Most Common Malware and Software Security Threats

A List of Common Types of Malware Attacks
Technologies are evolving, and so are viruses and malware; with each passing second, they are becoming more advanced and threatening. Thus, it is quite tough to keep all confidential data protected or safeguard software security.
Until and unless you take proper precautions (which people usually don’t), you risk falling prey to advanced software malware attacks and virus threats. Now, isn’t that scary?
Today, there is no dearth of ways of stealing data, and cybercriminals make the best use of malware and viruses to launch an attack. It is because cyberattacks, just like technology, have changed in terms of sophistication and complexity.
Gone are those days when you could simply rely on your system’s inbuilt antivirus software and stay assured. Today, you need the best endpoint software security to stay away from attacks.
To help you stay alert and protected, it is important to know about the most common types of malware attacks. But, before we start discussing that, let us first understand what software security is and why it is important in today’s time.
What does Software Security Mean?
If you are a software company, you would obviously want your software security protocols to give others a run for their money. However, in the present IT ecosystem, with the increased development of software and the frequency of cyberattacks, it can be quite challenging to keep up with the security of software. So, how will you achieve comprehensive security? The answer is software security.
Software security can be defined as the implementation of a mechanism in the working of the security to make it active or unsusceptible to attacks. It means that before an organisation sells it, the software has to face a software security test to determine its ability to stand or fight malicious attacks. This technology’s core concept is to build safe software from the get-go without having to incorporate extra security components for additional security purposes.
It has proven to be extremely crucial as malware attacks cause extreme damage to any software and result in compromised availability, integrity, and authentication. Therefore, this is something programmers should consider in the programming stage to stop the security threat even before it starts.
Primarily, IT security comes in four main types:
- Network Security: It means establishing security between different devices situated on the same network. Here, the significance of hardware and software security is the same. While establishing network security, companies ensure that no one can maliciously use the network.
- End-point Security: This type of security focuses solely on the used devices. So, it means securing laptops, phones, computers, tablets, etc. (both in terms of software and hardware), thus preventing any kind of unnecessary information from slipping. The process employs techniques such as user control, encryption, etc.
- Internet Security: Popularly called as cybersecurity, it deals with the transmission and application of data. Cybersecurity attacks take place when data is intercepted. Thus, different layers of authentication and encryption and authentication are used to prevent attacks.
- Cloud Security: Cloud security means adopting different types of security measures for the security of cloud-based infrastructure, apps, and information. It ensures user and device validation, data and resource access control, and data privacy protection.
These are the major types of IT security and how companies achieve them. Another important thing to know is a threat to the whole digital world- software malware!
What is Software Malware?

The digital space, just like the real world, is filled with marvels and perils. For every good thing that comes in, there is another dubious threat sneaking in the background, waiting to prey on its victim. Sounds a tad bit dramatic? But, it is the reality. Software malware are those threats that prey on people’s confidential data.
Software Malware can be defined as any program specifically designed to result in an undesirable or dangerous action on a system. Cybercriminals use them for extracting confidential information, extorting ransom, or just causing maximum destruction possible to an affected system.
Today, most cyber attackers are using the Internet to spread malware. As the threat of malware is not just limited to a system, any device connecting to the Internet can get infected. It can be placing infected file attachments in a spam email or distributing malware on a compromised website.
There are multiple types of malware available at the convenience of an attacker. Below, we will discuss the most common types of malware attacks.
What are The Most Common Types of Malware Attacks?
Let’s just face the truth here. No system is completely vulnerable-free or hacking-resistant. When a threat has sufficient manpower, time, and resources for launching an attack, there is a good chance for it to creep in. The stats speak volumes about all adversities spread by malicious attacks.
While there are many different types of malware attacks, we have listed down the ones that you are most likely to encounter:
1. Ransomware
In ransomware attacks, the software uses encryption technology to remove access of the target to its confidential data until it pays a particular amount of ransom. Usually, the victim party is rendered completely or partially unable to get hold of the data. However, even after the payment of ransom, there is, as such, no guarantee that it will ensure a decryption key or the key provided will work correctly.
According to statistics, the estimated number of ransomware attacks is around 204.24 million. In 2019, the city of Baltimore witnessed ransomware called RobbinHood, which halted all types of city activities for weeks. It included property transfers, tax collection, and government email resulting in several losses.
2. Adware
Adware is software that can monitor all the surfing activities of a user so that it can serve them with ads. The compromise of users’ privacy is the most dangerous aspect of this malware attack. Typically, the software captures all the data and collates it with data collected openly or secretly about the activity of a person in other places of the Internet and creates their portfolio. The portfolio usually includes who they are friends with, where they have traveled, who they talk to, what they have purchased, and other vital information. The attackers can sell or share this information with advertisers without the users’ consent.
In 2017, adware called Fireball was responsible for corrupting as many as 250 million computers and devices. It had hacked browsers and changed its default search engines and tracked what users did on the Internet. The worst part about this malware was that it had the power to remotely run code and download corrupt files.
It can happen to anyone, so Microsoft Windows systems have introduced a free community tool called CrowdInspect. It alerts the users about the presence of potential malware on their system.
3. Trojan
A Trojan is a type of malware or software that disguises itself as a legitimate program but, once downloaded by users, will take control of the system for malicious purposes. It is usually found hidden in software patches, applications, or games. One might also find it in phishing emails with an embedded attachment.
Since 2014, a Trojan malware called Emotet has been around. It is a complex banking Trojan that is quite challenging to fight due to its power of signature-based detection, which is highly persistent and consists of spreader modules that help in its propagation. It is so powerful that even the US Department of Homeland Security is quite alert of it.
4. Bots/Botnets
A bot happens to be a software application that can perform automated activities upon command. Though its application is quite legitimate, like indexing search engines, when it falls into the wrong hands, they become a self-propagating software that can access a central server and get all confidential information.
A computer infected with this attack can spread it to other devices, making a botnet. Usually, hackers control a network of bot-compromised systems to launch massive attacks. Oftentimes, these attacks take place without the device owner knowing all this. In 2018, a similar bot attack that goes by the name of distributed denial of service attack(DDoS) blew away the Internet connectivity for most parts of the Eastern U.S.
5. Rootkits
Software that allows malicious actors to get control of a computer remotely is called a rootkit. Usually, the rootkit has complete administrative liberties of the system. An attacker can inject this malware into hypervisors, applications, firmware, or kernels which is then propagated with the help of phishing, compromised shared drives, malicious email attachments, and malicious downloads.
Zacinlo is a type of rootkit malware that can infect systems when the system owners download a fake VPN software or application. After installation, the malware runs a security sweep for competing malware, attempts to get rid of it, opens invisible browsers and engages with Internet content just like any regular person would. It does so by scrolling, highlighting and clicking on online content.
6. Spyware
Spyware is another malware software that extracts data about users’ activities without their consent or knowledge. It can include their payment information, passwords and unstructured messages, or any credential. The application of this software is not just limited to desktop browsers, but it can also function in critical mobile phones or applications. As they steal all types of data, you might think the stealing of your not-so-important data is something you can bear, but you’re wrong. Even if the stolen data is not as important, the impact of this software often cripples an organization and degrades its productivity.
A fine example of spyware is DarkHotel. It was used to target government leaders and business tycoons who used hotel Wi-Fi. It employed multiple malware to access the system of people in powerful positions in society. As soon as the attackers got access, they installed keyloggers to collect credentials and other sensitive data.
There you have it! All of these were the most common types of malware attacks. Wondering how to fight all these types of malicious attacks? Code signing certificate is one way to go about combating different types of cyber security threats. Let us briefly talk about what it is:
What is a Code Signing Certificate?
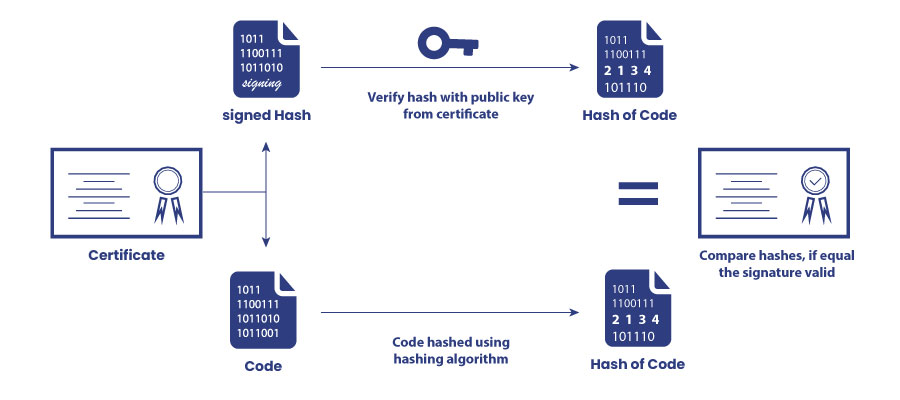
In a world that is operated fully by software, trust is everything. Given the news of cyberattacks every now and then, how do you know which one to trust and which one to not? We have a code signing certificate for that.
A code signing certificate is a type of digital certificate that is used for authenticating a business or organization. Typically, it is issued by a trusted Certificate Authority for the specific purpose of developers signing code. With a valid code signing certificate, a developer can sign any code that they are sending live for production.
Usually, the signature contains all the data of the company, like its name, location, kind of work it does and much more. Typically developers use code signing to prove the authenticity of a piece of software and assure that it is from a trusted or legitimate source and has not been tampered with by any third party.
The code signing is dependent on cryptography, more specifically, what is called a code signing certificate.
Conclusion
Software security can severely damage a company when you have it in place without any plan. Yes, that’s the bitter truth! But, as we already discussed, it begins with developers ensuring that the software is made for attacks on anything that tries to hamper it. Though this process is not in the hands of the end-users, it should be an important part of determining which software to trust.
After selecting suitable software, it is time to implement the best practices of software security to keep all malicious activities at bay and keep data protected. To achieve this, businesses and organizations must opt for the best software security solutions.

