What is a Code Signing within the Public Key Infrastructure (PKI)?

Public Key Infrastructure (PKI) is a fundamental backbone, empowering the seamless use of cutting-edge technologies like digital signatures and encryption across vast user populations.
It encompasses a comprehensive suite of hardware, software, policies, processes, and procedures, working harmoniously to create, manage, distribute, use, store, and revoke digital certificates and public keys.
The significance of PKI goes far beyond mere technicalities – it forms the bedrock for a secure and trusted business in e-commerce and the rapidly expanding Internet of Things (IoT).
By establishing and verifying the identities of individuals, devices, and services, PKIs pave the way for controlled access to critical systems and resources. Through this, data is safeguarded, and transactions carry an enhanced sense of accountability.
Importance of PKI Technology
As the world moves towards next-generation business applications, PKI technology assumes an increasingly vital role, providing the assurance required for the success of evolving business models.
With electronic interactions becoming ubiquitous and stringent data security regulations taking center stage, PKI is a guardian, ensuring online authentication and compliance in a dynamic and ever-evolving digital ecosystem.
Amidst this intricate tapestry of PKI, one particular facet shines brightly – Code Signing.
In this article, we delve into the world of code signing within PKI, unraveling its significance, mechanisms, and profound impact on bolstering the security and trustworthiness of software applications.
Let’s embark on this enlightening journey to discover the essence of “What is code signing in PKI?”
The Importance of PKI in Code Signing
Code signing plays a vital role in ensuring the integrity and security of software in both development and production environments. The Public Key Infrastructure (PKI) concept, a robust security framework, is at the heart of code signing. PKI facilitates the safe exchange of information by utilizing encryption, authentication, and integrity principles.
Cryptographic keys are central to the PKI framework, which works collaboratively to safeguard data during code signing. When code is signed, it uses a public key, making it unreadable. Only the corresponding private key possessed by the developer can decrypt and verify the code’s authenticity.
A critical element of PKI in code signing is the involvement of a trusted third-party identity verifier known as a Certificate Authority (CA). The CA is pivotal in issuing the code signing certificates that bind the public key to a specific entity or developer.
These certificates are crucial for establishing trust and legitimacy in digital signing.
PKI’s track record speaks for itself, as it has been the go-to security solution for decades. Its versatility has been successfully applied to secure various digital aspects, including networks, websites, email communication, and user authentication.
How are Certificate Authorities (CAs) in Public Key Infrastructures Vital?
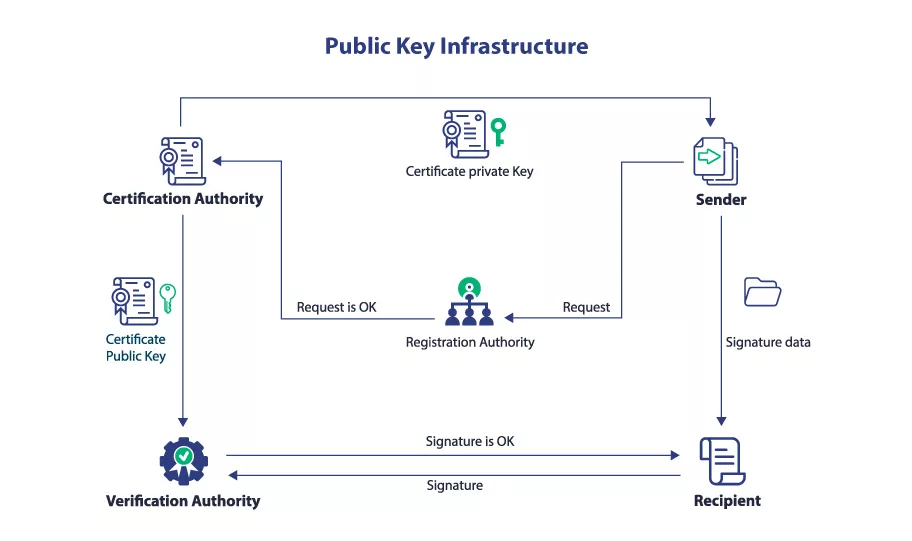
Within the intricate Public Key Infrastructures (PKIs) framework, digital certificates bind public keys to their corresponding users, ensuring secure and authenticated transactions.
These digital certificates serve as the credentials that verify identities, much like a passport certifies one’s citizenship in a country. In the digital realm, these certificates establish the identity of users, ensuring trust within the ecosystem.
The significance of digital certificates lies in their ability to identify the intended recipients of encrypted data and verify the identity of the signers of information. Therefore, safeguarding the authenticity and integrity of these certificates becomes paramount to maintaining the overall trustworthiness of the system.
Recommended: What is a Digital Certificate? Why Are They Important?
We turn to Certificate Authorities (CAs) to issue these digital credentials. These entities are responsible for certifying users’ identities within the PKI. CAs form the bedrock of security for the PKI and the services it supports.
To mitigate the risk of such attacks, it has become essential to implement a range of physical and logical controls and employ hardening mechanisms like hardware security modules (HSMs).
Recommended: What is a Hardware Security Module? Role of HSMs for Digital Signing
These measures bolster the integrity of the PKI, ensuring that the entire system remains robust and resilient against potential threats.
Understanding the Importance of Scalability in a PKI
Scalability is crucial to any well-designed Public Key Infrastructure (PKI), ensuring it can seamlessly accommodate an organization’s growth and user base.
Failure to factor in scalability can lead to the need for a complete PKI redesign as the business expands, resulting in lost productivity and potential negative impacts on customers. PKI scalability must be carefully considered from the outset to avoid such disruptions.
In the rapidly evolving digital landscape, where new applications emerge daily, and users demand access from multiple devices, PKI scalability becomes a pressing concern.
Comprehensive business planning necessitates anticipating and accommodating the increasing demands on the PKI infrastructure as the organization grows.
PKI scalability involves the number of Certificate Authorities (CAs) required to meet the organization’s expanding needs. Certificates are used for critical purposes, including logon authentication, digital document signing, and secure email communication.
As these use cases grow, more than one root CA might be needed, prompting multiple subordinate CAs to address different requirements. Another approach entails setting up multiple root CAs with hierarchies tailored to specific needs.
Regardless of the chosen strategy, the primary objective remains: to establish a scalable PKI that can accommodate the organization’s present and future growth without needing significant overhauls.
By getting the PKI design right from the beginning, the organization can ensure its security infrastructure remains agile and adaptive, aligning seamlessly with its ever-expanding needs.
The Pervasive Influence of Deployment in PKI
The widespread adoption of PKIs has revolutionized the deployment of cryptographic data security technologies on a massive scale. PKIs are the robust foundation that facilitates the effective utilization of essential cryptographic elements like digital certificates and signatures.
Its support for identity management services within and across networks lies at the core of PKI’s functionality. It enables seamless online authentication, a key component of secure socket layer (SSL) and transport layer security (TLS), ensuring the protection of internet traffic.
Moreover, PKIs extend their capabilities to encompass various applications, including document and transaction signing, application code signing, and time-stamping, further fortifying data security.
PKI has emerged as a pivotal player in many solutions across multiple domains. From desktop login to citizen identification and mass transit to mobile banking, PKIs are critical enablers of these services.
As the Internet of Things (IoT) continues to burgeon, PKIs become prominent in device credentialing, imparting identities to an array of cloud-based and internet-connected devices.
About Trust and Non-Repudiation in a Robust PKI
A well-established Public Key Infrastructure (PKI) forms the backbone of a secure digital environment. One critical aspect of PKI is establishing trust and non-repudiation, ensuring integrity and legal verifiability of digital transactions.
Inadequate security within a PKI, particularly concerning key management, can expose organizations to significant risks. If the PKI lacks the necessary measures to safeguard cryptographic keys, it becomes vulnerable to unauthorized access or tampering, leading to potential loss or disruptions.
Recommended: What is X.509 Certificate? How it Works and How to to Obtain it?
A critical consequence of such a scenario is the inability to verify a message’s sender’s authenticity legally.
However, a PKI built on a solid foundation of security and integrity can provide organizations with essential legal protection. Digital signatures, a hallmark of a robust PKI, offer irrefutable evidence of the message’s origin and the precise time it was sent.
This cryptographic evidence becomes a powerful tool in legal disputes, allowing organizations to prove the legitimacy of user activity.
The strength of the PKI directly impacts the defensibility of the digital signatures it generates. Suppose the PKI is robust and secure, demonstrating that signing keys are adequately protected back to the root key.
In that case, the organization gains a substantial advantage in legal challenges concerning a specific user’s authenticity and actions.
The Foundation of Cryptographic Security in PKIs
At the core of PKIs lie asymmetric and symmetric cryptography principles, facilitating secure data exchange and ensuring transaction authenticity, confidentiality, and integrity.
Within PKIs, users, referred to as “Subscribers,” encompass diverse entities, including individual end users, web servers, embedded systems, connected devices, and applications executing essential business processes.
Asymmetric cryptography empowers users, devices, and services within the ecosystem with a key pair comprising a public and private key component. The public key, available to anyone within the group, enables data encryption, ensuring only the intended recipient can decrypt and access information.
Secondly, it facilitates the verification of digital signatures, verifying the sender’s authenticity and ensuring the data’s integrity.
In contrast, the private key assumes a more exclusive role, demanding utmost secrecy. Only the entity to which it belongs has access to this key, and it is primarily utilized for tasks such as decryption or the creation of digital signatures.
The private key ensures that encrypted data remains secure and digital signatures are trustworthy.
How Adequate Separation of Duties in PKIs Are Crucial?
In a robust Public Key Infrastructure (PKI), properly separating duties is paramount to maintaining security and integrity. Weak controls over signing keys can create vulnerabilities, even if the keys remain uncompromised. It could lead to the misuse of the certification authority (CA) and open the door for malicious actors to exploit the system.
One critical risk associated with inadequate separation of duties is the potential issuance of malicious certificates. Malicious actors could exploit this loophole to issue certificates that enable devices or users to impersonate legitimate entities, facilitating man-in-the-middle attacks.
Furthermore, attackers could digitally sign malware, making it appear to originate from a trusted source, and propagate it with apparent authenticity.
Organizations must implement proper security controls during the design phase to establish a secure PKI. It involves ensuring a clear separation of CA roles and setting strict policies to prevent individuals from performing multiple CA roles simultaneously.
BY IMPLEMENTING SUCH CONTROLS, the PKI can safeguard itself from potential internal threats and unauthorized actions.
Which is the Pivotal Part of the Security Framework?
A crucial aspect of this security framework is the establishment of policies and procedures to enforce the proper separation of duties. These measures must also account for contingencies when team members leave the organization, ensuring the PKI remains resilient and secure even during personnel changes.
In the initial design phase of a PKI, emphasis must be placed on incorporating technological solutions that enable and enforce the separation of duties policy. By leveraging technology, organizations can enhance the effectiveness of their security controls and minimize the risk of human error or deliberate misuse.
The Growing Significance of PKIs in Today’s Digital Era
The world of business is ever-evolving. So, the role of PKIs has transcended beyond the boundaries of isolated systems, such as secure email or encrypted web traffic.
With changing business models leaning heavily towards electronic transactions and digital documentation and a surge in Internet-connected devices within corporate networks, the importance of PKIs has multiplied exponentially.
The contemporary landscape demands PKIs to support many applications, users, and devices, all intricately connected within complex ecosystems.
No longer limited to specific use cases, PKIs now form an integral part of various business processes, catering to a diverse range of applications and devices.
Recommended: Ensure IoT Identity Security at Scale with the Excellence of PKI
Moreover, as governments and industries tighten their data security regulations, mainstream operating systems and business applications seek the assurance provided by an organizational PKI.
rust has become a critical currency in the digital realm, and a robust PKI is the bedrock for instilling confidence in electronic transactions and interactions.
PKIs are no longer the reserve of niche security measures; they have emerged as indispensable guardians of trust in the modern business landscape.
From securing sensitive communications to validating the identity of users and devices, PKIs play a multifaceted role, ensuring the integrity and confidentiality of data across diverse digital scenarios.
Wrapping up
PKI forms the foundation of code signing, guaranteeing that software remains tamper-free and reliable throughout its lifecycle. Through deploying cryptographic keys, digital certificates, and Certificate Authorities, PKI offers a robust security framework that developers and users can trust without reservation.
Embracing PKI in code signing is a proactive step in safeguarding software integrity and maintaining users’ trust in digital platforms.
The increasing importance of PKIs is a testament to their adaptability and necessity in the face of digital transformation. As businesses rely more heavily on electronic interactions and the number of Internet-connected devices surges, PKIs serve as a vital linchpin for establishing trust and safeguarding sensitive information.

Protect the Integrity and Authenticity of Software
Add a digital signature on a file, program, software, or driver using Trusted Code Signing Certificate from trusted root certification authority using a secure public key infrastructure (PKI).
