How to Configure or Setup Azure Key Vault to Store Code Signing Certificates?
In this post, we’ll look at how to set up and use Azure Key Vault to store code signing certificates securely. The use of Azure Key Vault provides a dependable option for keeping these certificates safe in a secure setting.
What is a Code Signing Certificate?
Let’s start by learning more about what a code signing certificate includes. Software developers use code signing certificates as an essential tool to sign their programs, drivers, and other digital content. Its main objective is to give end users the means to check the validity and integrity of the code they receive.
Developers use code signing certificates to prevent unauthorized third parties from altering or tampering with their code. These certificates include crucial details like the developer’s signature, the name of the business, and if desired, a timestamp.
Azure Key Vault Code Signing essentially performs the same role as website certificates, which authenticate websites when viewed through HTTPS.
The customers are reassured that the code does actually come from the expected source, thanks to their ability to build trust and ensure the provenance of packages, executables, and other components.
How to Get a Code Signing Certificate?
An Azure code signing certificate may be purchased from a number of reliable sources. You can get your own code signing certificate from DigiCert, one of best providers.
If you don’t have a code signing certificate, respected businesses like DigiCert, Globalsign, and others offer alternatives. Remembering that these certifications may be pricey for smaller development teams is vital.
Steps for Setting up your Azure Key Vault
Let’s now see how Azure Key Vault is set up and configured to store code signing certificates. You can guarantee the highest level of security and protection for your priceless certificates by employing Azure Key Vault.
With strong access control and auditing features, Azure Key Vault offers a centralized, secure repository for storing cryptographic keys, secrets, and certificates.
You’ll need an Azure membership to get started. You may create an account on the Azure website if you don’t already have one.
Following these steps will allow you to set up and customize Azure Key Vault for code signing certificates after you have your subscription:
Step 1: Apply your Azure account credentials to log in to the Azure portal at portal.azure.com.
Step 2: You may add a new resource by selecting the “Create a resource” button.
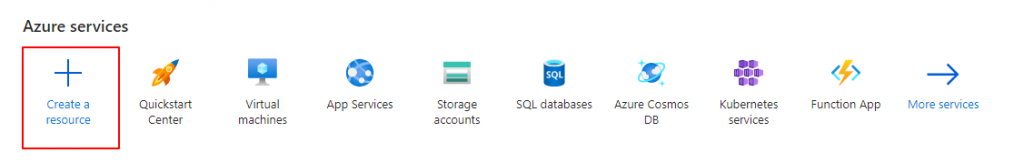
Step 3: Type “Key Vault” into the search field, then click “Key Vault” from the list of alternatives.

Step 4: The Key Vault creation procedure may be started by clicking the “Create” button.
Step 5: Give your Key Vault a distinctive name and choose your preferred area, resource group, and subscription.
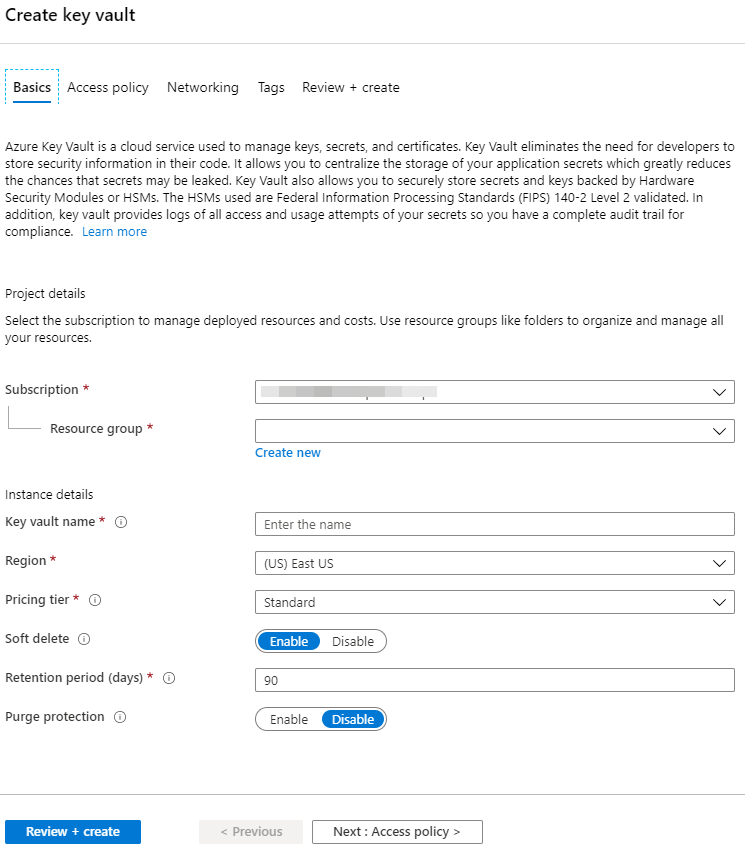
Step 6: Activate the “Soft delete” function to keep deleted keys, secrets, and certificates around in case of unintentional deletions for a predetermined amount of time.
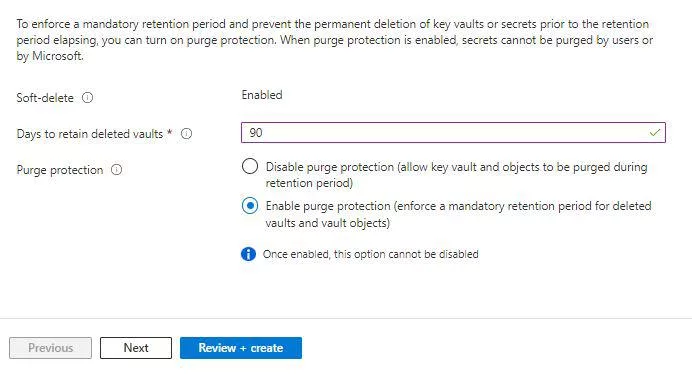
Step 8: Create your Key Vault’s access policies. This involves giving the people or programs interacting with the vault the proper permissions.
Step 9: Once the setting is finished, select “Review + Create” and “Create” to begin the Key Vault creation.
‘Partnered CA Providers’ Method for Importing Certificates:
Multiple methods are available to upload a certificate to Azure Key Vault. One of the options is using the ‘Partnered CA Providers’ method, which offers a straightforward approach.
However, if you prefer a different approach, you can choose to import your certificate into Azure Key Vault.
To begin the process, you must first import the certificate into the certificate store on your local computer. Once the certificate is successfully imported, you can export it to upload or import it into Azure Key Vault.
If you have obtained your certificate from DigiCert, you can utilize their DigiCert Certificate Utility for this process.
Recommended: How to Instantly Sign Your Software Using the DigiCert Utility Tool?
It’s important to note that the instructions provided here assume that you possess a ‘pfx’ file containing the certificate’s private secret, which is commonly referred to as the password for the certificate.
Note: Due to new CA/B, All code signing certificates now stored on FIPS 140-2 or Common Criteria EAL 4+ compliant Hardware Security Module (HSM) or Yubikey USB tokens. So, No PFX Cocept or Export Works!
By following these steps, you can securely transfer your certificate to Azure Key Vault, ensuring its availability for various operations and functionalities within the Azure environment.
Follow this blog post to generate and import the certificate into the Microsoft Azure Key Vault!
Congratulations! Now that Azure Key Vault is set up and ready to store your code signing certificates, you can easily use it.
Your certificates are now securely kept in a location that is both extremely secure and easily accessible. This guarantees their honesty.
A Future Note
So, to sum up, we have successfully executed the guide to set up and configure Azure Key Vault to store code signing certificates.
Developers can guarantee their certificates’ highest level of security and integrity by utilizing Azure Key Vault, shielding them from unauthorized access and manipulation.
The next step would be to provide the right apps, or users access to the certificate after storing the code signing certificate in the Key Vault. We will discuss the procedure for gaining access later because this subject is too broad for this one.
The procedures presented in this article can help developers build a solid infrastructure for keeping and securely storing their Azure code signing certificates.
Guaranteeing to end users that the code they receive is original and unaltered improves the software’s dependability.

