What is a PUA? How to Detect and Block Potentially Unwanted Applications?

PUA or Potentially Unwanted Applications are preferred by no one until or unless they are required to support critical processes or infrastructure. These kinds of applications slow down other processes and let the system suffer to retain or upgrade its performance.
But the good news is you can block PUAs and save your system from suffering. Further, you will find a brief about PUA and how you can block it on Windows, Linux, and macOS-based devices.
What is a Potentially Unwanted Application (PUA)?
Potentially unwanted applications are considered grayware software that consume additional resources, slow down the system, and sometimes even execute malicious programs. PUA apps are not always illegitimate, as some legit software can consist of components that behave in such a manner.
In addition, these unwanted applications can become a high-risk security threat. Attackers can take advantage of it to crash the system, hide and spread malware, and even congest the network.
Furthermore, a potentially unwanted application can enter your system in the following ways:
- You have installed a legit application, and a PUA was bundled with it.
- You clicked on a malicious link, file, ad, or mail, and PUA was downloaded automatically.
- You download and install a cracked/spoofed version of the software from a third-party site, and it contains a malicious PUA file.
What are the Most Common Detected PUA?
Software solutions that detect and block potentially unwanted applications divide them into the following categories/types.
Bundling Software
A software that tells the users to download another software integrated into it is called bundling software. It’s not recommended to install such software, as the embedded installation file can be of a malicious application.
However, if all the software bundled together fulfills your criteria and their sources can be trusted, you can download them.
Crypto-mining Software
Crypto-mining software runs in the background and uses the computational resources for mining the cryptocurrencies. Sometimes, the attacker creates a network of botnets and uses their resources simultaneously to mine digital currency, such as Bitcoin, Litecoin, Dogecoin, and Ethereum.
Marketing Software
Marketing software is like a backdoor or spyware malware. It is used by agencies to monitor user/customer activity for the following purposes:
- To Improve the Marketing Campaigns.
- To Enhance User Experience.
In addition to this, advertising software is also used in collaboration. Marketing software collects the data, and advertising software uses that data to filter out ads and display them to the user. Thus, the primary aim is to sell services or products and increase the company’s ROI.
Command and Control Malware
This kind of PUA malware connects your system to the hacker’s instruction server. A lot of resources are utilized if such malicious files get installed. You can refer to the following table for more insight.
| Resource | Purpose of Additional Utilization |
| Network | To establish a constant connection with the hacker’s instruction server. |
| Storage | To download, store, and install the malicious files being sent by the attacker. |
| CPU | To run in the background, maintain connection, and execute the attacker’s instructions. |
Exploit
An exploit is a file containing the code to use a vulnerability in an app, driver, or firmware to perform some illegitimate activity on the system. It also runs in the background and is difficult to detect if encrypted and integrated within some other file.
Evasion Software
It’s a software that evades itself from security solutions. Whenever you start the system scanning or a security mechanism is enabled, an evasion software will change its functionality. The primary purpose of such software is to not get detected and perform its functions.
Torrent Software
Torrent software is used to support the upload of a file present on your system. It connects your system to a peer-to-peer or P2P network, resulting in using the additional resources and lowering the speed, performance, and bandwidth availability.
Rogue Security Software
Rogue security software is becoming quite normal nowadays. These potentially unwanted applications showcase themselves as legitimate but don’t provide any security to the system. In addition, fake alerts are displayed, additional resources are utilized, and manipulation is performed to convince end-users to pay for better security.
How do you Block PUA on your Preferred Operating System?
In this section, you will learn about the procedures and tools to use for detecting and blocking potentially unwanted applications.
To block the PUA on Windows, follow the below process:
Step 1: Click on the “Start“, one with the Windows icon.
Step 2: Go to “Settings” >> “Update & Security” >> “Windows Security” >> “App & Browser control” >> “Reputation-based protection settings”.
Step 3: Enable the “Potentially unwanted app blocking” and check the “Block apps” and “Block downloads” checkboxes.
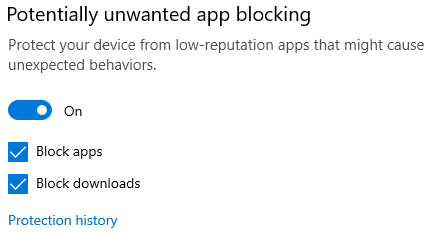
There’s only one drawback of this built-in functionality, that PUA downloads through Microsoft Edge will only be blocked. Further, a warning will be shown as below whenever a potentially unwanted application is detected.
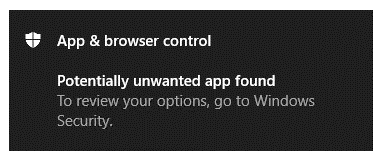
You can click on the notification to navigate to the “Virus & threat protection” interface. You will get the four primary options to execute on PUA, which are as follows:
- Manual steps required
- Remove
- Quarantine
- Allow on device
You can choose any of the actions per your requirement and use case scenario.
To Block PUA on Linux, Undergo the Following Procedure:
For the Linux operating system, Microsoft Defender solution will be used. It can be installed and used on Linux-based endpoint systems for detecting and blocking potentially unwanted applications.
Firstly, you should install the Microsoft Defender, then open your terminal and run the following command:
mdatp threat policy set --type potentially_unwanted_application --action [off|audit|block]Further, instead of “off|audit|block”, you are required to choose only one option. The “off” will disable the tool. The “audit” option will log the PUA and “block” will directly eliminate the detected PUA.
To Block PUA on macOS, use the Below Process:
Microsoft Defender is also available for macOS devices. You can install it and run the command as Linux on your system’s terminal.
mdatp threat policy set --type potentially_unwanted_application --action [off|audit|block]This command will help you define the relevant defender actions, which are off, audit, and block.
Concluding Up
Potentially unwanted applications are hard to detect as they run in the background. However, their impact on the system can be quite worse. PUAs can empty your storage, network, and CPU resources if they are not blocked promptly.
If you use a Windows OS, then you should enable the PUA security. And if you use a Linux or macOS system, then Microsoft Defender will help you detect and block PUAs.

