What Is Timestamping in a Code Signing & What’s Its Importance?
Timestamp to Preserve & Keep Your Digital Signature Valid Even After Code Signing Certificate Expires
Code Signing Certificate assures users that software they’re downloading or installing is coming through a trusted source and hasn’t been modified since its signing. Also, an operating system like Microsoft Windows requires code signing to guard users against those that don’t guarantee its authenticity.
Like SSL/TLS certificates, trusted code signing certificates by Certificate Authorities are provided to software development companies or individuals looking to sign their software digitally. So it can be seen as trusted sources and avoid unknown publisher warning messages that create doubts regarding software authenticity.
Unfortunately, it often happens that even signed software stops running abruptly and may even start showing warning messages all of a sudden. And one of the primary reasons is timestamping. So yes, if your signed software or an application isn’t timestamped, then it’ll start displaying a warning message to your users once your code signing certificate expires.
What’s Timestamping in Code Signing?
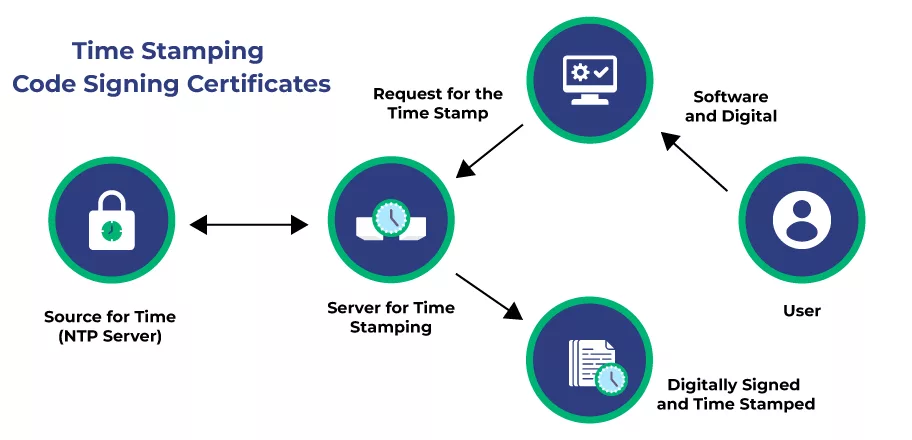
Timestamping is an essential feature in all types and validation of software signing certificates that freezes your digital signature. Because of timestamping, the operating system accepts your signed software even after the expiry date of a Code Signing Certificate surpasses.
So, whenever the timestamped digital signature gets evaluated, the timestamp feature will allow the signature validity to be verified against the time and date it’s signed rather than the current time at the time of execution. In contrast, the signature without a timestamp is verified against the current date and time.
So, if you’ve distributed your software a few years back and your certificate is expired, the signature will also expire and won’t remain valid. Ultimately, it’ll prevent your software user from executing your already signed and installed software.
Put simply, the digital signature embedded on your signed software is checked whenever the user runs it. It means if your code signing certificate expires and it wasn’t timestamped, then the software will stop working for all the users abruptly.
Similarly, that’s true that software is built to be used for an extended time range and, because of this, timestamping is considered an essential part of your signing process so the software can continue to be used for years.
Lastly, the timestamp is signed and protected by your Certificate Authority (CA) like Sectigo, making it resistant to spoofing or tampering. Similarly, your timestamped software remains valid even if your CA from whom you purchased the code signing certificate gets distrusted.
How Does a Timestamping Work?
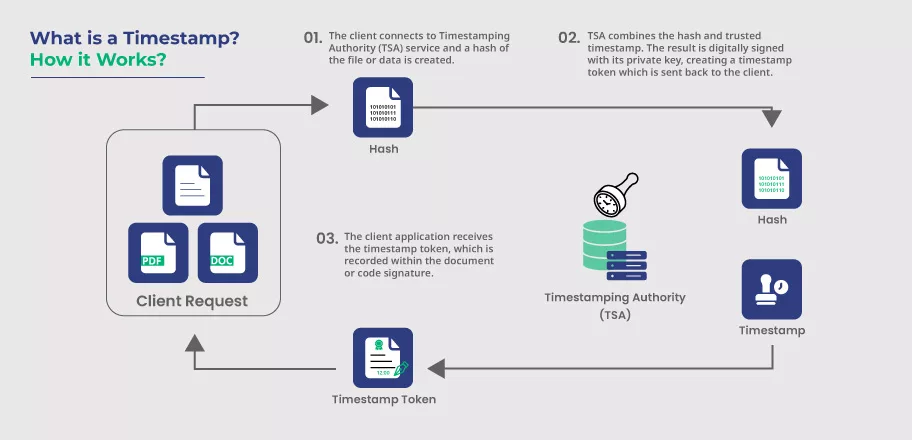
Timestamping makes use of PKI (Public Key Infrastructure) for applying timestamps. Let’s look at it stepwise for a better understanding of the working of timestamp:
- Software or application creates its hashed value, and then a unique identifier of the software or an application is timestamped, and it’s sent further to the TSA (Timestamp Authority).
- From thereon, even if the slightest change occurs in a software code, it’ll require communicating about that change with the TSA server.
- The TSA merges the hash and other related information, including authoritative time. And then, digitally signed software with the TSA’s private key creates a timestamp token and gives it back to the client. Similarly, the timestamp token has information regarding the client application that requires verification by the timestamp later on.
- Likewise, once the client software gets a timestamp token, it’s recorded within the digital signature.
Whenever the digitally signed and timestamped software or application is executed in the future, it’ll use the TSA’s public key to validate the timestamp and verify whether it came through a trusted TSA. Likewise, it’ll also re-calculate the hash value of the original data, which is compared with the mentioned above in the first step.
And, if any change is seen since the timestamp is applied to the software, the hash verification will fail and generate a warning message saying the software code is altered and shouldn’t be trusted.
When to Timestamp?
Timestamping is usually done in steps one to two. To be precise, once your software or application is hashed, and before a digital signature is added, the server makes the signature call a timestamping server.
Usually, CAs (Certificate Authorities) like Sectigo and DigiCert have their own timestamping server and the public one. And, whatever server you configure will respond with a timestamp, including the signature and the hash value.

Summary
Timestamping your software while digitally signing with a code signing is one of the vital parts. If there wasn’t timestamping feature, it might have created an issue for your software users.
For instance, digitally signed software that isn’t timestamped starts showing warning messages to users once a code signing certificate expires, which creates trust issues. On the contrary, timestamping gives assurance that the signature will remain valid and trusted even after your code signing certificate expires or is even revoked.
| Buy Certificates | Price |
| Comodo Code Signing Certificate | $225.99/yr |
| Sectigo Code Signing Certificate | $225.99/yr |
| Certera Code Signing Certificate | $199.99/yr |
| DigiCert Code Signing Certificate | $369.99/yr |
