A Developer’s Checklist To Curate Secure Software

Developing software requires immense focus on functionality and especially on its security. According to Intrusion Inc. cost of cybercrimes is increasing at a rapid speed and will cost around USD 10 Trillion.
In addition, HackerOne has also issued a report, defining an increase of 65,000 vulnerabilities in different applications and development platforms.
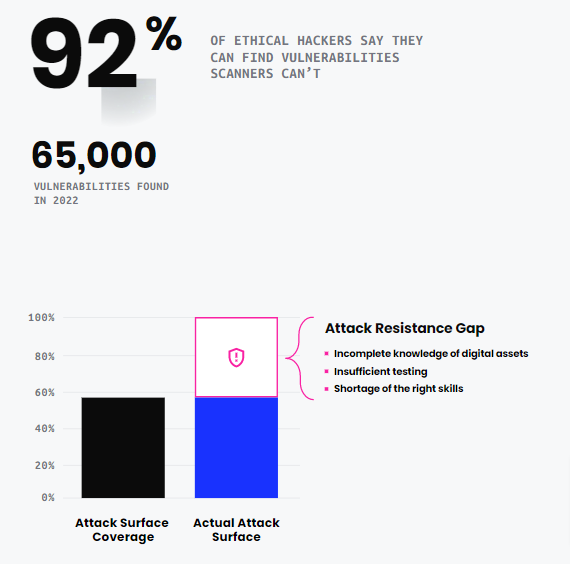
In addition, 50% of hackers don’t even report the vulnerability and take advantage for an extended period or until you patch it.
Such statistics are alarming and can impact any industry and organization. However, their impact can get reduced by adopting secure development approaches.
A developer must follow a checklist, defining all the necessary tasks to solidify software protection and prevent malicious activities. You don’t need to find anywhere else about it, as all the required details are present further.
So, let’s get started to create your checklist to curate secure software.
The Exact Meaning of Developer’s Checklist
Developer’s Checklist is a document, containing the tasks to complete while building an application, website, or any other software. The list consists of the important tasks, that highly focus on the CIA triad and software security for preventing a breach, malware, and malicious actors.
Further, whenever a development team or an individual developer has to start a project, a checklist must get generated. It would help to progress accordingly and curate secure software, providing all necessary functionality. In addition, it would help to maintain data integrity and confidentiality within the business constraints.
Gantt Charts can be an example of such a checklist, as it defines the tasks to get completed promptly.
Benefits of Creating a Checklist Before Starting Development
By creating a checklist, you can avail extraordinary leverages in the technology-driven industry, such as:
Fewer Vulnerabilities and Stable Software
With a checklist, you move further in the SDLC phases by focusing on software security, which results in less vulnerable loopholes. It prevents malicious actors from modifying the code, injecting malware, and gaining unauthorized access. Your app runs smoothly on each end-user’s device, providing a stable and seamless experience throughout.
Compliance with Relevant Industry Standards
A checklist helps to define the accurate standards and policies to follow for developing the application. For instance, if you need to create an app for processing medical data, then you can create a task to align with HIPAA guidelines. Similarly, you can use it for PCI-DSS, HITECH, NIST, ISO, and all other government regulations.
Seamless Accomplishment of Project Goals
In a checklist, you can define the project objectives along with the security mechanism required to protect each component. It will help you track the progress of overall development, including the integration of different modules, their testing, and patching according to the requisites.
As a result, you will get a full-fledged application, running all processes in a secure environment.
Productivity and Reputation Acceleration
You can set a clear path of tasks to complete and assign them accordingly among the team members. It would help you efficiently maintain collaboration and push secure code in the pipeline.
Additionally, it will release the software and updates at a faster speed. Besides it, when you develop secure software, end-users prefer it over any other application, leading to a boost in your reputation and revenue.
The Effort, Cost, and Time Savings
Once you start focusing on security from the very initial phase, it would save you a lot of money, cost, and effort afterward. With a checklist, you will have the assurance that all security systems are working fine and there’s a very low probability of getting breached. Moreover, it will provide you with plenty of time in creating new features and pushing them.
Top Tasks To Include In Your Checklist For High-End Software Security
If you want your software to be highly-secure and capable of preventing new-age cyber-attacks, then you must check off the following tasks:
Use Multiple Testing Techniques
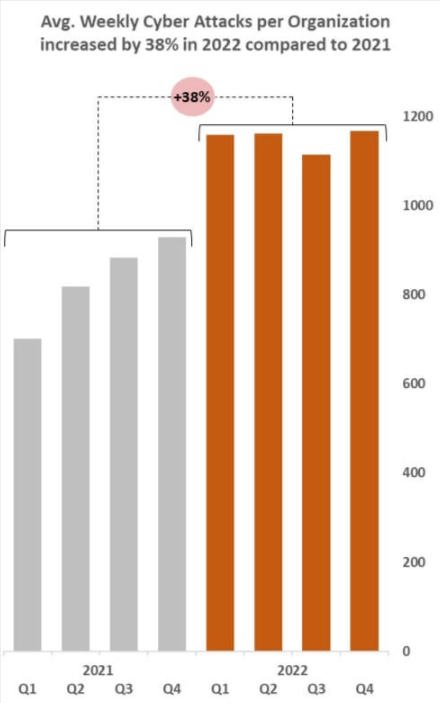
According to Check Point, a 38% rise in cyber-attacks gets analyzed in 2022. And most of it was due to a lack of testing and patching of potential loopholes. But, you can prevent them by using multiple software testing and review approaches.
Black Box, White Box, and Grey Box testing must be on your list to test overall software functionality from an end-user’s perspective. It will provide you an insight into attacks, which can get performed from the interface, such as SQL injection. Moreover, you must consider:
Fuzzing Testing
It will help you identify, whether the software is validating data properly or not. You can input malicious statements, SQL, XML, and HTML injection statements to verify the working of the validation mechanism.
Static Code Review
By thoroughly reading and reviewing the code, you can identify comments having confidential information, reused code blocks, and excessive code. As a result, you can remove additional code and remove sensitive details from comments, leading to reduce the attack surface.
Dynamic Code Review
To find more vulnerable code blocks, you can use automated tools such as Crucible, Visual Expert, GitHub, and CodeScene. The tools also provide suggestions to streamline the code and make it secure.
Recommended: Software Testing Strategies and Approaches for Successful Development
Configure Data Security Mechanisms
Whether the app is transmitting data or it’s at rest in the database, securing it is always a concern. You must focus on protecting data in every state, as its breach can lead to enormous monetary and reputation loss.
Attacks, such as man-in-the-middle, SQL injection, and directory traversal are the most common software threats. To prevent them, you can:
Configure an SSL Certificate
With an SSL certificate, you can create an encrypted data transmission channel between the browser and the web server. It will help you maintain the data integrity and prevent a man-in-the-middle attack. In addition, HTTPS protocol will get configured and all your users will understand that your domain is secured.
Hash the Passwords
Passwords are highly sensitive and for protecting them, you must use the Hashing mechanism. It would help you retain integrity, even if an attacker successfully breaches. Converting the hash value to the original format is nearly impossible. Therefore, hashing makes the password more secure.
Recommended: How to Hash a File to Improve Software Security?
Digitally Sign the Software
As per Verizon reports, 13% of overall cyber-attacks are due to malware, which an attacker embeds in software and then distributes it. And the primary root cause for it is when a malicious actor can read the code and modify it.
To prevent it, you must include the usage of a Code Signing Certificate in your checklist. It will help you convert readable code into scramble content, preventing hackers from understanding and modifying the programs.
Moreover, a Code Signing Certificate utilizes encryption and hashing algorithms, making it highly complex to crack software.
Additionally, when you use a Software Publisher Certificate, it embeds a digital signature with the application. It helps to remove Unknown Publisher Warnings and boost user confidence in the brand.
Whether you are an organization, that develops/publishes software or an individual developer, Code Signing Certificate is a must. It’s available at three validation levels:
- Individual Validation Code Signing Certificate (For independent developers)
- Organizational Validation Code Signing Certificate (For organizations)
- Extended Validation Code Signing Certificate (For organizations with three years of operability and additional security requirements)
Implementation of Least Privilege and Authentication
Whether you are building a website, web app, mobile app, or desktop software, keep the least privilege always a top priority. Always remember to provide only relevant access to resources according to the user’s profile and need.
Otherwise, a hacker can seamlessly take control of administrative controls and modify the app’s functioning.
To strengthen it, configure an advanced authentication system, preventing attackers at the beginning only. You must consider MFA (Multi-factor authentication) to verify a person’s identity. Further, OTP-based or email verification is a top method to configure for enabling it.
Moreover, for an organizational network, you can install digital certificates on host machines, which will get verified each time the server when an employee tries to log in.
Scan Logs, Validate Input, and Release Frequent Updates
The lack of an input validation system is one of the most severe risks, which can highly impact your software. Even, according to National Vulnerability Database, its severity is high and gets considered a critical loophole.
If your software doesn’t validate the input, attackers can effortlessly perform remote code execution on it. As a result, your app can even crash due to immense resource utilization.
Therefore, you must always put the configuration of input validation in your checklist.
Furthermore, constantly store the logs and analyze the average app behavior. It will help you discover abnormal activities happening using the software or between components. In addition, whenever an update is available for a framework, development technology, and OWASP and NIST database, push that update to the software.
However, you must test the update in a quarantined environment and then only provide it to end-users.
Wrapping Up
A developer’s checklist is necessary, as it helps to efficiently focus on the security of each component and data. It streamlines the overall development process and aids in managing upcoming tasks.
For high-end software security, a developer must have to enable encryption, digital signing of software, configure input validation, and use multiple testing techniques to identify vulnerabilities in the list.
Once you start preferring all the mentioned tasks, software security gets strengthened, maintaining data integrity, confidentiality, and availability.

