FIPS 140-3 Certification and Levels: FIPS 140-2 Vs 140-3
What is FIPS 140-3?
The Federal Information Processing Standard (FIPS) 140-3, is a collection of standards released by the United States government to examine cryptography modules. It explains how to design, develop, and run a cryptography module.
The National Institute of Standards and Technology (NIST) and Communications Security Establishment (CSE) created FIPS 140-3 to safeguard critical, unclassified information. The standard includes physical security, cryptographic key management, authentication, and other security criteria.
An approved laboratory must assess and verify cryptographic modules to meet the FIPS 140-3 standard. This certification protects sensitive data and prevents unauthorized access or alteration.
FIPS 140-3 replaces FIPS 140-2 and specifies revised federal security standards for cryptographic modules. The updated standards comply with ISO/IEC 19790:2012(E) and contain Annexes revisions permitted by the Cryptographic Module Validation Program (CMVP), which acts as a validation authority.
What is FIPS 140-3 Certification?

The most recent Federal Information Processing Standard (FIPS) for assessing the efficacy of cryptographic hardware is FIPS 140-3.
Organizations can use this certification to prove that their hardware systems have undergone official testing and validation by the United States and Canadian governments.
Enterprises are adopting more and more cloud-first PKI (Public Key Infrastructure) techniques to increase security and save costs.
These five factors explain why companies migrate their PKI solutions to the cloud.
Secure Digital Identities:
A cloud-first PKI offers a secure platform for managing digital identities, making determining who is accessing your data and apps simple. You can lessen the possibility of identity theft and illegal access to company networks with the help of this solution.
Safeguard Devices & Data:
Cloud-first PKI solutions guarantee that data is secured and secure. They also secure devices with capabilities like data encryption, remote wiping, and device/application notification.
The Difference of Keyfactor:
It offers a cloud-based PKI solution that meets all FIPS 140-3 requirements. Their software enables complete encryption and safe data storage, guaranteeing that you have total control over your digital identities.
Scalability:
Cloud-first PKI solutions offer great scalability as your business expands, enabling you to manage and deploy various identities for clients and workers effortlessly.
Cost Savings:
Unlike conventional on-premises solutions, switching to a cloud-based PKI strategy offers significant savings. It is simple to roll out to several places and requires no maintenance of servers or installation of licenses.
A certain approach to guarantee such cryptographic safety is to obtain FIPS 140-3 certification.
Latest Updates on FIPS 140-3
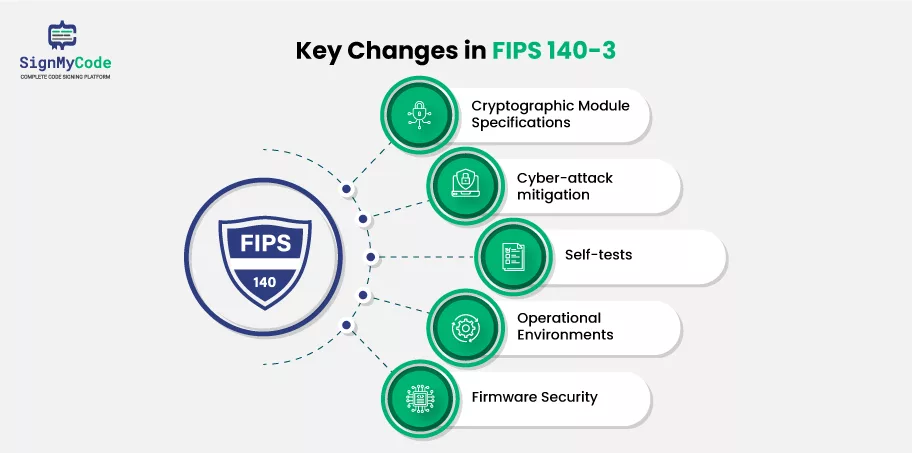
The newest standard for cryptography modules produced by the US National Institute of Standards and Technology (NIST) is FIPS 140-3.
It supersedes FIPS 140-2, which established the standards for a safe environment in which cryptographic modules might be utilized.
FIPS 140-3 went into effect on September 22, 2019, and the Cryptographic Module Validation Program (CMVP) will accept submissions for conformance with the new standard in September 2020. CMVP will continue to accept cryptographic module validations against FIPS 140-2 until September 22, 2021.
FIPS 140-3 contains revised security criteria, including additional module authentication protection requirements, increased physical security, and a more robust credential management environment. It also includes an enhanced, performance-based methodology that allows enterprises to be more flexible in deciding which security policies to apply.
Finally, FIPS 140-3 is a significant milestone for security professionals and the organizations they serve. It provides an enhanced set of security requirements for cryptographic modules. They allow more flexible implementation of security controls and speed up the cryptographic module validation process.
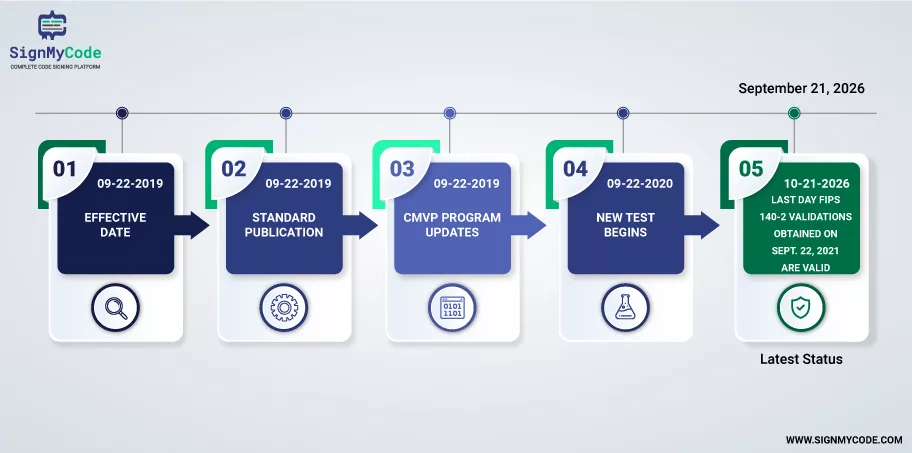
FIPS 140-2’s Latest Status:
FIPS 140-2 modules are valid five years after validation or until September 21, 2026, when they will be relocated to the chronological list. Even though these modules are on the historical list, CMVP encourages their purchase and use in existing systems.
For the most appropriate choice of cryptographic modules, CMVP suggests that customers investigate all modules that display on the Validated Modules Search Page and fulfill their criteria, no matter whether there is a validation of modules against FIPS 140-2 or FIPS 140-3.
Recommended: What is FIPS? Detailed Guide on FIPS 140-2
What are the Different Levels of FIPS 140-3?
The National Institute of Standards and Technology (NIST) created FIPS 140-3 as a collection of standards and security requirements to guarantee the security and dependability of cryptographic devices and modules used in secure IT systems. The standard, which has four levels, is in its third revision.
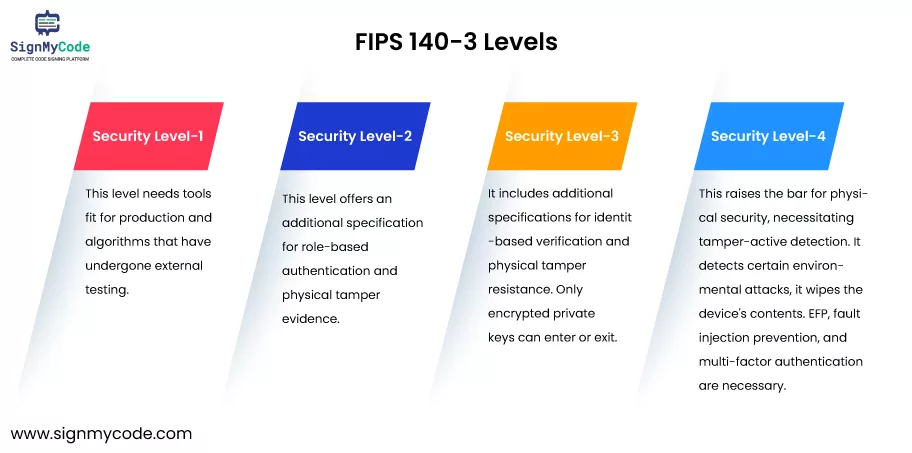
Level 1:
It needs tools fit for production and algorithms that have undergone external testing.
Level 2:
This level offers an additional specification for role-based authentication and physical tamper evidence.
Level 3:
It includes additional specifications for identity-based verification and physical tamper-resistance. The interfaces via which “critical security parameters” enter and exit the module must also be physically or logically separated.
Only encrypted private keys can enter or exit. The module must additionally detect and respond to out-of-range voltage or temperature in Level 3 (also known as environmental failure protection, or EFP), or else it must go through environmental failure testing, or EFT.
Level 4:
This raises the bar for physical security, necessitating tamper-active detection. FIPS 140-3 is gaining importance as more businesses and organizations attempt to safeguard their IT systems globally.
In the event that it detects certain environmental attacks, it wipes the device’s contents. EFP, fault injection prevention, and multi-factor authentication are necessary.
Therefore, it’s critical to comprehend the various FIPS 140-3 levels and select a cryptographic module that satisfies your organization’s security requirements.
What is the Difference Between FIPS 140-2 and FIPS-3?

You can clearly determine the differences between FIPS 140-2 and FIPS 140-3 based on the below detailed differentiations:
Functions:
The US federal government has established the FIPS 140-2 standard as a collection of guidelines for safe transmitting and storing sensitive data. It was optional to provide a maintenance position, but a module had to support both a crypto officer and a user role.
The most recent version of this security standard, FIPS 140-3, still includes all three jobs. However, only the crypto officer function is necessary.
Now that the user and maintenance roles are optional, businesses can select the roles most appropriate for their particular requirements.
The user position is for system users who require access to protected information. Still, the crypto officer’s job remains the principal role, with responsibility for the security of the cryptographic activities.
By conducting regular system inspections, the maintenance role is created to assist in preserving the system’s security. Organizations should take the time to select the appropriate role since each of the three is crucial to the system’s overall security.
Modules of Cryptography:
There are two security standards for cryptography modules: FIPS 140-2 and FIPS 140-3. With the understanding that all modules were hardware modules, the FIPS 140-2 standard was created in 2001.
Later, more specified hybrid, software, and firmware module types were introduced to the Information Guides (IGs) 1.9, 1.16, and 1.17.
The latest standard, FIPS 140-3, considers hardware, firmware, software, hybrid, and hybrid firmware module types. It offers an extra set of standards that must be satisfied by manufacturers of cryptographic modules and is an upgrade to the current FIPS 140-2 cryptographic module requirements.
FIPS 140-3 is more concerned with protecting cryptographic keys and guaranteeing the confidentiality of the data contained inside cryptographic boundaries. Additionally, it has more robust key management and authentication systems.
FIPS 140-3 mandates tighter control over the cryptographic module’s constituent parts and increased physical and virtual security measures. Businesses benefit from this increased security since it increases the reliability of the cryptographic modules and the services that depend on them.
Authentication Levels:
The National Institute of Standards and Technology (NIST) has established standards for encryption and authentication called FIPS 140-2 and FIPS 140-3.
The most recent version is FIPS 140-3, and FIPS 140-2 was the one before that. The inclusion of an extra level of authentication in FIPS 140-3 is the primary distinction between the two standards.
ISO 19790, which describes four layers of authentication, both standards are based. There are no criteria for authentication at Level 1, a minimal need for role-based authentication at Level 2, and identity-based authentication at Level 3.
While FIPS 140-3 mandates multi-factor identity-based authentication, FIPS 140-2 does not specify authentication requirements for Level 4.
These guidelines are intended to assist businesses in securing their networks, systems, and data. Organizations may guarantee that their networks are appropriately secure and safeguard both consumer and employee data by complying with the authentication standards in FIPS 140-2 and FIPS 140-3.
Boundaries of Cryptography:
Restrictive hybrid modules in FIPS 140-2 could only be verified to a Level 1 validation. Due to this, constrained hybrid modules could only offer the most fundamental kind of security.
The level at which a hybrid module may be verified under the new standard according to FIPS 140-3 is unrestricted. FIPS 140-3 broadened the scope of FIPS 140-2, which had a constrained scope and allowed for a more thorough and safe method of cryptographic border protection.
Numerous options for cryptographic border protection now exist because of FIPS 140-3’s addition of more lenient validation requirements. The FIPS 140-3 standard has broadened the use of cryptographic border protection, but there are other things to keep in mind as well.
For instance, more documentation could be needed to assure standard adherence, and procedures might have to be set up to track and handle security vulnerabilities.
Overall, the FIPS 140-3 standard, which incorporates a significant improvement over its predecessor, is the most recent and current standard for cryptographic border protection.
Wrapping up
Just to catch up on what we discussed earlier, the National Institute of Standards and Technology (NIST) of the United States has released the security standard FIPS 140-3 for cryptographic modules.
Based on the company’s security requirements and the application, it establishes four degrees of security requirements. Overall, FIPS-3 broadened the range of cryptographic border protection.
Allowing limited hybrid modules to be certified to a higher degree may improve the security of sensitive information and data.
Frequently Asked Questions (FAQs)
Q. What kind of cryptographic algorithms are FIPS 140-3 approved?
A: An algorithm or approach stated in a FIPS or NIST recommendation or incorporated in a FIPS or NIST recommendation (provided in an appendix or a document cited by the FIPS or NIST recommendation) is referred to as a “FIPS Approved Algorithm” in most cases.
Q. What Digital Signatures does FIPS 140-3 Employ?
A: Digital signatures guarantee data integrity and origin authenticity. DSA, ECDSA, and RSA are permitted only under specific conditions.
Q. How do Hash Functions Work?
A: A hash function converts a string of characters key) into a value of a predetermined length a hash value or hash). Although often smaller than the original, the hash value still represents the original string of letters.
Get FIPS 140-2 Code Signing Certificate
According to the New CA/B forum guideline, Now, user’s private key is generated and stored in an HSM (Hardware Security Module) that compliant with FIPS 140‐2 Level 2 and Common Criteria EAL 4+, or equivalent!
