Windows Security: Detailed Guide to Understand Security Baselines

The security of your organization’s data and systems is at the top. As a leading provider of operating systems and applications, Microsoft understands the criticality of safeguarding its customers’ sensitive information.
With products like Windows, Windows Server, Microsoft 365 apps for enterprise, and Microsoft Edge, they strive to offer secure solutions that inspire confidence.
While Microsoft’s products are designed with security in mind, many organizations still seek greater control over their security configurations.
The need for fine-tuning security features to meet specific requirements has led to the development of security baselines. These baselines act as a guiding compass, assisting organizations in configuring their systems effectively.
This blog aims to be your ultimate resource in understanding security baselines for Windows and Windows Server environments. We will explore these pre-configured standards rather than crafting custom configurations.
By adopting industry-standard security baselines, your organization can enhance its security posture, increase flexibility, and even reduce costs.
Learn about Windows security and discover how security baselines can empower your organization to build a robust and resilient defense against modern threats. Let’s embark on this journey together and unlock the full potential of your security environment.
Security Baselines to Strengthen Your Organization’s Defense
Today, almost every organization faces the ever-present specter of security threats regardless of size or industry. Cyberattacks are becoming increasingly sophisticated, targeting diverse vulnerabilities across the digital landscape.
However, the nature of these threats can vary significantly depending on the organization’s specific focus and area of operation.
For instance, an e-commerce company might prioritize safeguarding its internet-facing web applications, shielding its customers’ sensitive data from potential breaches.
On the other hand, a hospital must concentrate on protecting confidential patient information, ensuring it remains strictly accessible only to authorized personnel. Despite these distinct concerns, all organizations aim to secure their applications and devices.
This is where security baselines come into play—a crucial aspect of modern cybersecurity strategies. At its core, a security baseline refers to a carefully crafted collection of Microsoft-recommended configuration settings.
These settings are meticulously curated based on inputs and insights from various sources, including Microsoft’s security engineering teams, product groups, partners, and valuable feedback from esteemed customers like you.
The primary purpose of these security baselines is to furnish organizations with a clear and concise roadmap to bolster their digital fortifications.
Recommended: Windows 11 Security Measures: Safeguarding Home and Small Business PCs
Organizations can align their devices and applications with recognized security benchmarks by adhering to these pre-configured standards. This alignment ensures that your systems comply with security standards, safeguarding your vital assets and data from potential breaches.
Furthermore, the security implications of each recommended setting are thoroughly elucidated, providing organizations with a comprehensive understanding of their decisions.
This transparency empowers organizations to make informed choices while configuring their security settings, strengthening their resilience against emerging threats.
Significance of Security Baselines in Simplifying and Strengthening Cybersecurity
Grappling with the sheer complexity of security settings can be overwhelming, often leaving IT professionals and policy-makers needing help to make informed decisions.
Consider the staggering number of group policy settings for Windows 10 alone—over 3,000—which doesn’t even include the additional 1,800 settings for Internet Explorer 11.
While not all these settings are security-related, identifying the pertinent can be like finding a needle in a haystack. Each setting requires careful analysis to understand its security implications and determine the appropriate value for your organization’s needs.
Recognizing this predicament, Microsoft seeks to empower its customers with a solution that streamlines the security configuration process while drawing upon expert insights from multiple sources.
Enter security baselines—an indispensable boon for customers. These baselines are the culmination of collective expertise from Microsoft’s specialists, trusted partners, and valuable feedback from customers like you.
By consolidating the wealth of knowledge, security baselines distill the most relevant and practical security settings into consumable formats, such as group policy object backups.
This simplifies and accelerates the deployment process, making it more manageable and less time-consuming. With security baselines, organizations can confidently fortify their systems with the optimal configuration settings, bolstering their defenses against potential threats.
Options and Importance of Firewall and Encryption-
Ensuring the integrity of organizational networks is paramount. Two crucial components in achieving this level of security are firewalls and encryption. Let’s explore the significance of each:
Firewalls – The First Line of Defense:
Firewalls act as a protective barrier for an organization’s network, serving as the first defense against potential threats. These software-based tools enforce rules on data transactions, both within the network and between different networks.
By monitoring and controlling incoming and outgoing data, firewalls prevent unauthorized access and safeguard sensitive information.
Within an organization’s network, firewalls scrutinize all data packets, allowing legitimate traffic and blocking malicious attempts. Similarly, when data moves between different networks, firewalls regulate the flow and verify the authenticity of connections. This proactive approach significantly reduces the risk of unauthorized access and potential cyberattacks.
Encryption – Safeguarding Data in Transit:
Data encryption is a critical layer of protection, ensuring the confidentiality and privacy of sensitive information during transmission. Encryption tools encode data as it moves from one device to another, rendering it unreadable to unauthorized individuals.
Even if a hacker bypasses the firewall and gains access to an organization’s data transfers, encryption prevents them from understanding the content without the decryption key.
Encryption uses complex algorithms to scramble data into ciphertext, making it unintelligible to anyone without the corresponding decryption key. This ensures the data remains secure and indecipherable to malicious actors even if intercepted during transit.
The Synergy of Firewall and Encryption:
When employed together, firewalls and encryption form a formidable defense against cyber threats. Firewalls act as gatekeepers, monitoring data traffic and preventing unauthorized access at the network level.
Encryption, conversely, guarantees that data remains protected even if unauthorized access occurs, rendering intercepted data useless without the decryption key.
Windows Editions and Licensing Requirements for Security Baselines
As organizations seek to fortify their digital defenses, understanding the compatibility of Windows editions with security baselines becomes crucial.
The table below elucidates the Windows editions that effectively support security baselines:
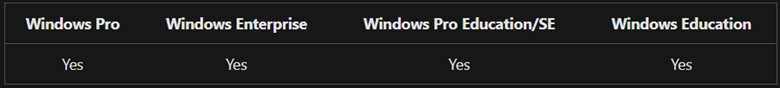
To further clarify the entitlements for security baselines, they are granted by specific licenses as outlined below:
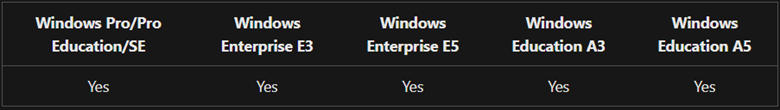
It is evident from the above information that organizations equipped with Windows Pro, Windows Enterprise, Windows Pro Education/SE, and Windows Education editions can avail the benefits of security baselines.
Licensing entitlements grant access to Windows Pro and Windows Pro Education/SE security baselines. Similarly, Windows Enterprise E3 and E5, along with Education A3 and A5 licenses, provide the necessary entitlements for utilizing security baselines effectively.
Top Windows Security Tips for Your Device and Data
Here are some top Windows security tips that can help protect your device and data from potential threats:
Make use of Unique Passwords:
Strengthen the security of your endpoints by employing solid passwords. A strong password should be unique, incorporating a mix of uppercase and lowercase letters, numbers, and special characters.
Avoid using personal information like your name or birthdate in passwords. For easier management of strong passwords, consider using a reliable password manager.
Update Your Windows Device:
Regularly updating your Windows device is one of the simplest yet most effective ways to enhance security. Windows updates often include critical security patches that address vulnerabilities and safeguard your device from potential exploits.
To ensure your device stays up to date, you can check for updates in the Windows settings or enable automatic updates for added convenience.
Get an Antivirus Software Immediately:
Employ reliable antivirus software to defend your Windows device against malware and viruses. Use Microsoft’s built-in antivirus program, Windows Defender, which offers real-time protection, automatic updates, and cloud-based security features. Additionally, various third-party antivirus programs are available for added protection.
Enabling the Two-Factor Authentication (2FA):
Add an extra layer of protection to your device and accounts by enabling two-factor authentication. This requires you to provide a unique code, often sent to your phone or email, and your password during login. Two-factor authentication significantly reduces the risk of unauthorized access, enhancing overall security.
Data Protection via Encryption Process:
Encrypting your data provides an additional layer of security, ensuring unauthorized access is thwarted. Windows offers BitLocker, a built-in encryption tool that can encrypt entire drives or specific files. Encrypting your data protects it from being accessed or read without the correct authentication.
Recommended: Roadmap to Secure Code Signing to Safeguard the Digital World
Take Necessary Precautions Against Phishing:
Stay vigilant against phishing attempts, where attackers pose as trustworthy entities to deceive you into revealing sensitive information.
Be cautious of suspicious emails, messages asking for personal information, or offers that seem too good to be true. Double-check email addresses and URLs before clicking links, and promptly report any suspicious activity.
These essential security tips can bolster the protection of your Windows device and fortify your digital defenses. Embrace a proactive approach to security, keeping abreast of the latest threats and best practices to ensure a safe and secure computing experience.
How to Utilize Security Baselines for Your Cyber Defenses?
Microsoft offers a powerful tool in the form of security baselines, enabling organizations to fortify their devices and user configurations with Microsoft-recommended security settings. Let’s explore how you can effectively leverage security baselines:
Ensuring Compliance:
Security baselines serve as a benchmark for best practices in security configurations. You can ensure compliance with the recommended standards by comparing your organization’s user and device settings with the baseline.
This helps identify potential vulnerabilities and areas that require attention, allowing you to strengthen your overall security posture.
Configuring Settings:
Implementing security baselines involves configuring various settings on your devices. This can be achieved through various management tools such as group policy, Microsoft Configuration Manager, or Microsoft Intune.
By applying the specified setting values from the baseline, you can align your devices with the desired security configurations, creating a robust defense against potential threats.
Your Destination to Access the Security Baselines!
Microsoft offers several convenient ways to access and utilize security baselines:
Microsoft Download Center:
You can download the security baselines directly from the Microsoft Download Center. The Security Compliance Toolkit (SCT) is available for download, which not only includes security baselines and comprises tools that aid administrators in managing these baselines effectively.
The SCT equips you with the necessary resources to streamline the implementation and management of security configurations.
Mobile Device Management (MDM):
MDM security baselines function like the Microsoft group policy-based security baselines for those using Mobile Device Management solutions.
Integrating these baselines into your existing MDM management tool becomes a seamless process. Specifically, Microsoft Intune offers easy configuration options for MDM security baselines on devices running Windows 10 and Windows 11.
Incorporating security baselines into your organization’s cybersecurity strategy empowers you to mitigate risks and safeguard your critical assets proactively.
By adhering to Microsoft’s industry-leading security recommendations, you can stay ahead of emerging threats and create a robust digital environment.
Essential Principles of Baseline Definitions
Microsoft’s approach to baseline recommendations follows a streamlined and efficient path, with fundamental principles that serve as the foundation for this approach. Let’s delve into these essential principles:
Targeting Security-Conscious Organizations:
The security baselines provided by Microsoft are tailored for organizations that prioritize security and maintain a well-managed infrastructure. These baselines assume that standard end users do not possess administrative rights.
By restricting administrative privileges, organizations can reduce the potential for unauthorized system modifications, minimizing security risks.
Balancing Security and Operational Impact:
A crucial tenet of baseline definitions is striking a delicate balance between security enhancement and operational implications. Each enforced setting must serve a clear purpose in mitigating contemporary security threats.
However, it must also be carefully assessed to ensure it does not cause operational issues that outweigh the risks it addresses. This cautious approach prevents inadvertently disrupting critical operations in the pursuit of heightened security.
Default Enforcement for Insecure States:
Baselines are pivotal in promoting secure configurations, mainly when dealing with default settings. If a baseline identifies a default setting that could lead to an insecure state, it will enforce the appropriate secure value.
The underlying rationale is to preempt potential vulnerabilities by establishing secure defaults.
Addressing Misinformed Administrative Decisions:
When dealing with settings that may lead to insecure states and require administrative rights to change, baselines consider the possibility of misinformed administrative decisions. In such cases, the baseline enforces the default value, ensuring that even inadvertent or poorly informed choices do not compromise security.
Microsoft’s security baselines aim to create a comprehensive and pragmatic approach to cybersecurity. This approach empowers organizations to fortify their defenses, adapt to emerging threats, and maintain operational efficiency.
Understanding these principles equips IT professionals and decision-makers to make informed choices while implementing security baselines, thus elevating the overall security posture of their organization.
Boost Productivity on Your Windows Devices: Top Tips to Maximize Efficiency
In the fast-paced digital world, maximizing productivity on your Windows devices is crucial for staying ahead. With a myriad of features and tools at your disposal, here are some productivity tips to help you work smarter and more efficiently:
Kiosk Mode:
Utilize Kiosk mode to enhance security and productivity in specific scenarios. By configuring your Windows device to run a single app or a set of apps, you can limit access to other applications and settings.
This is particularly useful for public kiosks, digital signboards, or point-of-sale devices. Kiosk mode streamlines device management, preventing unauthorized access and minimizing distractions.
To set up Kiosk mode using Assigned Access, create or select a user account, enable Assigned Access in Settings, choose allowed apps or websites, and customize settings. Exiting Kiosk mode can be done by pressing the Windows key + Ctrl + Esc keys together.
Regular Data Backups:
Safeguard your valuable data by performing regular backups. Windows Backup, a built-in tool, allows easy data backup. Consider using cloud-based backup solutions like OneDrive or Google Drive for additional security. This ensures data availability even during system failures or malware attacks.
To back up your data on a Windows device, navigate to Settings > Accounts > Windows Backup.
Organizing Device Efficiently:
Unified Endpoint Management (UEM) solutions offer comprehensive device management, enhancing security and productivity. Key features of effective device management include easy enrollment, remote supervision and monitoring, and remote troubleshooting.
A centralized platform to manage and secure all Windows devices streamlines IT administration tasks, enabling swift support and maintenance.
Files and Folders must be Managed:
Adopt a structured approach to organizing files and folders to save time and reduce stress. Create a logical folder structure and implement consistent naming conventions for quick file retrieval. Utilize File Explorer to drag and drop files into their designated locations effortlessly.
Use Productivity Tools:
Explore productivity tools specifically designed for Windows to optimize your workflow. Embrace popular tools like Microsoft Office Suite, Trello, Evernote, Slack, and Grammarly. These tools facilitate time management, organization, and efficient communication.
When selecting productivity tools, consider their compatibility with your workflow, hardware, and software. Prioritize user-friendly tools that seamlessly integrate with your daily tasks.
Wrap up
Security baselines serve as invaluable tools in the battle against the ever-evolving landscape of cyber threats. By adhering to these meticulously crafted guidelines, organizations can enhance their security posture, build a robust defense, and instill confidence in their stakeholders.
In the subsequent sections of this blog, we will explore in depth the benefits and best practices of implementing these Microsoft-recommended security baselines. Together, let us embark on this journey to fortify your organization’s digital stronghold and confidently navigate the realm of cybersecurity.
“Safeguard your Windows Apps and Software Codes with Authentic Code Signing Certificates“
Trusted and Authentic Code Signing Certificate Starts at Just $199.99/yr
