Code Signing Security: Publishers Getting More Aware After GitHub’s Certificate Breach

In this highly technology-driven world, no company is completely safe from cyber-attacks. Even one of the IT giants – GitHub faced exploitation, leading to the stealing of their Code Signing Certificates. There was only minimal impact on the organization and its software products.
But, from the incident, almost every small, medium, and large-scale company has got aware of securing their software publisher certificates.
To understand the Code Signing Certificate security, let’s start by looking at the GitHub incident.
The GitHub Code Signing Certificate Breach Incident
On December 6th of the recent year (2022), GitHub faced a cyber-attack, which made attackers successful in stealing the Code Signing Certificates. As per the statement given by GitHub officials, malicious actors utilize the Personal Access Token of an internal machine to intercept the network and execute their illegitimate operations.
Further, GitHub was not far behind to spot the attack, as its security team detected the breach on the very next day (December 7th, 2022).
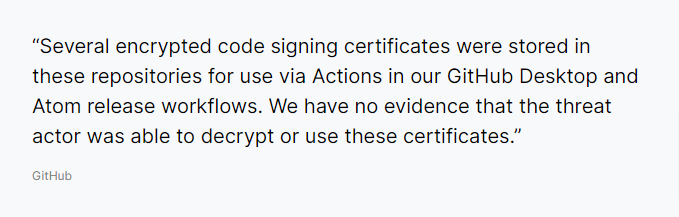
And instantly they get started with the investigation to discover impacted systems, network routes, customers, and their data. With this breach, everyone gets to know that GitHub also utilizes its repositories to store the source code of its software products.
As a result of the investigation, the GitHub security team finds that attacker stole the Code Signing Certificates used to sign the Atom application for Mac and Windows desktops.
Moreover, they also revealed the Certificate details, which include:
- Two DigiCert Code Signing Certificates. One expires on January 4, 2023, and the other on February 1, 2023.
- One Apple Developer ID Certificate, valid up to 2027.
A total of three Code Signing Certificates were with attackers, but during the investigation, there was no news defining their utilization of them. But, to mitigate the post-breach impact, GitHub has taken all precautionary measures.
Steps Taken By GitHub To Minimize Impact
Once GitHub was assured about the impacted Code Signing Certificate, customers, and applications, it instantly contacted the Certificate Authority. It led them to submit the certificate revocation request to disable attackers from signing any executable file on their behalf.
Moreover, GitHub notified all the users of the Atom application to downgrade to the previous version and not install any updates until further notice.
Also, the company representatives have provided February 2, 2023, as the official date, when breached certificates will get revoked. As a result, newer app versions signed using those certificates will not function and the hacker will get disabled from signing.
In addition, GitHub has also removed the latest Atom desktop app rollout to secure customers from downloading them. And also recommended everyone scan their systems for any malware.
Until the day of certificate revocation, their security team is constantly strengthening the GitHub ecosystem and patching loopholes.
Further, below app versions are at risk and you should also avoid installing and using them:
- GitHub Desktop Application Version 3.0.2 to 3.1.2
- Atom Application Version 1.63.0 and 1.63.1
For security reasons, GitHub is no longer hosting these versions and they will get relaunched with the new Code Signing Certificates.
What You Can Do To Prevent Code Signing Certificate From Breach?
After the GitHub Code Signing Certificate Incident, all organizations get aware of securing digital certificates. You must also protect your certificates and to efficiently do it, the below approaches can help.
Enable Password Protection
Always enable the password on the certificate file and share it only among authorized users to prevent its misuse. In addition, don’t provide system access to everyone on which the certificate is present. And you must utilize a strong password of a minimum of 15 characters consisting of alphabets, numerical and special characters.
Log and Audit
Whenever you utilize, import, or export a Code Signing Certificate, log the date, person’s name, designation, time, and system details. It will help you to discover who is accessing the certificate on which system and at what time. As a result, if you discover any suspicious activity, it will get easier to find and assess its root cause.
Utilize EV Code Signing Certificate
For an additional security layer, you must prefer Purchasing EV Code Signing Certificate. CA provide its private key in an external hardware security module, which is compulsory to plug into the system for executing the signing procedure. In case, your certificate gets breached, it will not work until the attacker doesn’t have a hardware token.
Prefer Different Testing and Production Certificates
In the complete software development lifecycle, you must prefer utilizing two Code Signing Certificates. One must get used during the testing phase and the other during final production. It will help you prevent hackers from exploiting pre-build software in online repositories.
Limit Signing With a Single Code Signing Certificate
You must not sign all applications and executable files with a single software, as if someone steals it you have to disable the functioning of all software signed with it. You can learn from GitHub, that if they were using the same certificate for all of their applications, then a breach would disrupt their functioning.
But, the stolen certificates were in use for limited applications, which minimizes the impact and helped GitHub continue business operations.
Concluding Up
The GitHub incident was a lesson for other software developers and publishers to secure their Code Signing Certificates. Many people are discussing, Whether the attacker was able to sign or not sign the application with stolen certificates.
But the main concern must be to implement appropriate approaches to prevent unauthorized access to your digital certificates.
If GitHub can be on target and then it’s a matter of concern. Therefore, you must password protect the certificate, prefer EV Code Signing Certificate and limit its usage.
Be Safe with Extended Validation Code Signing
Sign your software, application, drivers and more with EV(Extended Validation) Code Signing Certificate and get the highest level of security and trust!
