What is Azure Security? 7 Best Practices for Microsoft Azure Active Directory (AD)

Organizations are increasingly adopting cloud technologies, mainly to secure their sensitive data.
But are these cloud infrastructures so secure?
We all know that companies worldwide are challenged by the ongoing volume of evolving security threats and by retaining qualified professionals to respond to these threats.
On average, large organizations get approximately 17,000 security alerts a week, and it takes 99 days to discover security breaches.
And to your surprise, the average cost of a cybersecurity breach is a whopping $4.45 million, a 15% increase over 3 years. In addition to confidential information, reputation, time, investment, fines, and legal fees are all at stake.
So, how can organizations be sure to avoid costly data breaches and get top-notch security in such cloud environments?
You’re in safe hands with Azure Active Directory, the security key to Microsoft 365 cloud platforms.
Let’s dive into this blog to learn what Azure security is and how your organization can incorporate Microsoft Azure Active Directory in the best way.
What is Azure Security?
Azure is one of the best and most robust cloud computing service providers in the competitive market. It incorporates various services, such as databases, storage, and a network.
Due to the endless services that make your network strong and secure, Azure is the top choice for organizations to safely and securely store their confidential information. Whenever some third party tries accessing the data or tries to control the system, Azure alerts the organizations.
But even with such a powerful security framework, attackers can sometimes attack. So, ensuring double security for confidential data is necessary and great.
That’s where an important tool of Azure, the Azure Security Center, comes in.
Azure security is the security management tool for Azure customers’ cloud stuff. Here’s how it helps in various ways:
- Provides visibility and security control for Azure resources such as cloud services, virtual machines, virtual networks, and blob storage.
- Prevents the deployment of mixed workloads in Azure or non-Azure settings, including client locations.
- Enhances security posture by monitoring the cloud environment and assisting clients to determine the health and security of their resources.
- It detects and blocks cyber attacks and displays alerts and recommendations on its dashboard. This dashboard also helps with compliance management, as security policies are easily accessible via the Azure Security Centre dashboard.
Azure Security Center also helps with some other big problems:
- Changing Workloads: For services whose usage varies as consumers do more in the cloud, Azure Security Centre simplifies conforming to security requirements and best practices. It helps keep things safe even when they’re always changing.
- Attacks are becoming Simpler: As more and more consumers use the public cloud, threats get more complex. Customers must continue to defend their businesses, but doing so may expose them to further risk if they do not follow best practices. Azure Security Centre can help with this operation.
- Lack of Security Expertise: The quantity of security alerts and notifications might be overwhelming for administrators, particularly those who are inexperienced. Administrators can, however, use Azure Security Centre to deal with direct attacks. It helps newbies stay on top of things.
So, if you want to keep your data safe in the cloud, Azure Security Center is your best friend. With Azure Security Center, you can rest easy knowing your data is in good hands.
Why is Azure Security Necessary?
Every organization requires different and customized security frameworks for its data. Given the highly advanced threat vectors within the cloud architecture, organizations must implement a zero-trust security approach, in which no aspect of the business is trusted, and everything is verified.
This means safeguarding confidential data and resources and implementing measures across all application layers – from computing, storage, and networking to application-specific controls and identity/access management.
Azure Security provides it all – ensuring the security of each specific workload. Azure security allows organizations to customize their security controls by offering various configurable tools and services to address multiple security demands.
It offers various features that make it necessary for businesses:
- Encryption allows organizations to prevent unauthorized access to sensitive information, even if storage devices are compromised or intercepted during transmission.
- Microsoft 365 Secure Score & Defender for Cloud allows Azure administrators to examine and adjust security settings across their environments. It also provides the present security status and recommends strong steps that help organizations continuously improve their security posture and avoid possible threats.
- Identity-based control mechanisms, such as multi-factor authentication and AI-powered anomaly detection, help organizations implement strict access controls and detect suspicious activity in real-time. This feature allows only authorized individuals to access the data.
Not only these, Azure also allows organizations to leverage industry-leading antivirus technologies from reputable vendors like Kaspersky Labs, McAfee, and Symantec. These antivirus solutions help organizations detect and mitigate malware threats, ensuring the integrity and security of their Azure environment.
What is Azure Active Directory?
Azure Active Directory (Azure AD) is now Microsoft Entra ID. It is Microsoft’s cloud-based identity and access management platform. It is the foundation of the Office 365 system, which syncs with the on-premise Active Directory and even authenticates other cloud-based services via OAuth.
Additionally, its services, such as core directory, access control, and identity protection, allow administrators to control end-user identities and access privileges.
The service also allows administrators to specify which information will remain in the cloud, who may use or manage it, which services or apps can access it, and which end users have access.
Not only this, Azure AD helps enable SSO (single sign-on), which eliminates the need for end users to enter passwords multiple times while accessing the cloud apps.
Besides administrators, IT administrators, app developers, and Microsoft cloud service customers can also use Azure AD.
- IT administrators can use it to manage role permissions and regulate individual users’ access to specific applications and resources.
- App developers can use it to add single sign-on to apps with pre-existing user credentials.
Azure AD (Microsoft Entra ID) also provides application program interfaces (APIs) that use the organization’s existing data. By default, subscribers to Microsoft cloud services such as Office 365, Dynamics CRM Online, and Azure are Azure AD tenants.
7 Azure AD or Microsoft Entra ID Security Best Practices
Here are the 7 Azure AD Security Best Practices –
Enable Azure AD Multi-Factor Authentication (MFA)
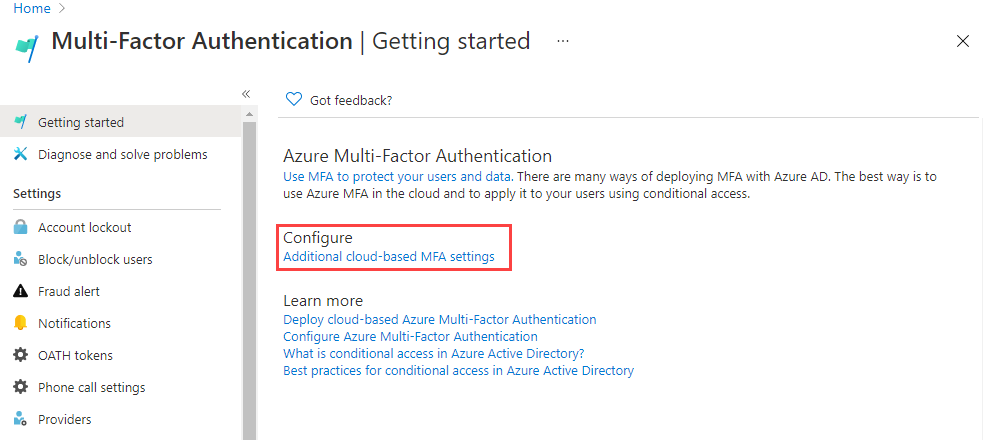
Azure AD’s Multi-factor authentication reduces the danger of password-only authentication by forcing users to give a combination of two or more factors:
- “something they know” (e.g., a password),
- “something they have” (e.g., a trusted device such as a phone), and
- “something they are” (e.g., their fingerprint).
In general, it is suggested that MFA be enabled not only for administrators but for all users, particularly those that could pose a severe threat if compromised.
Microsoft provides many techniques for enabling Multi-Factor Authentication:
- Azure AD Security Settings — This option allows organizations to streamline MFA deployment and rules for challenging administrator accounts, requiring MFA via Microsoft Authenticator for all users, and restricting legacy authentication protocols. This approach is available for all licensing levels.
- Conditional Access policies — allows you to enforce multi-factor authentication under certain conditions, such as signing in from unusual locations, untrusted devices, or dangerous applications. This technique reduces the load on users by requiring additional verification only when a higher risk is discovered.
- Modifying user state on a per-user basis — This option is compatible with both Azure AD MFA in the cloud and the Azure MFA authentication server. It requires two-step authentication for each sign-in and overrides Conditional Access restrictions.
Protect Secrets and Keys using Key Vault.
Microsoft Azure offers Key Vault, a cloud service that secures the storage of secrets and keys. This service employs encryption and other security measures to keep secrets and keys safe from unauthorized access, even if the underlying data storage is compromised.
Recommended: Comprehensive Guide on Azure Key Vault
Key Vault is intended to assist businesses in protecting sensitive information such as passwords, API keys, and other secrets by providing capabilities such as auditing, versioning, and the ability to revoke and rotate keys. It works seamlessly with other Azure services, making utilizing and managing secrets and keys in your Azure environment simple.
Configure Password Management
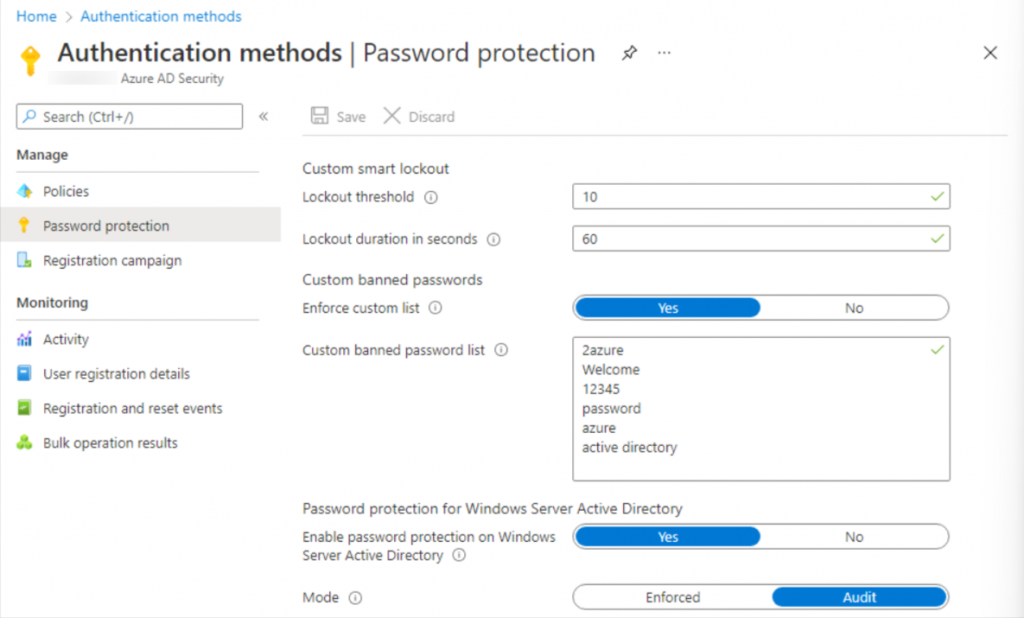
Microsoft has revised its password policy guidance to no longer expire passwords. However, SMEs that are regulated or don’t have MFA and CA configured should not do this. You may also consider changing your password if you suspect an ID has been hijacked.
As per a study, CrowdStrike discovered that 71% of assaults are now malware-free, and compromised identities cause target cloud IDs and 75% of cloud breaches.
The Zero Trust posture is not voluntary. Consider implementing Extended Detection and Response (XDR) from a vendor of your choice or paying an additional fee for Microsoft Identity Protection if you prefer the Microsoft stack.
You can also Configure Password Management following these:
- Set up self-service password reset (SSPR) using two authentication methods. It should be noted that using security questions may be problematic, as attackers can get “open source” intelligence on employees from the web or obtain information from third-party breaches elsewhere. Microsoft charges more for on-premises write-back.
- Use the same password policies across all environments (on-premises and cloud). Microsoft provides substantial guidance on an agent-based strategy for enforcing AAD password protection on AD DS without exposing your domain controller to the internet or requiring network changes. It is important to note that you must be proficient in adjusting AD settings.
Use Microsoft Defender to Prevent, Detect, and Respond to Threats
Microsoft Defender for Cloud is a cloud-based security platform with various tools and services for detecting, preventing, and responding to threats.
Some advantages of utilizing Microsoft Defender for Cloud include:
- It utilizes machine learning and other technologies to detect and prevent cyber threats like malware, ransomware, and phishing.
- It identifies and prioritizes vulnerabilities in your Azure environment, recommending fixing them.
- It monitors your Azure environment for compliance with regulations and standards, including GDPR and HIPAA.
- It proactively responds to security threats and vulnerabilities, minimizing their impact on your Azure environment.
Recommended: What Is the Windows Defender Security Warning? How to Get Ride?
Role-Based Access Control
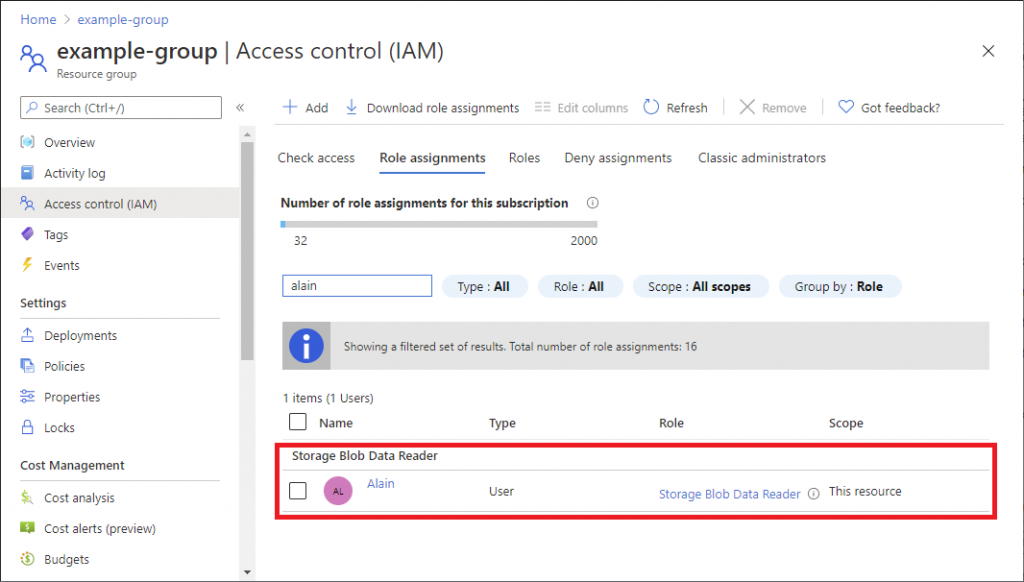
AAD supports built-in and tailored user roles, and role-based access control (RBAC) is standard across all subscription tiers. This allows IT to use the principle of least privilege and contributes to a zero-trust security approach, but it relies significantly on manual input and maintenance. Dynamic membership rules are now possible with a rules-based approach independent of RBAC.
Make sure that you:
- Minimize the number of privileged accounts for that
- Prepare to manage, control, and monitor access.
- Limit global administrator accounts and instead use other roles like billing administrator, global reader, helpdesk administrator, and license administrator.
- Limit global administrators and never sync high-privilege accounts from Active Directory.
- Pay close attention to external collaboration settings and consider preventing external users from inviting visitors to shared files or third-party storage. Also, review & and adjust settings for SharePoint Online and OneDrive. These changes affect end users but make identifying “official” channels easier.
Using security groups for users improves application security and reduces administrative costs. Microsoft restricts this functionality to AAD Premium 1 (P1) and Premium 2 (P2) accounts.
However, always aim to avoid allocating resources directly to users and utilize identity protection. Please keep in mind that Microsoft has listed some limitations when it comes to syncing AD groups with ADD groups. For example, AD primary group memberships will not be carried over to AAD.
Limit Administrative Privileges
Admin accounts are the most common target for attackers because they enable access to critical data and systems throughout an organization’s ecosystem. These accounts are required for both business and IT tasks, but they pose a considerable risk to your organization.
Accordingly, experts emphasize the importance of not just securing these accounts but also limiting their quantity. To achieve that goal, you must have a thorough awareness of all of your organization’s administrative accounts, both obvious and not.
As a result, in addition to enumerating the membership of known groups or roles that provide administrative access, audit individual access rights to identify shadow admins who may be lurking around and take steps to reduce the opportunities for privilege escalation via non-standard means.
Plan for Routine Security Improvements
As cyber security threats are continuously growing, organizations must constantly improve their security measures. It is essential to design the cloud and identity management framework in a way that it regularly grows and secures the environment in new ways.
This is where you can use the identity secure score, which is a set of recommended security policies published by Microsoft that operate together to provide a numerical score which can further be used to objectively assess the security posture and plan future security enhancements.
Bonus Tip – Be Prepared for the Worst!
Create an emergency access Global Admin account in case you need to “break the glass” during network failures or system downtime. This account has been excluded from CA and MFA. Always store these credentials securely and use a complex password.

