What is Hashing?: Best Hashing Algorithms
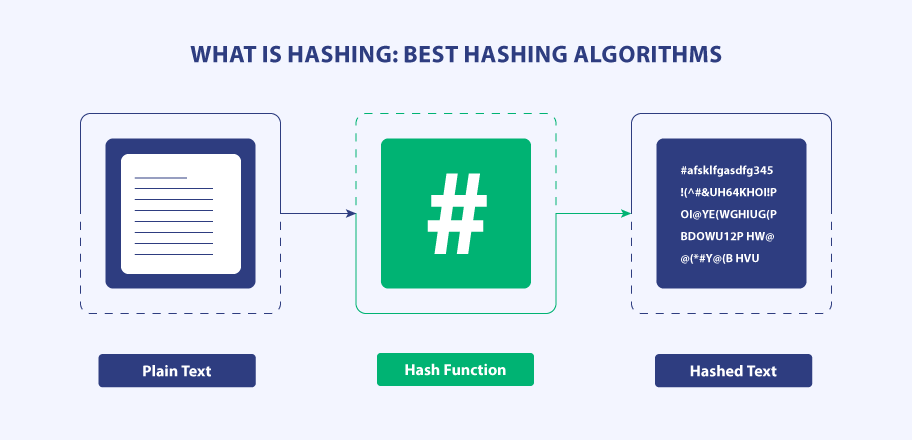
Hashing has become a ubiquitous part of internet security and one of the most secure encryption algorithms used more often than others. It is a mathematical function and a one-way program to encode data or messages that others can’t decode.
The best thing about hashing is that even if your server gets compromised, hashing will protect your data because it’ll remain unreadable. Furthermore, the data remains unaltered or can’t be modified once it’s hashed using the secure hashing algorithm.
Hashing is used for more than just password security to offer integrity checks, data validation, and others. Apart from these, there are so many applications of hashing, but, what does hashing mean and what are some of the best hashing algorithms?
What Does Hashing Mean?
Hashing is a cryptographic process to encrypt data using a mathematical function that is uniform, consistent, and one-way. The process involves encoding any given text or data into a cipher value, which is a fixed-length key to represent the original string of data.
The most popular usage of the hashing algorithm is the implementation of the hash tables that store key and value pairs and can be accessed through the index. Additionally, it’s widely used for user authentication and also to validate files, documents, and other data types.
The improper or incorrect use of hashing algorithms can lead to some serious data breaches. But not using it completely to safeguard your sensitive data would be an even bigger mistake.
The hashing function used can generate new values depending on the hashing algorithm used. This function is always one-way to prevent the converted hash back into the original value or key. Once data is hashed, it is virtually impossible to reverse the hash as it requires too much computational power.
Hashing is one of the three basic elements of cryptography that also includes encoding and encryption. An ideal hashing algorithm is easy to compute, irreversible, and produces unique output.
Where Is the Hashing Algorithm Used?
- Data Validation and Encryption
- Software Code Signing
- Password Verification
1. Data Validation and Encryption
The primary use of the hashing algorithm is to encrypt data messages and digital signatures. Also, it’s used for user data authentication for flawless access to the requester’s profile. The hash algorithm converts the digital messages into a hashed value, which is then sent to the receiver along with the signature.
2. Software Code Signing
Another use case of the hashing function is to make sure that your software file is genuine and not modified or contains a virus. For the same, a code signing certificate with a hash function is used to ensure the code integrity of the software or other executable files.
A digital signature of the publisher is attached with the software code to verify the source identity. You can check the hash algorithm on the download page with the one included in the software. If the hash values match, then the file is considered to be not tempered with or modified by malicious actors.
Doing so bars the software operating system to display “Unknown Publisher Security Warning” alerts when installing the software.
There are two different code signing certificates:
3. Password Verification
The hashing algorithm is also used for password verification and storage. Whenever someone registers on the online platform, their passwords are saved in only hash value instead of the plaintext password.
Thus, when users try to log in by entering their password, the system will hash the same & compare it with the one stored in their database. Now if these hash values match, then only the user can access their profile, making it the safest option.
Apart from that, hashing is also used for data retrieval, message digest, proof-of-work system, and many others. Hashing plays a key role in safeguarding the internet from malicious actors.
What Makes Hashing Algorithms Important?
Now that we know what hashing is and its applications, let’s get to know why hashing algorithms are important:
- Provides quick search functionality that is faster than other data retrieval methods, for example, arrays or lists.
- Hashing increases password security as the database doesn’t have to store the password in plaintext, only the hash value.
- Allows you to compare two pieces of data without opening them to know if they are the same or different.
- Hashing is a powerful ally for code and data integrity to ensure the originality of the certificate.
Some of the Best Hashing Algorithms
- SHA (Secure Hash Algorithm)
- Message Digest (MD)
- WHIRLPOOL
- RIPEMD
Let’s take a closer look at some of the best and most popular hashing algorithms:
1. SHA (Secure Hash Algorithm)
SHA has multiple different variants starting from SHA-0, SHA-1, SHA-256… and so on. SHA-0 was first introduced in 1993 but was compromised multiple times and thus went obsolete. The SHA-1 was a slightly improved version of its predecessor but it also went through a similar fate.
SHA-256 and SHA-384 are more secure versions of their predecessors and are used by companies with more seriousness about safeguarding their data. SHA-256 is 30% slower than the previous version while SHA-384 is much faster than the SHA-256 version as it is based on sponge construction.
2. Message Digest (MD)
The Message-Digest hash algorithm began with MD-2 in 1989, followed later by MD 4, MD 5, and MD 6 versions. However, any of the MD versions are not in use due to their consistent failure to satisfy security requirements.
For instance, MD 5 fails to find two distinct messages with the same hash value. Such catastrophic failures can easily be found in seconds even on ordinary computers. MD 6 is said to be not ready to reach the level of SHA-3 due to speed issues.
3. WHIRLPOOL
WHIRLPOOL is also another popular cryptographic hash function and has also been recommended by NESSIE and adopted by ISO and IEC. It is designed after the Square block cipher and is considered to be part of the block cipher functions.
This hash algorithm returns the 512-bit hash message digest and is based on the Advanced Encryption Standard (AES). The first version was called Whirlpool-0 while the revised version was called Whirlpool-T and the latest version is called Whirlpool.
4. RIPEMD
RIPE Message Digest is another cryptographic hash algorithm family which includes RIPEMD, RIPEMD-128, RIPEMD-160, RIPEMD-256, and RIPEMD-320. RIPEMD-160 is one of the most commonly used hash functions and is typically represented as 40-digit hexadecimal numbers.
The said RIPEMD-160 version behaves with the avalanche effect of the hash function. RIPEMD is based on MD 4 hash function and is used in Bitcoin and cryptocurrencies based on Bitcoin. This series of hash algorithms is less popular than the SHA-1 and SHA-2.
Recommended: MD5 vs SHA1 vs SHA2 vs SHA3: Choose Best
What are Some Traits of Strong Hash Algorithms?
Strong hash functions should include the following characteristics:
- It should be preimage resistance, meaning the value should be too complex and burdensome to reverse engineer to its original value.
- It should have an avalanche effect which refers to the randomness of the hash value, thus, a tiny change in the input will create a big change in the entire output.
- It should be collision resistance. A collision occurs when two inputs provide the same hash output. A collision resistance hash should generate unique hash values and impossible-to-find matches.
Conclusion
We hope that this article has provided you with helpful information on hashing and some of the popular hashing algorithms. Hashing helps ensure your important data and password remains protected and aren’t stolen by hackers.
It is also used for preventing file tempering by integrating the code signing certificate and storing the generated hash in the file data. Apart from that, hash algorithms have several other applications. They make the life of attackers and hackers difficult and play an important role in securing the digital world.
If you are using outdated algorithms such as MD 5 or SHA-1, make sure to update to the latest and newest version of the hashing algorithm to secure your data. That said, keep your data safe with a hashing algorithm and secure software with code signing certificates.
