Microsoft SignTool: Signing Executable Files Through a Seamless Approach
Code Signing Certificate has become a prominent security solution for every software publisher and developer. And after purchasing it, there are still a lot of queries that arise before tamper-proofing the source code.
And then a big question also comes, How to sign executable files using Code Signing Certificate? The simple yet most accurate answer to it is Microsoft SignTool. Whether you have an IV, Standard, or EV Code Signing Certificate, you can use SignTool to unleash the potential of any digital certificate.
A lot of developers need help using SignTool. But, with this step-by-step guide, you will learn digital signing and timestamping of an executable file in just a few steps. Let’s get started.
What is Microsoft SignTool and its Usage
SignTool is a program available for the Microsoft Windows operating system. It’s a tool you can access through a command-line interface for signing and timestamping applications, software packages, and other executable files.
It is, by default, available in the Windows Software Development Kit. And you can effortlessly find it in the Bin folder inside the Windows SDK folder, stored in C:\ drive. However, if you are utilizing Visual Studio for code development. Then, you can access SignTool from within the app, as it comes in the Visual Studio installation package.
Steps to follow for Digitally Signing an Executable File with SignTool
Signing an executable file is a smooth five-step procedure. You can complete it within minutes by following the below instructions.
Step 1: Accessing the Command Prompt to run SignTool Commands
To utilize the SignTool, you must open the Command Prompt in Administrator mode. You must open the startup menu and search for Command Prompt or cmd. Further, you have to:
- Right-click on the Command Prompt icon.
- Select “Run as Administrator”
Once the system runs, you will get a dialog box to provide permission. After selecting the appropriate response, Command Prompt with administrator controls will get opened.
Step 2: Logging In as Administrator
Sometimes, you have to log in using default system credentials to access the administrator controls. And once the system verifies it, a new window will get displayed as below.
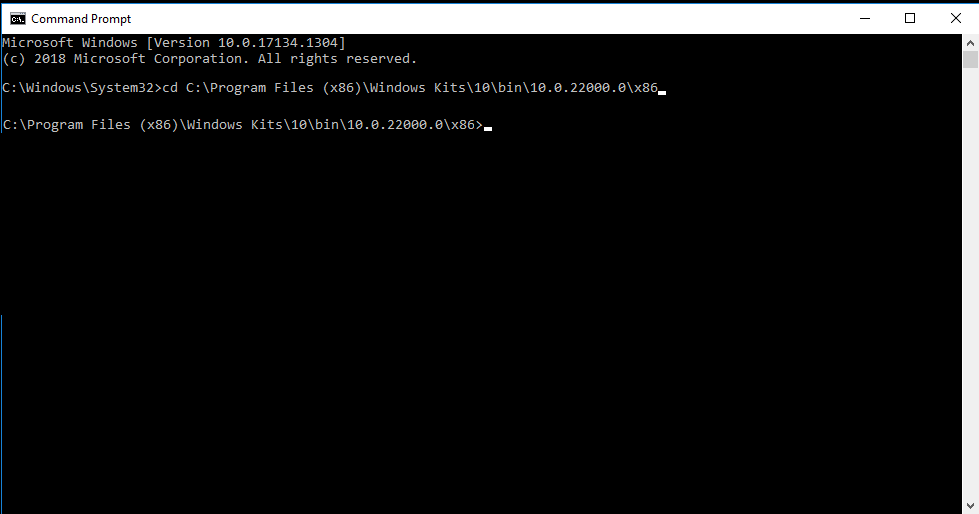
Step 3: Navigate to the SignTool directory.
To complete step 3, you must know the exact location of SignTool in your system. Primarily, it is available in the C drive by default. If you have saved it in a different file, you must use the path to that particular location in the command.
You have to run the following command:
cd C:\Program Files (x86)\Windows Kits\10\bin\10.0.22000.0\x86The ‘cd’ command gets used to change the current directory. It will help you to access and utilize files present inside the SignTool directory.
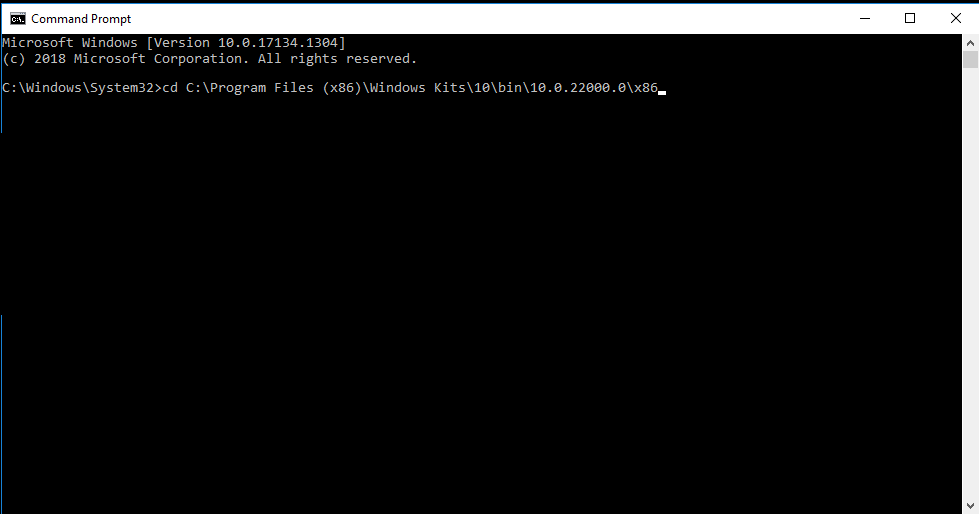
After writing the above command and hitting enter, you will see a command prompt similar to the one below. Now you are in the SignTool directory, enabling access and utilizing its resources.
Step 4: Signing the Executable File using IV, OV, and EV Code Signing Certificates
To sign the file, you must run the following command per your requirements.
To Timestamp and Digitally Sign an executable file simultaneously:
Signtool sign /f MyCodeCert.pfx /t http://timestamp.comodoca.com MyFile.exeFor timestamping purposes, you must write down the address to a timestamping server of your Certificate Authority. The above command illustrates the address to Comodo Timestamping Server. You can replace it with your CA’s address, and your software will get a timestamp and a digital sign.
Above all, commands are specific to Individual Code Signing Certificate and Organization Validation Code Signing Certificate.
To Digitally Sign the file using EV Code Signing Certificate, you have to run the following command:
Signtool sign /n "MyEVCertificate" MyFile.exeTo execute the command, you must first install the EV Code Signing Certificate and plug in the hardware token. The system will display an error if you cannot fulfill any of the requirements.
Recommended: Sign Executable Files Using EV Code Signing Certificate
In addition, you will see a confirmation message when your file gets digitally signed.
To Sign a complete Application Package:
Signtool sign /fd SHA256 /a /f signingCert.pfx /p password file path.appxTo secure an app package using a code signing certificate, you have to define the hashing algorithm, path to the file, and password in the command.
To Sign and Timestamp a complete Application Package:
Signtool sign /fd hashAlgorithm /a /f signingCert.pfx /p password /tr timestampServerUrl filepath.appxYou have to replace the hashAlgorithm with the SHA256 or any other algorithm you want to use. Also, you have to replace timestampServerUrl with the address of the timestamp server of the CA.
Step 5: Verifying the Code Signing
After running the appropriate command to sign the software, it is crucial to validate it. And for it, you have to run the below command:
signtool verify /pa /v “c:\filepath\example_software.exe”You have to define the path to the signed executable file to execute the command. And, if it gets signed, you will get an output.
Furthermore, let’s understand the different commands getting used for signing purposes:
| Command Option/Extension | Description |
| /f | The /f command option is getting used to define the file, storing the Code Signing Certificate. Its primary purpose is to aim toward the file with the .pfx extension. Such files are also known as files in the Personal Information Exchange Format. |
| /t | The main purpose of using the /t command option is to define the URL to the timestamp server of the CA. You have to write /t and then the server’s web address. It will help the system to fetch the required details and perform timestamping on the executable file. |
| /n | The /n option gets used to tell the system the name of the Code Signing Certificate file. You first write the /n and then the subject of the file containing the digital certificate. |
| /p | /p command option stands for password. When you utilize a .pfx file protected with a password, it is essential to use /p to write the password in the command. It enables the system to access the certificate and perform further functionalities to sign and timestamp the software. |
| /a | The function of /a command option is to analyze the currently available valid certificates and select the most appropriate one to digitally sign the specified executable file. It entirely depends upon whether the publishers want to utilize it or not. |
| /fd | Using /fd command option is necessary when defining a particular hash algorithm. It is mandatory to use in such cases for digitally signing the software and to maintain the integrity of the source code. |
| /pa | The /pa option is to set the Authenticode Verification Policy for validating the sign of the executable file. Furthermore, if you don’t utilize /pa in the command, the system uses the Driver Verification mechanism, which is inappropriate in such cases. |
| /v | The /v is for verifying the command status. It tells the user whether the command gets executed successfully or not by showcasing a warning message in case of failure. |
| .pfx | The .pfx extension is for Code Signing Certificate files in PKCS#12 format. All these files contain the information of public and private keys associated with that particular certificate. |
| .exe | The files with .exe extension contain a code or script that the system can run. Such files’ data get encrypted with the help of Code Signing Certificates. |
| .appx | The .appx extension represents a complete application package containing every essential file required to install and run an app on the end-user’s device. Such files are ready for deployment and installation across compatible systems. |
| Sign | The sign command initiates the digital signing of an executable file and application package. It leads the Code Signing Certificate to hash and encrypts the source code to protect it from unauthorized modification and breach. |
Can I use any digital solution, such as Sectigo, Certera, or Comodo Code Signing Certificate with SignTool?
Numerous software developers need clarification about whether their Code Signing Certificate will be compatible with SignTool or not. And the most accurate answer for such a query is YES; you can use any Code Signing Certificate with SignTool.
Whether you have Sectigo Code Signing Certificate, Certera Code Signing Certificate, or Comodo Code Signing Certificate or DigiCert Code Signing all get configured appropriately.
You only have to define the subject name of the certificate file, password (if any), and executable file in the command to digitally sign. Besides, if you want to timestamp your software, defining the URL to CA’s timestamp server is an additional requirement.
Hence, you can use any Code Signing Certificate with Microsoft SignTool.
The Purpose to Buy Code Signing Certificate for Executable Files
When you timestamp and sign an executable file, you get the following leverages:
- The system treats it as a legitimate file by analyzing a digital sign and publisher’s information with the software. As a result, users don’t see an Unknown Publisher Warning or anything similar on the screen.
- The code Signing Certificate first performs hashing and then encrypts the hashed file. It helps to strengthen source code protection and ensure data integrity.
- When you utilize an EV Code Signing Certificate, you get instant recognition as a trustworthy organization. And, when any end-user tries to install your software, the Windows Defender SmartScreen warning doesn’t appear.
- With the aid of timestamping, your software becomes a valid and legit application in the long run. The devices consider it a valid executable file; even the Code Signing Certificates gets expire.
- Digital Sign and Timestamp showcase that an authentic Certificate Authority backs your software. Therefore, your brand’s reputation gets enhanced, and people prefer it over other software.
Wrapping Up
Microsoft SignTool is the primary solution used by software publishers to sign their software, application package, and executable files.
It comes in handy with Windows SDK and Visual Studio. You only have to install the Code Signing Certificate and hardware token for signing. Then, you have to open the Command Prompt and run the command as mentioned above according to your requirements.
Furthermore, you can also verify whether your executable file gets signed or not. If you are a software developer, you must know about SignTool and its fundamental commands. It will help you solidify code security, optimize brand reputation and enhance user trust.
