Must To Know Secure Java Development Practices

Java is a top-notch software development technology, that gets highly used for curating desktop, mobile, and web-based applications. According to enlyft, 455,000+ companies are using applications based on java.
But, with the introduction of newer technologies, hackers have become more competent in breaching and java apps are one of their primary targets. And the main reason behind it is the occurrence of loopholes in it, including the Spring4Shell/Springshell vulnerability. In addition, more than 25 new java vulnerabilities are added to the CVE database.
With such an increasing vulnerability rate, developers like you need to follow the best practices. It will help you utilize cutting-edge Java technology to build secure applications, and fulfill client requirements.
Top Development Practices to Build a Secure Java-based Software
To curate a secure environment for a java application to run its processes, you must consider the following best practices.
Avoid Implementing Serialization
Industry veterans, working as Java developers always suggest avoiding using serialization in applications. However, serialization helps in caching, sharing byte streams, configuring multi-tenant communication, and persistence.
But, there are also numerous vulnerabilities associated with it, such as an attacker can benefit from object deserialization to embed malicious code.
In addition, serialization also uses extensive processor resources, which can slow down the app’s performance and stability.
Furthermore, you must consider the following practices instead of serialization:
- Prefer JSON for data transfer
- Utilize non-native data formats, such as XML
- Deploy RASP (Runtime Application Self-Protection) tools on application servers
- Prevent classes to get serialized by using the java.io.ObjectInputStream
Don’t Reveal the Exact Error
Revealing the exact error to end-users is a primary way of providing confidential information to an attacker. When you display the exact code, hackers use it for gathering information about code structure, used libraries, databases, classes, and objects in Java software.
You must always keep your error messages generic, rather than entirely technical. For instance, if a user enters the wrong password, only show a message such as “Invalid Login”, rather than displaying the code behind password verification.
While developing the Java application, always create test cases for confirming that the error code is not getting displayed. And also try to keep a log of every activity using tools like Kibana and Looker. Additionally, you can use a log server, analyzing activities based on user behavior to detect malicious actors.
Encrypt and Hash Sensitive Information
Primarily data has three states in Java applications, at rest, in processing, and in transmission. And you must focus on the security of all three. The best way to do so is by using encryption and hashing algorithms.
For data at rest, you must use encryption and for passwords, hashing is the best technology. It will secure user passwords, even if an attacker successfully performs an SQL injection attack.
Further, you must use an SSL certificate to transfer every data bit in an encrypted environment. If you use a datagram for data transfer, then you can prefer configuring a DTLS (Data Transport Layer Security) for secure communication over the network.
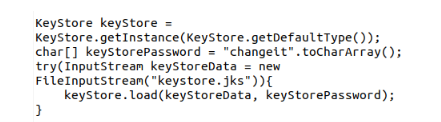
Below is a code example, which you can refer to for enabling SSL.
Write Clean and Short Code
Clean and short code is the fundamental pillar of every secure Java software. Due to it, additional code gets removed, which directly impacts eliminating additional vulnerabilities. The shorter the code and naming convention, the less the possibility of an attacker exploiting the application.
In addition, you must prevent reusing the code from third-party repositories, such as Stack Overflow and GitHub. Hackers are also present on these sites and they publish their malicious code so that developers copy that and put it in their programs. Hence, you must avoid code reusing.
Moreover, make perfect use of access modifiers by configuring different access levels to methods and classes. And try to provide only limited scope to components for interacting with each other and outside the network.
Prefer Only Tested and Known Libraries
To build a secure Java application, use only tested libraries to prevent attackers from exploiting your software. Before you use any library, research through the CVE database to discover associated vulnerabilities and patches to it. And if the patch is not available, avoid using that particular library and find an alternative to it.
Whether it’s parsing, general-purpose, or logging library, always use it after confirming its legitimacy and available vulnerabilities. Also, have a constant look at the release of their new versions to update your application accordingly.
Use Java Code Signing Certificate
To make the application secure in the production environment, it always recommends to use Java Code Signing Certificate. Similar to data encryption and hashing, such digital certificate aids in encrypting the source code.
It converts the code into a hash digest and then encrypts that digest. And the person with a private key only avails the leverage to read or convert back the code to its original format.
Recommended: What is Java Code Signing Certificate?
As a result, attackers get disabled from reading and modifying the code.
Furthermore, it also embeds your digital signature, which helps the system identify you as an authorized publisher. Due to it, your users don’t face Unknown Publisher Warning, which boosts the user’s confidence and brand reputation.
Parameterize Input and Queries
According to Statista, SQL injection has led the charts of the most critical vulnerability in 2022. And the most common factor behind its successful execution is the lack of parameterization. To make a java application secure, you must configure parameters in the code to run only specific queries.
public void selectExample(String parameter) throws SQLException {
Connection connection = DriverManager.getConnection(DB_URL, USER, PASS);
String query = "SELECT * FROM USERS WHERE lastname = " + parameter;
Statement statement = connection.createStatement();
ResultSet result = statement.executeQuery(query);
printResult(result);
}By using the code block as above, you can create a difference between parameter data and a query. As a result, the attackers will get disabled from injecting malicious queries and breaching databases. Hence, your data at rest would become more secure.
Configure Authentication and Access Controls
Authentication is a crucial security control, that every java application must have. It will help you validate the user identity and allow only authorized people to access resources. For strong and efficient authentication, you can prefer tools such as OpenID, Auth 2.0, and similar. Although, you must verify their legitimacy before implementation.
Furthermore, always consider configuring multi-factor authentication control. It will help you prevent hackers from hijacking user accounts through usernames and passwords.
Additionally, to strengthen identity verification, you can use cloud-based services, such as Firebase authentication. With it, the responsibility of managing and securing data will also get eliminated. But, prefer it only if you have a flexible budget, as sometimes cloud services can be expensive.
Enable Java Security Manager
You won’t find Java Security Manager enabled by default, as it restricts a process from accessing the network, disk, processor, and other resources. But, according to security experts, it’s a good practice to use it.
Otherwise, someone exploiting a single java app component could switch to another by jumping between processes. For instance, if you don’t enable it, a hacker can even modify the bytecode of a running process.
Further, when you enable java security manager, you need to define policies for each process execution with its access level. As a result, each operation avails a limited exposure, which in return limits the attackers. Therefore, you must consider using the built-in security manager for a solid security foundation.
Concluding Up
Java is a top choice for companies to develop a scalable business solution. But, every year more vulnerabilities get discovered in Java, leading to exploits and breaches. However, to not let malicious actors perform such activities on Java-based software, developers must consider adapting the mentioned practices.
Once the programmers start following such practices, the java app will become more secure, stable, and high-performing. Moreover, with the code practices, a developer must always sign the software using Java Code Signing Certificate to enhance its reputation across digital platforms.
Want to Secure your JAVA Application?
Digitally Sign and Verify your Java based Application or Code with Cheap Java Code Signing Certificate Just at $199.99/yr!
