Proven Ways to Boost Your Web Application Security in 2024

Several web applications have been booming in recent years, as every organization prefers it for business due to its easy maintenance and advanced features. And it’s evident that when a firm uses any application, it processes confidential data.
Whenever data comes into play, cyber-attacks and security aspects accompany it. And same is the case with web applications.
Like other software, application security is also crucial for web applications. You must consider the application security checklist to protect users and information from threat actors. It will help you solidify the app foundation and maintain a secure ecosystem.
So, let’s get started to protect any web application in 2024.
The Need To Focus On Web Application Security
App Development and Security are the fundamentals of every development project that every team member should focus on. To protect data and applications from hackers, it’s important to consider web application security from the initial stage, i.e., from the requirement gathering and planning phase.
Most of the development teams primarily focus on building the application but lack while testing and configuring the security. And that’s how the risk of getting exploited by a hacker increases.
In addition, as per industry professionals, every web application consists of a minimum of 2 high-level, 5 medium-level, and 8 low-level vulnerabilities if the development team doesn’t focus on its security.
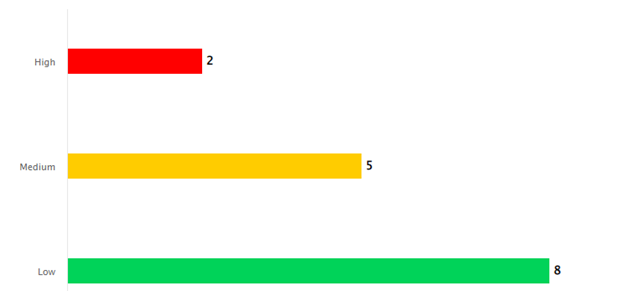
Even a single vulnerability can lead organizations to face heavy reputation, monetary, and customer loss. Just think, what can happen if all such vulnerabilities are present, then how devastating it can be. Hence, it’s essential to work on app development and security simultaneously to prevent hackers from providing any harm.
Application Security Checklist To Consider For Solidifying Web App Security
To ensure all end-users that your web application maintains data integrity, confidentiality, and availability, you should implement security practices, tips, and approaches.
Perform All The Necessary Testing
Security testing is a must for every web application. Whenever you develop any web-based software, constantly test it with different techniques using both automated and manual tools. It will help you gain knowledge of every component’s functioning, loopholes, and security levels.
In addition, you must consider the following testing approaches to solidify web-app security.
DAST
Performing Dynamic Application Security Testing must be on every tester’s checklist. While creating the project schedule or Gantt chart, you must list the DAST testing.
Under this testing, the application gets tested from the perspective of an average hacker. To find and exploit vulnerabilities, the tester executes multiple cyber-attacks, such as SQL injection and brute-force attacks.
The primary aim of DAST testing is to find methods a malicious actor can perform from the interface to impersonate the software. Moreover, the information about used technologies and source code isn’t get disclosed to the tester for better results.
SAST
Static Application Security Testing gets performed at the developer’s end or during the development phase. Under this testing, development teams verify the security and functionality of every code block before or after its integration.
It’s the choice of developers how they want to test their code, but they have to make sure that the final source code is vulnerability free.
As compared to DAST, SAST is entirely different. In SAST, developers have access to code, frameworks, and all other backend and frontend technologies. As a result, vulnerabilities get eliminated along with development and reduce the efforts for testers, making the app more secure in a short period.
Penetration Testing
Under penetration testing, you must research and identify the cyber-attacks that an attacker can perform on your web application. Once you start simulating, you will gain knowledge about the software’s strength of authentication, authorization, and access controls.
Besides it, you should also target the servers, databases, and cloud infrastructures integrated with the app for better results.
It will help you discover all the vulnerabilities which get missed by the development team while doing SAST testing. Always remember that you should prepare a report of penetration testing so that you can share it with developers to embed appropriate patches.
RASP
Runtime Application Self-Protection is the testing approach in which automated monitoring tools get used. Testers run the applications along with RASP-oriented tools in the background to assess performance, reliability, exception handling, and data flow security.
Besides testing, you can also run such tools in the background of the final release, as they contain defending systems. It will alert about threats and differentiate between legitimate and illegitimate requests. Some of the popular RASP tools you can use include:
- Fortify
- Screen
- OpenRASP
- Jscrambler
- Imperva
- Hdiv
Additionally, you should rely on something other than RASP tools, as sometimes it can slow down the performance. So, you should first test the tool and software compatibility before the final release.
Digitally Sign App with a Code Signing Certificate
With the help of a Code Signing Certificate from a reputed CA, such as Certera, Comodo, and Sectigo, you can protect the software integrity and enhance brand authenticity. Also, Code Signing certificates are made compulsory by various digital platforms to publish the web application.
When you utilize such digital certificates, it creates a hash value of the source code and then encrypts the hash digest, preventing attackers from making any modifications. Further, it adds your digital signature and embeds it with software.
And with its PKI mechanism, it helps the systems to verify the legitimacy of your software and remove the Unknown Publisher Warning. Whether you are an independent software developer/publisher or some enterprise, Code Signing Certificate is available.
Encrypt Communication with an SSL Certificate
You must install an SSL certificate for applications and accessing browsers to provide relevant resources to the end-users. With the aid of an SSL Certificate, data transmissions will get encrypted with the 256-bit encryption algorithm.
In addition, it will help you integrate an additional security layer, preventing hackers from breaching the data in transmission.
Moreover, an SSL certificate will ensure that only legitimate systems participate in the communication. And it will also help you align the web app with PCI-DSS, HIPPA, and HITECH standards, guaranteeing secure financial, medical, and other business-sensitive data transactions.
Configure Input Sanitization
Whether it’s about web apps or any other software security, input sanitization must be on your list. With the advancement in SQL injection, code injection, and cross-site scripting attacks, input sanitization has become a necessary security mechanism.
It assesses the data getting entered by the end user and verifies its legitimacy before processing. It leads to preventing the application from executing a malicious query and triggering malfunctioning.
In addition, you must create your own custom rules for input sanitization and define a proper format for every user group. As a result, the application will have the clarity to block malicious input from reaching out to the processor and getting executed.
Implement New-Age Security Policies
Security policies aid in strengthening the overall application architecture and also helps the developers in complying with industry standards. With the use of policies, you can define how data will get retrieved, processed, and stored and what requirements the user has to fulfill before accessing the web app.
Primarily, you need to define two types of policies; business-defined and governing body-defined policies. Under the business defined, you must look into the requirements and generate passwords, resource utilization, user login, or similar protocols accordingly. And under governing body, you need to align with NIST, ISO, PCI-DSS, and other such policies.
Make Use of Authentication, Authorization, and Access Control
The AAA controls in cyber-security are crucial for every web application. It assures that only legitimate users are accessing the software and that the right amount of resources gets used.
The authentication control will analyze the identity of the person trying to access the application. Verifying the password, token, private key, OTP, and verification link are common mechanisms you can configure to authenticate the user.
Further, the authorization will work according to the user groups. For instance, administrative controls will get denied if an average end-user utilizes the app.
And last but not least, access control. It will help you define blacklists and whitelists to block threat actors and from transmitting sensitive to a third-party server. You should define your policies according to the AAA controls to boost overall app security.
Constantly Backup and Scan
Backing up data is a well-proved approach to maintaining data availability. When configuring the web-app server, always add an extra server or storage space to back up the data constantly. But, ensure that the backup server is not a part of a public-facing network or IP (Internet Protocol).
For better security, you can install the backup system in a DMZ (Demilitarized Zone) or at a separate cloud infrastructure. It will prevent hackers from accessing backup data, even if they enter your organizational network.
Once you start doing data backup, you will get the assurance of always having the required data in place to continue business operations, even if any breach happens. Moreover, you should frequently scan the data offline to discover suspicious activities and loopholes and to verify that every component is working appropriately.
Conduct Bug Bounty Programs
You will find very few organizations participating in bug bounty programs and considering it as a relevant security approach. However, it can be a little costly, but as a result, you can learn about various hidden or missed vulnerabilities in your web app.
You can publish your application on platforms such as Bugcrowd and HackerOne. Then, numerous penetration testers and ethical hackers will try to exploit the software. And whenever they find a bug, you will get the report and procedure to simulate the attack. In return, you can provide a monetary reward, appreciation certificate, or company swag to the person.
Therefore, through bug bounty, you can identify and patch loopholes promptly. And you can also connect with multiple security enthusiasts, testers, and hackers.
Utilize WAF
A web Application Firewall (WAF) is an advanced security mechanism that vets every incoming and outgoing request. You can define custom firewall policies for filtration, which will seamlessly allow and disallow user requests accordingly.
However, WAF can be resource intensive and even downgrade the application performance. So, you must check its compatibility and functionality before releasing it with the final version.
In addition, you can enable IPS (Intrusion Prevention System) and IDS (Intrusion Detection System) systems along with a firewall to alert about potential threats or handle them automatically.
Additionally, web apps are mostly on the verge of getting attacked with DDoS, but with a firewall, you can prevent or completely mitigate it.
Encrypt and Hash Data
Always remember the encryption and hashing mechanism whenever you build any web application. Both will help you solidify security for data in rest and transmission. And it will also strengthen the authentication procedure and prevent hackers from reading information even after a breach.
You have to configure the hashing on stored passwords. When the user enters a password, the application will convert it to a hash value to compare it with the stored hash digest.
If the hash values get matched, the user will log in, but otherwise, it will not. Similarly, you can use encryption to convert information into ciphertext and allow only authorized parties to read it using public and private key pairs.
Constantly Check for Human Error and Misconfigurations
Misconfigurations due to human errors can be a potential vulnerability for cyber attackers entering your network and exploiting web applications. You must focus on the following aspects to remove loopholes.
- Password protects all the systems and digital certificates.
- Check for open ports and close them as soon as possible.
- Test the functionality of the firewall and all other security systems with automated and manual tools.
- Use only the latest version of development frameworks and libraries.
- Scan and patch every new version and code block before integrating it into the final release.
- Avoid utilizing APIs and plugins from unauthorized identities.
Additional Practices for Container Management
Nowadays, most web applications are built and run on containers, which can be an additional vulnerability. Hence, you must also focus on securing the container ecosystem to protect the web application from malicious actors.
To improve container security, you must scan the image file for viruses and utilize hashing to store the account credentials to access it. In addition, root access to the container must never get granted by default to any user.
You can also configure the containers in different subnets for better protection. Once you follow such practices, your web application will get secured.
Why Developers/Publishers Prefer EV Code Signing Certificate
Extended Validation Code Signing Certificate is a worthy digital certificate that provides instant reputation to software and business. Once the developer/publisher passes the EV validation process, every digital platform treats it as authentic.
In addition, any software coming from the such publisher doesn’t trigger Defender SmartScreen and Unknown Publisher Warning.
In addition, the EV Code Signing Certificate also provides the following:
- Unlimited signing for any executable file format
- Timestamping to make software valid for a lifetime
- Private Key in an external FIPS-140 aligning USB
- 100% assurance to eliminate download and installation warnings
- Ensure source code integrity and confidentiality
A Reliable Provider To Avail Cheap Code Signing Certificate
While looking to Purchase Code Signing Certificate, you must always consider a recognized certificate provider, such as SignMyCode. The certificates offered by SignMyCode are one of the cheapest in the digital certificate industry. Besides it, you also get the leverage of:
- 24/7/365 available technical and customer support
- Freely accessible tools and resources to smoothly execute certificate operations
- All types of Code Signing Certificates – IV, OV, and EV
- Certificates directly from CAs, like Comodo, Certera, and Sectigo
- 30-day money-back guarantee
Wrapping Up
Web applications are becoming the top-most choice for organizations to start and enhance their business digitally. But with the increasing cyber-attacks, it is essential to focus more on its security factor to protect personal, financial, and other sensitive information.
According to experts, Code Signing Certificate, SSL Certificate, Authentication, Firewall, Data Backup, and Input Sanitization must get implemented to align the app with new-age standards.
In addition, you must also define policies and perform appropriate testing before releasing the final application and any of its updates. As a result, your web app will get vulnerability-free, preventing hackers from performing exploitation.

