Ensure IoT Identity Security at Scale with the Excellence of PKI

The modern digital space is undergoing a seismic transformation characterized by an unprecedented surge in IoT device adoption across industries. As businesses embrace digitization on an ever-expanding scale, deploying IoT devices has transcended mere convenience, becoming an integral part of the operational fabric.
With a proliferation that has outpaced human population growth, the world is witnessing a new era laden with both possibilities and challenges.
Integrating network-connected devices is reshaping industries and redefining how we interact with technology, from healthcare to manufacturing, from pharma to vehicular systems. The potential of IoT applications spans vast by promising innovation, efficiency, and interconnected experiences like never before.
Power of IoT Devices
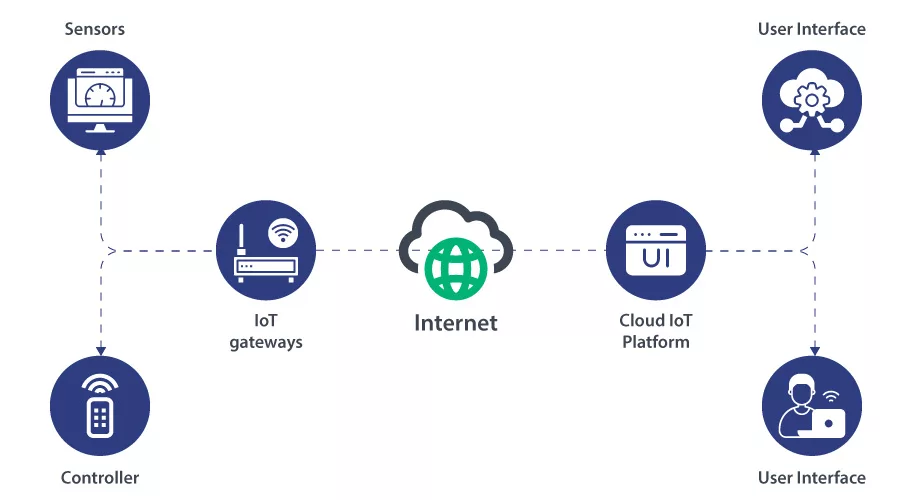
The allure of IoT devices lies in their ability to infuse enhanced functionalities, mobility, and seamlessness into our digital lives. However, amidst the marvels they bestow lies a lurking concern – the security of identity. The essence of trust, the cornerstone of the digital age, is at stake due to potential vulnerabilities in the IoT ecosystem.
In this dynamic environment, safeguarding the identity and security of IoT devices is paramount. The answer to this challenge emerges in the form of Public Key Infrastructure (PKI), a cryptographic framework that holds the potential to fortify the foundations of IoT security.
A resilient strategy for ensuring network-connected devices’ integrity, authentication, and data encryption can be established by seamlessly integrating PKI into the manufacturing process. In the following pages, we will delve into the critical role of PKI in IoT security, exploring its capacity to mitigate cyber threats and uphold the trust that underpins our connected future.
Harnessing PKI for IoT Identity Security: Building a Resilient Framework
Integrating Public Key Infrastructure (PKI) technology has many benefits when establishing an identity-centric security paradigm for IoT devices.
Its prowess lies in enabling authorized user access to applications, systems, and smart devices, forging a foundation of trust and security in the IoT ecosystem. Yet, to unlock the full potential of PKI, a thoughtful strategy anchored in its deployment is essential.
The Robustness of PKI Technology:
PKI technology is celebrated for its potent security standards, achieved through the formidable combination of asymmetric encryption and hashing mechanisms.
In the intricate dance of IoT manufacturing and deployment, a well-managed PKI system is a bulwark against vulnerabilities inherent in tokens and passwords.
Furthermore, the allure of PKI technology extends to its compatibility with the resource constraints of IoT devices. Its deployment offers the gift of asymmetric encryption and a minimal computational and memory footprint, making it an ideal match for devices with limited processing power.
Navigating the Landscape of Certificate Policy and Certificate Practice Statement:
Within PKI and procedural intricacies, the importance of Certificate Policy (CP) and Certificate Practice Statement (CPS) must be balanced. In orchestrating a PKI ecosystem, the issuance of certificates, symbolic of cryptographically verified identities, rests solely with a Certifying Authority (CA).
These certificates weave a tapestry of trust, embodying the essence of device identity. Their life cycle management (CLM) forms a critical process that can update or revoke certificates on an individual device level.
Steering the Ship with Certificate Policy Implementation:
Certificate Policy presides over crucial generation, storage, backup, recovery, and distribution. The orchestration of these operations is meticulously documented, ensuring alignment with the ever-evolving regulatory landscape.
By emanating from a single, Trusted Certificate Authority (CA), unique certificates simplify device authentication, bestowing certificates with high availability and near-instantaneous latency for large-scale IoT deployments.
A Bespoke Approach of Tailoring PKI to IoT:
While the core principles of IoT remain steadfast, the application of PKI demands a unique adaptation within the IoT device lifecycle. The complexities of IoT ecosystems necessitate PKI to scale and seamlessly integrate with key generation, storage, certificate policy, and lifecycle management.
Unlike conventional enterprise PKI implementations, the PKI-IoT nexus requires a custom approach that embraces scalability, availability, and security without compromise.
How to Get Public Key Infrastructure (PKI) for IoT Device Protection?
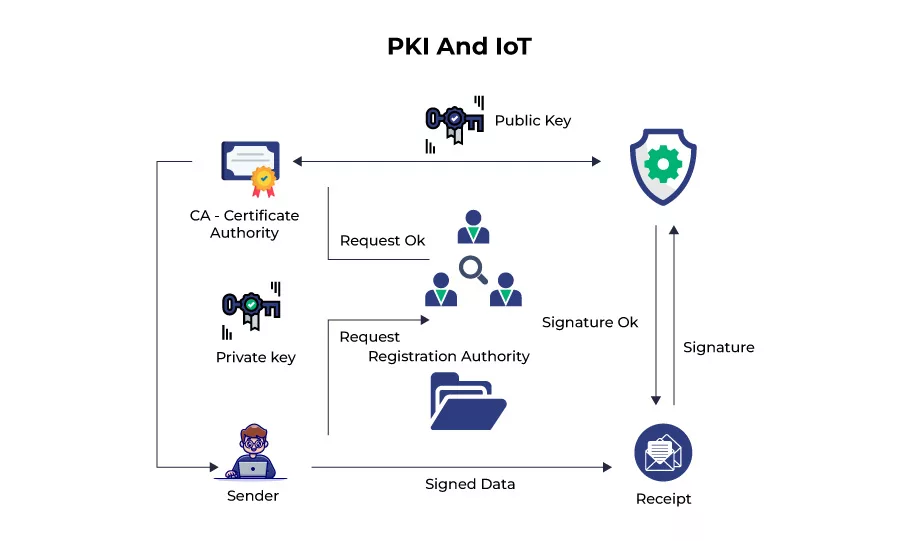
Where the proliferation of IoT devices brings both innovation and challenges, Public Key Infrastructure (PKI) emerges as a formidable guardian of security. Securing IoT devices is no longer a mere aspiration; it’s a necessity. Here’s how PKI can be wielded to shield IoT devices from potential threats:
Establishing and Upholding Security Standards:
PKI operates on an open standard, empowering organizations to craft a cryptographically secure system. By defining a framework that includes trusted root CAs, revocation policies, and standardized protocols like SCEP and ACME for certificate management, the IoT ecosystem is fortified against unauthorized access and malicious interventions.
This proactive stance elevates the security posture of IoT devices to a new level of resilience.
Distinct Identity for Every IoT Device:
The foundation of IoT security lies in assigning a unique digital identity to each device. This cryptographic fingerprint, embodied in digital certificates, not only facilitates secure network access and code execution but also offers the flexibility to adapt based on manufacturer policies.
With this, a cryptographically verifiable identity becomes the gatekeeper of each device’s interactions, ensuring trust and authenticity throughout its lifecycle.
Elevating Security Standards:
Digital certificates from a well-orchestrated PKI system wield a level of security surpassing conventional authentication methods. Additionally, integrating secure hardware components for cryptographic key storage further elevates security.
The extended validity periods of these certificates far exceed the practical lifetime of passwords or tokens, offering sustained protection against evolving threats.
Scalable Security for Expansive Deployments:
The genius of asymmetric encryption lies in its ability to issue certificates from a singular, trusted Certificate Authority (CA). This decentralized approach eliminates the need for a centralized server or resource-intensive agent-based software for device authentication.
This inherent scalability ensures that security remains robust without straining resources, whether deploying a handful of devices or orchestrating an expansive network.
Ensuring Security with a Light Touch:
A remarkable facet of PKI is its ability to secure devices with minimal resources. Even devices grappling with memory and processing power limitations can harness the power of asymmetric keys.
For instance, Elliptic Curve Cryptography (ECC) is the panacea for sensor and network devices that rely on smaller-sized keys. PKI ensures protection without undue burden by enabling security measures that complement the device’s innate capabilities.
Addressing IoT Security Problems with Scalable Solutions using PKI
In an era where security breaches can shatter user trust instantly, the quest for an interoperable and scalable security solution has become a driving imperative.
This has culminated in adopting authentication protocols empowered by Public Key Infrastructure (PKI) aimed at fortifying the security foundations of the IoT ecosystem.
To comprehend the urgency of this move, let’s delve into the prevalent security threats that cast a shadow over IoT devices and how PKI can be the remedy.
Poor Verification:
Among the most insidious threats to IoT security is weak authentication. Many commercial IoT devices come out of the box with default credentials, often set by manufacturers.
This seemingly convenient approach, however, creates a glaring vulnerability. Hackers capitalize on these weak credentials to gain unauthorized access, potentially leading to the deployment of malicious software.
The result? A compromised device, a breach of privacy, and the erosion of trust. PKI-driven authentication protocols can overhaul this scenario by establishing robust and dynamic authentication mechanisms that resist hackers’ attempts to exploit default settings.
Inaccurate Secure Keys:
The storage and security of encryption keys lie at the core of IoT device protection. Yet, at scale, ensuring the confidentiality of these keys becomes a complex challenge. Mismanagement or inadequate safeguards can expose these keys to cyber criminals.
Recommended: Top Best Practices for Storing X.509 Private Keys
Asymmetric keys stored improperly or using insecure symmetric encryption keys can unlock a treasure trove of sensitive data for malicious actors.
PKI’s sophisticated key management protocols can introduce an extra layer of protection, ensuring keys are generated, stored, and exchanged securely, bolstering the defenses against unauthorized access.
Weak Encryption:
In the race to make IoT devices user-friendly, compromises on encryption strength can be tempting. Weaker encryption algorithms seem more convenient but become open invitations for cyberattacks.
A subpar encryption algorithm can be swiftly deciphered by determined hackers, jeopardizing the confidentiality and integrity of transmitted data. With its arsenal of robust encryption algorithms and rigorous standards, PKI enforces a higher level of protection, making data breaches an uphill battle for cyber adversaries.
Difficult Credentials:
Embedding hardcoded credentials in source code, while intended to simplify development and management, comes with an alarming trade-off: it becomes a two-way street for developers and hackers. A quick backdoor for developers can also serve as an open gateway for hackers.
PKI injects a dose of intelligence into this equation, enabling dynamic credential management through digital certificates. This dynamic approach reduces the attack surface and bolsters the overall security posture.
PKI addresses authentication vulnerabilities, secures encryption keys, strengthens encryption, and enables dynamic credential management, which aligns perfectly with the multifaceted challenges presented by IoT security.
Challenges in IoT Security:
IoT devices operate in diverse and often hostile environments, making them susceptible to a range of security challenges:
Device Heterogeneity:
IoT encompasses various devices with differing architectures, capabilities, and constraints, complicating the implementation of standardized security measures.
Limited Resources:
Many IoT devices operate with limited processing power, memory, and energy resources, making resource-intensive security mechanisms challenging to implement.
Remote Management:
IoT devices are often remotely managed, making it essential to ensure secure and authenticated software updates to prevent unauthorized access or data breaches.
Supply Chain Vulnerabilities:
The complex and global supply chain for IoT components introduces the risk of compromised hardware or software components being integrated into devices.
Data Privacy:
IoT devices collect and transmit sensitive data, necessitating robust encryption and authentication to protect user privacy.
Why Choose SignMyCode for Code Signing: The Best Practice Solution for IoT Security
The proliferation of interconnected devices has opened up unprecedented avenues for innovation and convenience but has also introduced significant security challenges.
As IoT devices become integral to critical infrastructure, healthcare systems, manufacturing processes, and more, ensuring the integrity and authenticity of the code running on these devices has become non-negotiable.
This is where Code Signing comes into play as a crucial cybersecurity measure, and SignMyCode emerges as a best practice solution for implementing this technology effectively.
Understanding Code Signing in IoT:
Code signing is a cryptographic process that involves applying a digital signature to software code before it is distributed or deployed. This signature acts as a tamper-evident seal that verifies the origin of the code and ensures that it has not been altered or compromised during transit.
Recommended: What is a Code Signing within the Public Key Infrastructure (PKI)?
In the IoT context, code signing safeguards against various security threats, such as malware injection, unauthorized modifications, and firmware tampering.
By guaranteeing the authenticity and integrity of the code, code signing provides end-users, manufacturers, and service providers with the confidence that the IoT devices they interact with are secure and trustworthy.
You can follow the below-listed aspects for the most precise selection.
| Buy Certificates | Price |
| OV Code Signing Certificate | $199.99/yr |
| EV Code Signing Certificate | $269.99/yr |
| Individual Code Signing | $199.99/yr |
Wrapping up
The role of PKI in IoT security, specifically through code signing, must be considered. SignMyCode emerges as a leading solution addressing IoT security’s unique challenges.
By providing robust authentication, secure onboarding, resource efficiency, and support for remote updates, SignMyCode helps fortify IoT devices against various threats.

