What is Digital Signature Spoofing? How to Fix this Vulnerability in the LibreOffice Suite?

LibreOffice is a highly used productivity suite that helps organizations create business documents. All the apps under this suite offer seamless functionality. However, on 11th October, 2021, three digital signature spoofing vulnerabilities were discovered in it.
But the good news is all the vulnerable loopholes are now patched, and the LibreOffice is safe from signature spoofing attacks. To discover and fix the vulnerabilities in your LibreOffice suite, undergo this blog.
Digital Signature Spoofing: What and Why?
Whenever software is released, the organization owning the application digitally signs it using a Code Signing Certificate. This signature is unique and helps the firms distribute their software as legitimate and authentic. Also, when an end-user tries to install the software, the operating system verifies the digital signature.
Further, if the signature is classified as valid, the software is installed. Otherwise, an Unknown Publisher Warning is displayed. But, with the digital signature spoofing attack, illegitimate actors, such as hackers, are able to distribute malicious files in the name of authentic software. They spoof the signature of a validated firm and use it to sign their malware.
For instance, suppose that an attacker integrates a malicious file with an MS Word application and digitally signs it using a spoofed Microsoft signature. Now, the end-user doesn’t know that the MS Word file contains viruses, bots, or similar components.
In addition, when the OS checks that MS Word package, it will consider it legit due to the availability of spoofed Microsoft’s digital signature. As a result, malware will be installed on the host machine.
The LibreOffice Suite Digital Signature Spoofing Vulnerabilities
For the LibreOffice suite, a total of three digital signature spoofing vulnerabilities were identified. The list of the vulnerabilities is as follows:
CVE-2021-25633
Every LibreOffice ODF file contains a digital signature to ensure the receiver that the content’s integrity is maintained. However, with the exploitation of the CVE-2021-25633 vulnerability, attackers were able to modify “documentsignatures.xml” or “macrosignatures.xml stream.”
Due to this, multiple certificates were combined together, bypassing the system’s security to categorize the file as legit.
CVE-2021-25634
Timestamping is a feature of a code signing certificate that enables the retention of the authenticity of software, even after the signature/certificate expires.
Under the CVE-2021-25634 vulnerability, attackers were manipulating the timestamping functionality. Primarily, signature wrapping attacks were being carried out, making systems believe an invalid/expired certificate was valid.
CVE-2021-25635
The CVE-2021-25635 vulnerability enabled the attackers to conduct a certificate validation attack. Due to this, illegitimate actors were signing the ODF documents with an untrusted/self-signed code signing certificate. Following this, they also changed the signing algorithm with an unknown algorithm.
As a result, the digital signature with an invalid algorithm was showcased as a valid one, leading the system to trust it and install the malicious software without any warning.
How To Fix LibreOffice Signature Spoofing Vulnerabilities?
All three LibreOffice suite vulnerabilities (CVE-2021-25633, CVE-2021-25634, CVE-2021-25635) are resolved. And you can also fix them by upgrading to the 7.1.2 version of the software. You can directly download and install the newer version from the official website.
However, if you are on a Linux-based system, you can update from the command line interface by following the below procedure.
In this tutorial, we are using Ubuntu OS.
Step 1: Confirm the LibreOffice suite version installed on your system.
LibreOffice -versionStep 2: Verify the version information. If it’s below or equal to 7.0.5, execute the following process.

Step 3: Update the cache and add the PPA repository by running the below command.
sudo add-apt-repository ppa:libreoffice/ppa && sudo apt updateStep 4: Install the PPA associated with the LibreOffice suite.
sudo apt install LibreofficeStep 5: After the installation of PPA and completion of the update process, check the LibreOffice version.
LibreOffice –versionStep 6: Ensure that a minimum of LibreOffice 7.1.12 is installed.
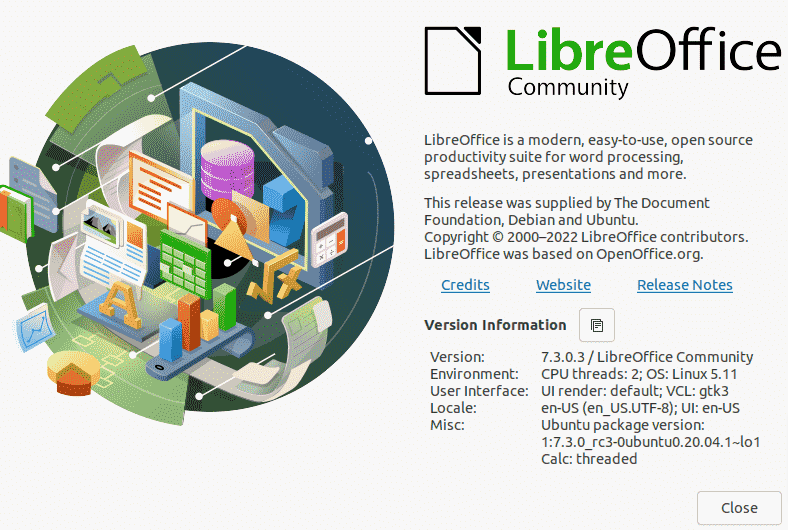
After performing this update process, all three vulnerabilities will be fixed.
Concluding Up
The digital signature spoofing vulnerabilities in LibreOffice were enabling attackers to sign ODF files with invalid algorithms, bind certificates together, and manipulate the signature stream.
All the vulnerabilities are present in the 7.0.5 and 7.0.6 versions of the LibreOffice suite. Therefore, you should immediately update to the 7.1.12 or above version to fix them. As a result, you will be safe from a signature spoofing attack.
