Comprehensive Guide on Azure Key Vault: Key Management and Difference

Discover in this article, What is Azure, its types, and the difference between standard and premium Azure key vaults. Learn about Managed HSM Vs. Vault, features, and compatibilities.
What are Azure Key Vault and Managed HSMs?
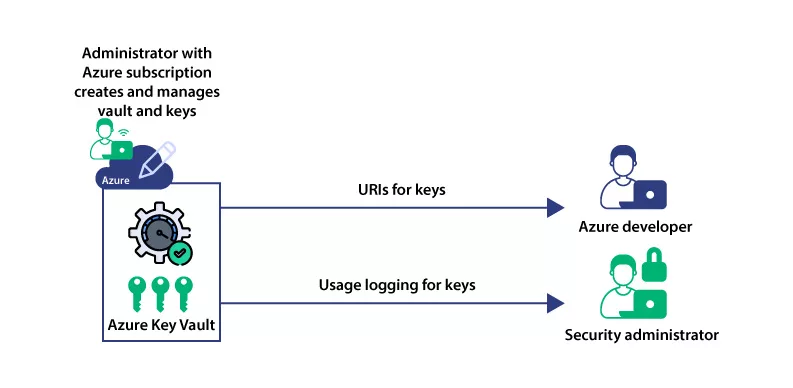
Azure Key Vault is a solution for cloud-based key management offering two types of resources to store and manage cryptographic keys. Vaults support software-protected and HSM-protected keys, while Managed HSMs only support HSM-protected keys.
They provide a low-cost, easy-to-deploy, multi-tenant, zone-resilient (where available), highly available key management solution suitable for most common cloud application scenarios.
| Name of Product | Validation Needs | Issuance Time | Our Price |
|---|---|---|---|
| Azure Key Vault Cloud Code Signing Certificate | Business | 1-5 Days | $369.99/yr |
| Azure Key Vault EV Cloud Code Signing Certificate | Extended | 3-5 Days | $519.99/yr |
On the other hand, Managed HSM provides single-tenant, zone-resilient (where available), highly available HSMs to store and manage cryptographic keys.
This makes it most suitable for applications and usage scenarios that handle high-value keys. It also helps to meet the most stringent security, compliance, and regulatory requirements.
Azure Key Vault supports encryption keys and key operations, including creating, reading, listing, and updating. It also offers simplified administration of application secrets, making securing and controlling access to tokens, passwords, certificates, API keys, and other secrets easy.
Types of Resources Azure Key Vault
The text describes two types of resources Azure Key Vault provides for storing and managing cryptographic keys: Vaults and Managed HSMs.
Vaults:
Vaults are a low-cost, easy-to-deploy solution for key management. They are multi-tenant, meaning multiple users can utilize the vault. Vaults are zone-resilient, meaning they can handle failures in specific geographical zones.
Vaults support two types of keys:
Software-protected keys:
They are stored and managed by software-based mechanisms within the vault. They offer a secure way to handle keys but need to provide the highest level of physical protection.
HSM-protected Keys:
Hardware Security Module (HSM) is a physical device that provides higher security for cryptographic keys. HSM-protected keys are stored and managed within the vault using an HSM. They offer enhanced protection against physical attacks and are suitable for scenarios that require more robust security measures.
Recommended: Code Signing Using Azure Key Vault (Cloud HSM)
Managed HSMs:
Managed HSMs are a specialized offering within Azure Key Vault that provides single-tenant HSMs for key storage and management. They are also zone-resilient and highly available. Managed HSMs are suitable for applications and usage scenarios that handle high-value keys, such as sensitive financial or personal data.
They are designed to meet the most stringent security, compliance, and regulatory requirements. Managed HSMs offer the highest level of security and are recommended when the utmost protection is necessary.
What is the Difference between Standard and Premium Azure Key Vault?
Azure Key Vault is a cloud service provided by Microsoft Azure that allows you to securely store and manage cryptographic keys, certificates, and secrets.
Azure Key Vault offers two tiers: Standard and Premium. The main differences between the two tiers are in features, capabilities, and pricing.
Features and Capabilities:
- Standard Tier: The Standard tier provides core Key Vault functionalities, such as key management, secret storage, and certificate management. It supports the creation and storage of keys and secrets and the ability to generate and manage certificates.
- Premium Tier: The Premium tier includes all the features and capabilities of the Standard tier but with additional advanced features. It provides enhanced scalability, higher throughput, and lower latency for cryptographic operations. The Premium tier also offers features like HSM (Hardware Security Module) isolation, which provides additional protection for cryptographic keys.
Performance and Scalability:
- Standard Tier: The Standard tier is designed for general-purpose key storage and management. It offers a standard level of performance and scalability suitable for most common scenarios.
- Premium Tier: The Premium tier is optimized for high-performance scenarios that require increased scalability, throughput, and lower latency. It is ideal for applications with demanding cryptographic workloads or requiring strict SLAs (Service Level Agreements).
Pricing:
- Standard Tier: The Standard tier costs less than the Premium tier. It provides cost-effective key storage and management for most scenarios.
- Premium Tier: The Premium tier is priced higher than the Standard tier due to its advanced features and enhanced performance capabilities. It offers higher scalability and performance but comes at a higher cost.
It’s essential to consider your specific requirements, performance needs, and budget when choosing between the Standard and Premium tiers of Azure Key Vault.
The Premium tier might be better if you have demanding cryptographic workloads. It requires HSM isolation or needs higher scalability and performance guarantees. Otherwise, the Standard tier offers a cost-effective general key storage and management solution.
Note: Certificate Authority Like DigiCert Code Signing Certs support Azure Vault Standard and Premium tier! To Get Benefits of this, You can Purchase DigiCert EV Code Signing Certificate from us!

Cryptographic Keys in Azure Key Vault and Managed HSM
The provided text contains explanations and details about cryptographic keys in Azure Key Vault and Managed HSM.
Let’s break it down:
Cryptographic Keys in Key Vault:
In Azure Key Vault, cryptographic keys are represented as JSON Web Key (JWK) objects. JWK is a JSON-based format for representing cryptographic keys. It provides a standard way to express key parameters and properties.
JSON and JOSE specifications:
The text mentions several specifications related to JSON Web Keys. These include JSON Web Encryption (JWE), JSON Web Algorithms (JWA), and JSON Web Signature (JWS). These specifications define standards for encrypting, signing, and verifying JSON-based data.
Azure Key Vault Uses:
Key types Unique to Azure Key Vault and Managed HSM:
The JWK/JWA specifications used in Azure Key Vault and Managed HSM are extended to support critical types specific to these implementations. Azure Key Vault and Managed HSM offer additional key types beyond the standard specifications.
HSM-Protected Keys:
HSM-protected keys, also known as HSM keys, are processed within a Hardware Security Module (HSM). HSMs provide high security for cryptographic operations and ensure the keys remain within the HSM protection boundary. This adds an extra layer of security to the keys.
Managed HSM Uses:
FIPS 140-2 validated HSMs:
Azure Key Vaults use HSMs that are FIPS 140-2 Level 2 validated. FIPS (Federal Information Processing Standard) 140-2 is a U.S. government standard that specifies security requirements for cryptographic modules. Level 2 validation ensures the HSMs meet specific security standards.
Managed HSM and FIPS 140-2 Level 3:
Managed HSM in Azure utilizes FIPS 140-2 Level 3 validated HSM modules. Level 3 validation is a higher level of security than Level 2 and includes additional physical security requirements.
Each Managed HSM pool is an isolated single-tenant instance with its security domain, providing complete cryptographic isolation from other HSMs in the same hardware infrastructure.
Key Protection and Import:
Keys in Azure Key Vault and Managed HSM can be imported in different formats, such as RSA, EC, and symmetric keys. These keys can be imported in a mild form or exported from a supported HSM device. The BYOK (bring your key) specification allows secure transportation of key material into Managed HSM pools.
Managed HSM Vs. Azure Vault: Key Difference
Here are some key types and protection methods supported by Azure Key Vault and Managed HSM:
Azure Key Vault:
- RSA Keys: Azure Key Vault supports RSA (Rivest-Shamir-Adleman) keys. RSA is a widely used asymmetric encryption algorithm that relies on the mathematical properties of prime numbers.
- EC Keys: Azure Key Vault also supports EC (Elliptic Curve) keys. EC keys use elliptic curve cryptography, offering strong security with smaller key sizes than RSA.
Managed HSM:
- RSA Keys: Managed HSM extends the support for RSA keys. You can create, import, and manage RSA keys within a Managed HSM. RSA keys are commonly used for asymmetric encryption, digital signatures, and key exchange.
- EC Keys: Like Key Vault, Managed HSM supports EC keys. You can work with elliptic curve cryptography and perform operations using EC keys within a Managed HSM.
- Symmetric Keys: Managed HSM supports symmetric keys using a single shared secret for encryption and decryption. They are typically operated for efficient bulk data encryption and decryption.
Key Protection Methods:
Both Azure Key Vault and Managed HSM offer robust protection methods for cryptographic keys:
Software-protected Keys:
Keys can be stored and managed in a software-protected environment. This means the keys are securely stored within the Key Vault or Managed HSM using various encryption and access control mechanisms. Software-protected keys leverage the security features provided by the cloud service itself.
HSM-protected Keys:
HSM-protected keys are processed within a dedicated Hardware Security Module (HSM). HSMs provide a highly secure and tamper-resistant environment for key operations.
HSMs ensure that the keys never leave the HSM boundary and provide additional security measures like physical protection, secure key storage, and hardware-level security features.
Recommended: What is a Cloud Hardware Security Module? How to Choose the Right Cloud HSM?
Azure Key Vault and Managed HSM allow you to generate, import, and manage these key types while providing additional security and management capabilities.
Using Key Vault or Managed HSM depends on your application’s specific security. It also varies based on compliance requirements and the level of control you need over the underlying hardware and security boundaries.
Comparison Table of Azure Key Vault and Managed HSM
| TYPE | HSM-PROTECTED KEYS | SOFTWARE-PROTECTED KEYS | COMPLIANCE | USAGE SCENARIOS |
| Vaults | Available with Premium SKU | Available | Compliant with industry standards | General key storage and management |
| Managed HSMs | Available | Not applicable | FIPS 140-2 Level 3 validated HSMs | High-security and compliance requirements, dedicated HSM control |
Here’s a breakdown of each category.
HSM-protected keys:
Vaults offer the option for HSM-protected keys, specifically available with the Premium SKU. HSM-protected keys are processed within an HSM, providing an additional layer of security.
Managed HSMs fully support HSM-protected keys. All keys within a Managed HSM are processed within an HSM, ensuring the highest level of security.
Software-protected Keys:
Vaults support software-protected keys, where keys are stored and managed within the secure software environment of the Azure Key Vault.
Software-protected keys do not apply to Managed HSMs since all keys within a Managed HSM are processed within the HSM boundary.
Compliance:
Vaults in Azure Key Vault are designed to comply with industry standards, including regulatory requirements such as GDPR, HIPAA, and ISO certifications.
Managed HSMs utilize FIPS 140-2 Level 3 validated HSM modules compliant with stringent security standards.
Usage Scenarios:
They are suitable for general key storage and management scenarios. They balance security and ease of use, making them suitable for various applications.
Managed HSMs are ideal for high-security and compliance-sensitive scenarios that require dedicated control over the HSM and the highest level of security for cryptographic operations.
QUICK NOTE: While Vaults offer HSM-protected keys with the Premium SKU option, Managed HSMs provide a dedicated HSM environment with exclusive control and higher security assurance.
The choice between Vaults and Managed HSMs depends on your application’s specific security, compliance, and control requirements.
Concepts of Platform-Managed Keys and Customer-Managed Keys
The provided text explains the concepts of platform-managed keys (PMKs) and customer-managed keys (CMKs) in Azure, including the distinction between them and their usage scenarios. Let’s break it down:
Platform-Managed Keys (PMKs):
- PMKs are encryption keys entirely generated, stored, and managed by Azure. Customers do not have direct interaction with PMKs.
- PMKs are used by default for Azure Data Encryption-at-Rest. This means that Azure automatically handles the encryption of data stored within Azure services using PMKs without customer intervention.
Customer-Managed Keys (CMKs):
- CMKs are encryption keys that customers can create, read, update, delete, and administer. They provide customers with more control over their encryption keys.
- CMKs are typically stored in a customer-owned key vault or a hardware security module (HSM), both managed by the customer.
- Bring Your Own Key (BYOK) is a CMK scenario where customers import (bring) their keys from an external storage location into Azure Key Vault, a key management service in Azure.
Key Encryption Key (KEK):
- A specific type of customer-managed key is the “key encryption key” (KEK). A KEK is a primary key that controls access to one or more encryption keys that are themselves encrypted.
- KEKs provide an additional layer of security by encrypting the encryption keys, thereby protecting them from unauthorized access.
Storage of Customer-Managed Keys:
- CMKs can be stored either on-premises or, more commonly, in a cloud key management service.
- Cloud key management services, like Azure Key Vault, offer secure and scalable storage for CMKs, allowing customers to manage their keys centrally and leverage the benefits of cloud-based security services.
So, basically, Azure provides two types of encryption keys. The first is platform-managed keys (PMKs) handled entirely by Azure. And the other is customer-managed keys (CMKs) that give customers control over key management.
CMKs can be stored in customer-owned key vaults or HSMs, and a specific type of CMK is the key-encryption key (KEK).
As a customer, you can store your CMKs on-premises or use cloud-based key management services like Azure Key Vault.
Securing Keys in the Cloud with Key Management Services
Azure provides a range of key management services designed to store and manage keys in the cloud securely. These services include Azure Key Vault, Azure Managed HSM, Dedicated HSM, and Payments HSM.
Each option has distinct features and is suitable for different scenarios, considering factors such as FIPS compliance level, management requirements, and intended use cases.
Azure Key Standard and Premium tiers:
Azure Key Vault is available in both Standard and Premium tiers. It offers a secure and scalable solution for key storage and management.
With the Standard tier, you can benefit from key management capabilities that meet industry standards. The Premium tier provides additional features and performance enhancements for demanding workloads.
Managed HSM:
Azure Managed HSM provides a dedicated Hardware Security Module (HSM) environment, ensuring the highest security and control over key operations. It leverages FIPS-compliant Level 3 validated HSM modules, making it ideal for applications with stringent compliance requirements.
Dedicated HSM:
Azure Dedicated HSM offers a dedicated, single-tenant HSM instance for organizations that require even more control and isolation. This option provides enhanced security and isolation, protecting keys within a dedicated hardware infrastructure.
Payments via HSM:
Azure Payments HSM is explicitly designed for applications that require secure payment processing. It offers a secure environment for cryptographic operations related to payment systems and adheres to industry standards and regulations.
With these key management services, Azure enables organizations to choose the option that best fits their security, compliance, and management needs.
Whether it’s the scalable and versatile Azure Key Vault, the dedicated control of Azure Managed HSM and Dedicated HSM, or the specialized security of Azure Payments HSM, Azure provides a comprehensive set of tools to protect and manage keys in the cloud.
Azure Key Vault’s Price Structure:
The pricing structure for Azure Key Vault varies depending on the tier. The Standard and Premium tiers are transaction-based, meaning you are billed based on the number of transactions performed.
Additionally, there is a monthly charge per key for premium hardware-backed keys. On the other hand, Managed HSM, Dedicated HSM, and Payments HSM are billed at a fixed hourly rate, as they are always-in-use devices.
You can refer to the specific pricing pages for Key Vault, Dedicated HSM, and Payment HSM for detailed pricing information.
What are the Limits in Azure’s Service?
Managed HSM, Dedicated HSM, and Payments HSM offers dedicated capacity, ensuring consistent performance.
In contrast, Key Vault Standard and Premium are multi-tenant offerings with throttling limits. To understand the service limits for each offering, you can refer to the Key Vault service limits details.
Encryption-At-Rest with Integration:
Both Azure Key Vault and Azure Key Vault Managed HSM provide integration with Azure Services and Microsoft 365 for Customer Managed Keys.
This integration allows customers to use their keys stored in Azure Key Vault and Azure Key Managed HSM for encryption-at-rest of data within these services.
On the other hand, Dedicated HSM and Payments HSM are Infrastructure-as-a-Service (IaaS) offerings and do not offer the same level of integration with Azure Services.
To get a comprehensive overview of encryption-at-rest with Azure Key Vault and Managed HSM, refer to the Azure Data Encryption-at-Rest anytime.
About APIs:
Dedicated HSM and Payments HSM support a range of APIs, including PKCS#11, JCE/JCA, and KSP/CNG. However, Azure Key Vault and Managed HSM do not support these APIs.
Instead, Azure Key Vault and Managed HSM utilize the Azure Key Vault REST API and offer SDK support for developers. If you need more information on working with the Azure Key Vault API, you can consult the Azure Key Vault REST API Reference documentation.
By providing transparent and detailed information about pricing, service limits, encryption-at-rest capabilities, and APIs, Azure ensures customers can make informed decisions about the appropriate essential management services that best meet their specific requirements.

