTP:
During the initial setup and backup process, you will require a mobile phone to receive one-time passwords (OTP) via SMS. Alternatively, you can install Google Authenticator on your phone to receive OTPs through the application.
GitHub Account:
To utilize YubiKey for authentication on GitHub, you’ll need an active GitHub account.
Guarantee that you meet all these requirements to set up and use YubiKey for authentication purposes effectively.
How to Configure to YubiKey for GitHub?
By following these guidelines, you can enhance the security of your online accounts, including your GitHub account, by leveraging the capabilities of YubiKey.
If you need to enable two-factor authentication for your GitHub account, follow the steps below. If you have already enabled two-step verification, proceed to the second method.
METHOD 1: To Enable a Two-factor Authentication
Step 1: Sign in to your GitHub account.
Step 2: Click on your profile picture in the top right corner of the screen.
Step 3: Select “Settings” from the dropdown menu.
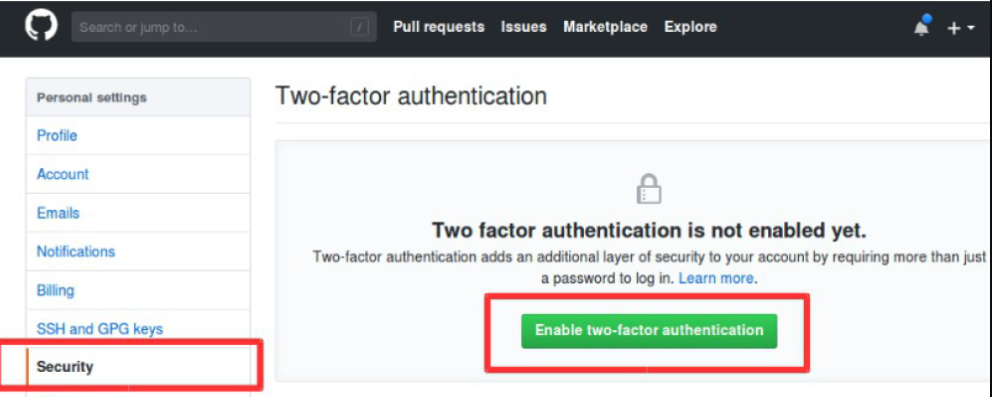
Step 4: In the left pane, choose “Security.”
Step 5: Click on “Enable two-factor authentication.”
Step 6: Select a method for obtaining one-time passwords:
Set up with an App:
Install a TOTP app like Google Authenticator, 1Password, Authy, or LastPass Authenticator.
Once installed, click “Set up using an app” and save your recovery codes. You can choose to download, print, or copy the recovery codes.
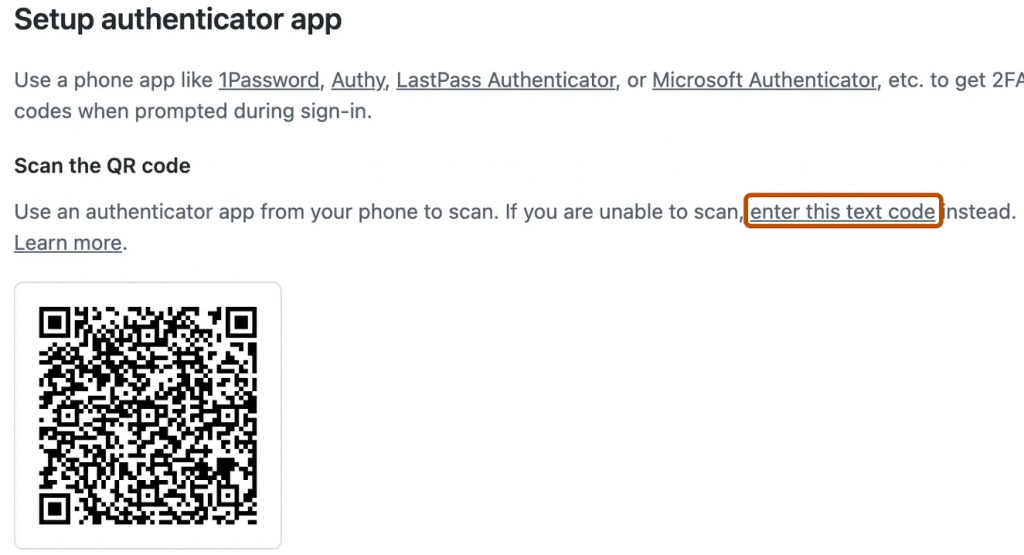
Next, scan the QR code with your TOTP app or manually enter the code if scanning is impossible. Enter the generated code from the app on the GitHub two-factor authentication page and click “Enable.”
Set up using SMS for Login:
If you can’t use a TOTP app, click “Set up using SMS.” Save your recovery codes by downloading, printing, or copying them.
Enter your country code and phone number, then click “Send authentication code.” Enter the code received via SMS on the GitHub two-factor authentication page and click “Enable.”
After saving your recovery codes and enabling two-factor authentication, it is recommended to sign out and sign in again.
If you encounter any issues, such as a forgotten password or an incorrect email address, you can use the backup codes to access your account and resolve the problem.
Next Step: How To Add YubiKey for Two-Factor Authentication?
Once you have set up two-factor authentication using the mobile app or SMS, you can add a YubiKey hardware security key as an additional authentication factor on GitHub.
Step 1: Sign in to your GitHub account.
Step 2: Click on your profile picture in the top right corner of the screen.
Step 3: Select “Settings” from the dropdown menu.
Step 4: In the left pane, choose “Security.”
Step 5: To the right of “Security keys,” click “Add.”
Step 6: Insert your YubiKey into a USB port.
Step 7: In the “Security keys” section, click “Register new device.”
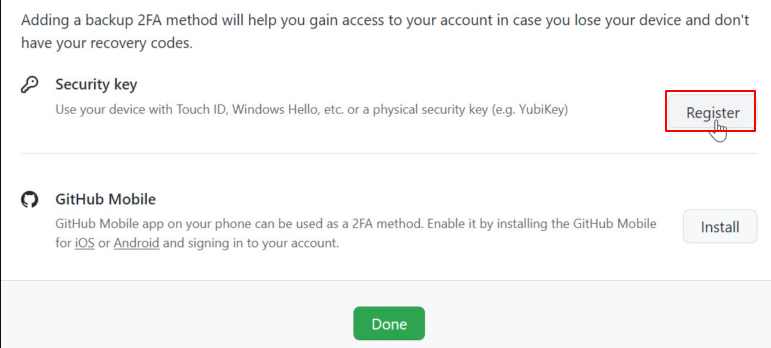
Step 8: Provide a nickname for your YubiKey and click “Add.”
Step 9: Wait for your YubiKey to start flashing, then tap the gold button or edge.
Voila! You’ve successfully added a YubiKey security key to your GitHub account.
So, you can conveniently log into your GitHub account with the added security of two-factor authentication. Now you know what to do!
Log in, by simply entering your username and password. Then touch the button or the gold-colored edge on your YubiKey.
Secure guard your Code Signing Certificate with YubiKey
Code Signing Certificates ensure the software integrity and authenticity. Whereas YubiKey is a hardware-based authentication device for code signing certificates security.
