What is Azure IoT Security? Top Best Practices to Secure IoT Devices

IoT devices have become a vital component of worldwide business operations for different industries, including healthcare, IT, transportation, etc. Organizations that invest in IoT deliver more value to their consumers than others.
According to a report by Statista, the number of IoT devices is estimated to be 17.08 billion in 2024, and the figure is showing no signs of stopping.
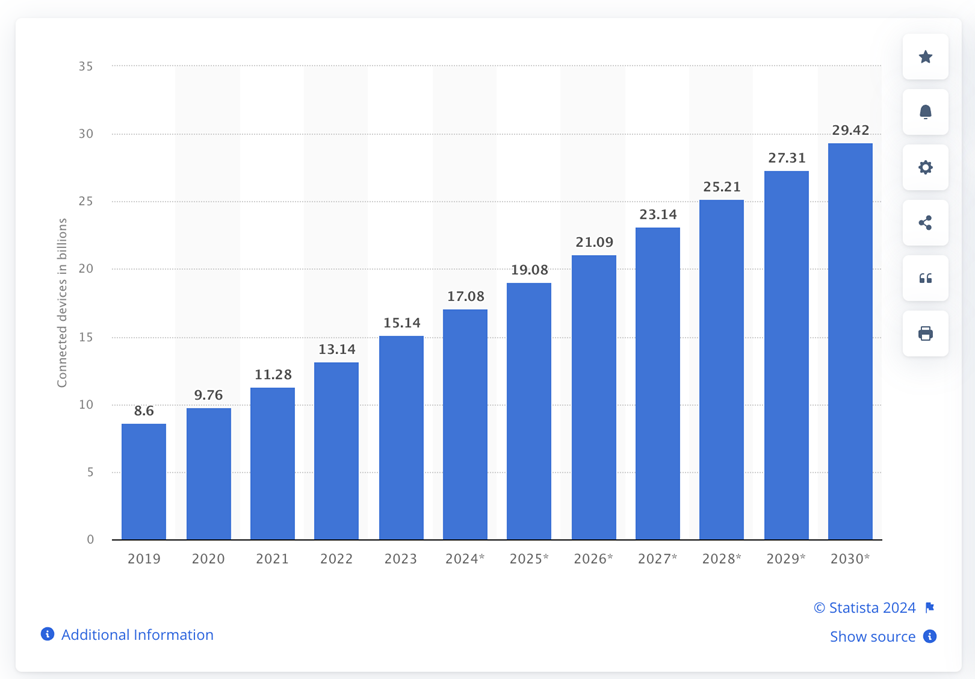
But as its usage is continuously increasing, so are the security concerns!
Wondering Why?
The global network of smart devices evolves and becomes increasingly complex, resulting in enhanced interconnectedness. IoT devices are possible entry points to hack a company’s network system.
To combat such situations, we have some best practices that can be used for securing IoT devices.
What is IoT (Internet of Things)?
IoT, or the Internet of Things, refers to the network of connected devices, objects, or “things” that collect and share data through the internet.
However, IoT is not only about connected devices but also about the information these devices collect and gives immediate insights into several aspects.
These insights can further be used for
- Streamlining Business Operations
- Predictive Maintenance
- Remote Monitoring
- Manufacturing Efficiency
- Expansion into New Lines of Business
- Wasted Materials Reduction, etc.
As a whole, IoT helps turn data into insights, and, finally, businesses can use those insights to turn them into action.
What is Azure?
Azure, or Microsoft Azure, is a cloud computing platform with more than 200 products and cloud services, including:
- Infrastructure as a Service (IaaS),
- Platform as a Service (PaaS), and
- Software as a Service (SaaS).
These can be used for building, deploying, or managing applications and services. Over 95% of Fortune 500 businesses rely on and trust Azure. For what? Let’s have a look!
Backup & Disaster Recovery:
Azure can backup data from any location in almost any language or on any OS (Operating System). The best part? Backup frequency can be defined (daily, weekly, monthly, etc.) according to different requirements. Due to its flexibility, advanced site recovery, and built-in integration, Azure is one of the best backup and disaster recovery tools.
Web & Mobile App Hosting and Development:
It provides a platform for hosting, developing, and managing web and mobile applications. With Azure, businesses can ensure their applications are autonomous, adaptive, and scalable.
Active Directory Integration:
Azure integrates seamlessly with Active Directory to provide centralized management, global reach, and enhanced identity and access management security. Multi-factor authentication and single sign-on capabilities further enhance security and user experience.
IoT Industry Solutions:
Azure’s scalability, flexibility, and security make it an ideal platform for IoT solutions. Azure IoT Hub can help organizations in several ways, like
- Monitoring and managing billions of devices
- Get insights to make better decisions
- Enhanced security features
- Remote monitoring
- Predictive maintenance and analytics.
What Is IoT Security?
IoT security is an umbrella term used for the tools and strategies that help safeguard devices connected to the cloud. Simply put, it is a method to protect IoT devices connected to a network from cyber threats and unauthorized access.
What is Azure IoT Security?
Azure IoT is a collection of Microsoft-managed cloud services, edge components, and SDKs that help connect, monitor, and control IoT devices.
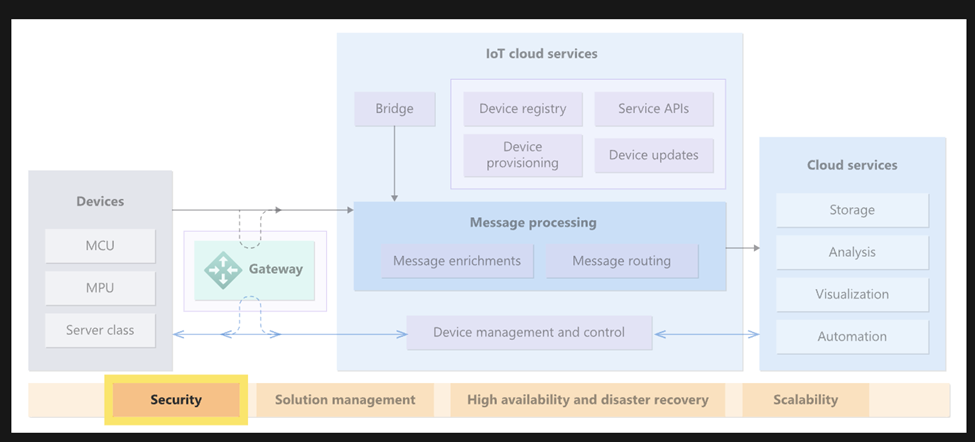
As shown in the above figure, IoT security is divided into three parts.
- Device Security: Protecting IoT devices from unauthorized access and tampering.
- Connection Security: Focuses on securing the communication between IoT devices and the cloud services they interact with.
- Cloud Security: Safeguard data while it’s stored and processed in the cloud.
Recommended: Azure Security Best Practices & Cloud Security Checklist for Secure Cloud Storage
IoT Security Challenges
Before we move forward to know more about Azure IoT device security best practices, it’s first important to understand the security challenges.
Device Diversity:
Due to the various shapes, sizes, and functionalities of IoT devices, it becomes a challenge to implement standardized security measures across all devices. As a result, this diversity increases the complexity of managing security vulnerabilities.
Data Privacy Concerns:
With that being said above, IoT devices collect and transmit huge amounts of data, often including sensitive information. Now, as data flows between devices, networks, and cloud platforms, protecting this from unauthorized access is a significant challenge.
Firmware and Software Vulnerabilities:
Many IoT devices often rely on firmware and software for their operation. These may contain vulnerabilities or bugs that attackers could exploit.
Remote Access:
Certain IoT devices allow remote control or monitoring, which is convenient but also opens them up to security risks. Ensuring secure remote access is vital to prevent unauthorized tampering.
Device Proliferation:
As the number of IoT (Internet of Things) devices continuously increases, it becomes tough to manage and secure each one individually from potential threats.
Azure IoT Device Security Best Practices
Following the best practices for Azure IoT security is vital to keep users, devices, and data always secure. Some of the best practices or methods for securing IoT devices include:
Use Microsoft Defender for IoT:
Microsoft Defender for IoT acts as a proactive monitoring solution for Azure resources. It serves as an initial defense line that detects and addresses vulnerabilities before they escalate.
Keep System Updated:
It is a very important practice to update device operating systems and drivers to the latest versions regularly. So as to ensure protection against known vulnerabilities and security threats.
Secure Hardware Deployment:
Ensure hardware is tamper-proof in deployments to unsecured locations, such as public spaces.
IoT Gateway Security:
The next measure by which the security of IoT devices can be enhanced is through IoT gateway security measures. Secure Web Gateway (SWG) offers essential features such as application control, deep HTTPS and SSL inspection, remote browser isolation, and URL filtering. These measures block unauthorized software, like malware, from accessing user connections.
Secure Hardware Selection:
To protect the overall IoT infrastructure, prioritize device hardware with security features like secure and encrypted storage and boot functionality based on the Trusted Platform Module (TPM).
Use Device SDKs:
Opt for Device SDKs that implement encryption and authentication features. Why? This facilitates the development of robust and secure device applications.
Frequent & Regular Auditing:
Regularly audit IoT infrastructure for security-related issues, reviewing event logs to detect and respond to security breaches promptly.
Follow Manufacturer Guidelines:
Adhere to device manufacturer security and deployment best practices and generic security guidelines.
Recommended: Ensure IoT Identity Security at Scale with the Excellence of PKI
To Secure Connections, follow the Below Practices
X.509 Certificate Authentication:
Use X.509 certificates for authenticating devices to IoT Hub or IoT Central. It is recommended for production environments and offers enhanced security compared to security tokens.
TLS Root Certificate Updates:
Establish a mechanism for updating TLS root certificates on devices. However, TLS root certificates are long-lived, but they may expire or be revoked. If these certificates are not updated, devices may lose connectivity to cloud services in the future.
Transport Layer Security (TLS) 1.2:
Ensure that device connections are secured using the TLS 1.2 protocol. IoT Hub and IoT Central rely on TLS to encrypt connections, protecting against unauthorized access and data interception.
Azure Private Link:
Consider implementing Azure Private Link to connect devices to a private endpoint on your Virtual Network (VNet). This allows you to block access to public-facing endpoints of IoT hubs, enhancing security by limiting exposure to external threats.
What is the Difference between Azure IoT Hub and Azure IoT Central?
Azure IoT Hub and Azure IoT Central are both platforms provided by Microsoft for building and managing IoT solutions, but they serve different purposes and have distinct characteristics.
Let’s have a look!
Microsoft Azure IoT Central
- Azure IoT Central is a SaaS (Software as a Service) used for centralized device data management.
- Abstracts underlying Azure IoT Hub infrastructure for simplified user experience.
- It has a web dashboard that can be used for monitoring and visualizing device data, creating custom alerts, and setting up data-driven workflows.
- Azure IoT Central’s drag-and-drop widgets & SDKs allow the development of custom device applications.
- Pricing: Azure IoT Central is based on the pay-per-device payment model. As it is a SaaS-based solution, so there are fixed payment plans and no option to optimize the costs.
Microsoft Azure IoT Hub
- Azure IoT Hub is a PaaS (Platform as a Service) that serves as a communication hub for IoT devices.
- It enables data sharing among devices, generating insights and enhancing data utilization.
- Allows creation of custom device SDKs or use of pre-built SDKs in multiple languages.
- Pricing: Payment is based on the total number of messages per day, known as a unit, and any number of devices can utilize each one. Additional units or plan upgrades are required for increased data exchange needs.
Wrapping Up!
To ensure your IoT devices’ security, get the best Code Signing Certificates from SignMyCode for different platforms, such as Azure Key Vault, Java, Apple, etc. We offer Money Back and the Lowest Price Guarantee!
Azure IoT security is all about keeping your IoT devices and data safe in the cloud. By using Azure’s security features, you can protect your devices from hackers and other threats.
