How Does the Code Signing Process Work? – Understand the Code Signing Architecture

Today, one of the most common ways to get into a system is via malware. And the way in which the malware can reach a system is via software. Some of you must have noticed the unknown publisher warning on your PC while installing the software. If you haven’t, you are lucky, as it may be the last thing you do before deliberately impacting your PC in a bad way.
When it comes to these software warnings, the code signing architecture and code signing process comes into the frame.
Now, what is code signing? Well, the short answer to this question is signing the software code using a code signing certificate obtained from a legitimate CA.
In the modern-day security landscape, the rise of malware and fake software is swift. According to stats, viruses are commonly spread by .exe files, and these executable files are what software is. Companies do their best to ensure that their software is virus-free, and code signing is what helps them.
Let’s read ahead and drill down the concept of code signing and code signing architecture!
Why Is Code Signing Necessary?
Well, there are not one but many reasons that support the need for code signing. Here are some of the chief ones!
1. Reduce Security Warning:
Whenever a user installs software on their machine, a security warning can be a bad way to introduce yourself. If the user finds installing the software on their machine difficult, they may not try again and might never install it. To make sure that this does not happen, code signing is necessary. Code signing eliminates those irritating warnings and provides the users with a guarantee that the software is safe to use.
2. Shields Code Integrity:
The security warning is raised due to the mismatch of the hash function. For example, when software is signed, the code is hashed to keep encrypted, and if this hash does not match at the time of downloading, it is unsafe. With code signing, you can protect your code integrity using the mentioned hash function. The hash function is produced by combining the digital signature of the publisher.
3. Increases Product Scope:
As mobile devices and desktops use is on a larger scale, the scope of malware has skyrocketed. On top of all, the proliferation of devices has also made it easy for publishers to make more profit by increasing distribution.
As security is the number one concern of the users, code signing helps the publisher to fulfill almost every aspect. It ensures optimum security and helps build trust for the software among users.
These are some primary reasons supporting the necessity of code signing. Besides these, code signing also ensures faster time to market and boosts your reputation.
How Does Code Signing Work?
The process of code signing involves some steps that can be tough to catch up with. Here we have broken down the process in an easy-to-understand way!
Step 1. Purchasing the Certificate
The very first step in the working process of code signing is the purchase. You have to purchase the code signing certificate from a reputed CA. Certificate Authorities like Certera, DigiCert, Comodo and Sectigo supply code signing certificates.
Make sure you choose the right one based on your requirement. For example, you can go for a standard code signing certificate if you are an individual or an EV code signing certificate if you are a company.
| Buy Certificates | Price |
| OV Code Signing Certificate | $199.99/yr |
| EV Code Signing Certificate | $269.99/yr |
| Individual Code Signing Certificate | $199.99/yr |
Step 2. Certificate Authority Verifies You
This is the crucial step for you. It is not like you purchase the certificate, and it is yours. There is a proper verification process that the CA follows to ensure that it is you and that you are operating in a legitimate way. Based on the type of certificate, it takes time.
Step 3. Installing the Code Signing Certificate
Once you obtain the code signing certificate, you can install the certificate on the platform that you are using.
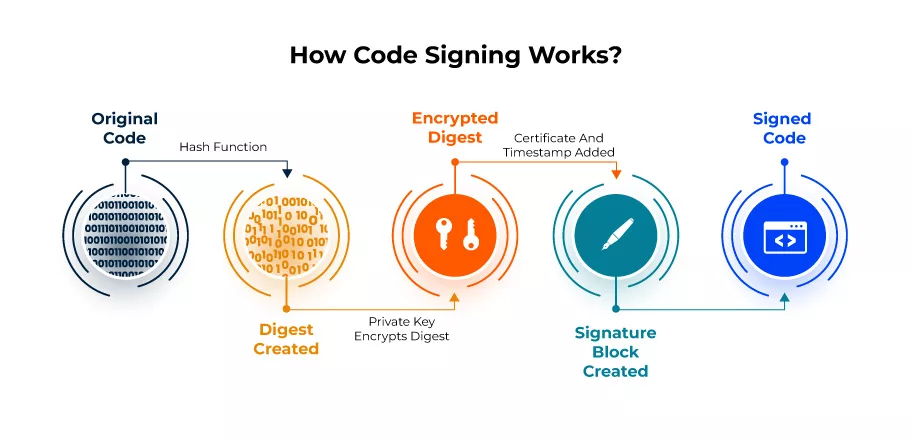
Step 4. Signing the Software Code
After successful installation, you can start signing the software. The signing process includes hashing the software code with a hash function that is included in the code signing certificate. The key motive of hashing the code is to prevent its alteration.
Step 5. Software Distribution
When your software is signed, it is ready to be distributed. When the user installs the software on their machine, the machine hashes back the code and displays the name of the developer. If the hashed-back code does not match, the code has been altered. Usually, it does not happens.
So, this is what happens behind the scenes when software is developed and installed on your computer. The key motive of code signing is to ensure software safety.
What Is the Architecture of Code Signing?
The architecture of code signing is not that tough to understand. Let’s take a look at all the critical elements of the code signing architecture!
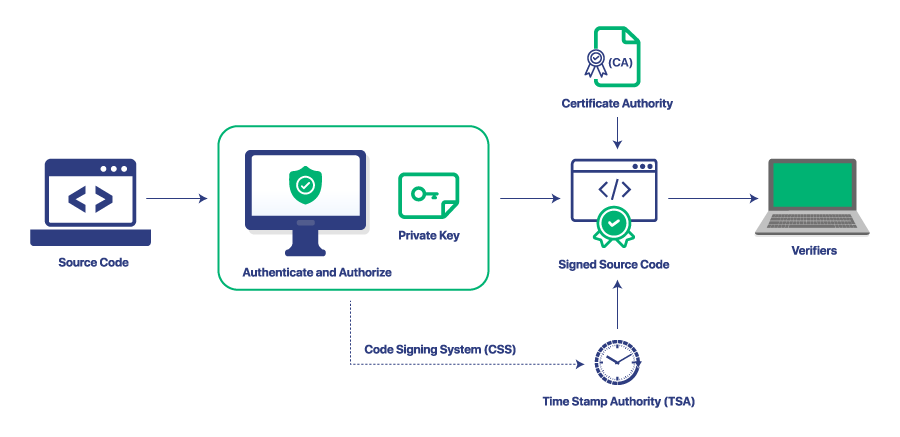
Code Signing System (CSS)
As the name suggests, the code signing system is the pivotal element of the code signing architecture. It is the place where the raw code is accepted and checked for legitimacy. It is done via the authorization and authentication process.
When the code is confirmed to be legitimate, it is signed using a digital certificate and a private key. The keys and certificates are stored in a secure location that is not vulnerable to any attack. Primarily, it is a hardware security module.
Certification Authorities (CA)
Now, the signing that takes place in the code signing system is backed by the certificate authority. Certificate authorities like Sectogp provide software signing certificates to software publishers to sign their software code.
However, as a code signing certificate ensures software safety and integrity, it is tough to acquire, especially if it is an EV code signing certificate. To get a code signing certificate, a software developer or an entity has to submit proof of their business. The CA carefully follows the vetting process to make sure that the firm is indeed legit. It checks the business name, location, phone number, and government records for authentication.
Once all of this is checked, the digital code signing certificate is issued to the publisher. Each CA has some mandatory requirements to follow before assigning a code signing certificate. These requirements are provided by the CA browser forum and CA security council.
Time Stamp Authority (TSA)
Though it is an optional choice, it can play a key role in keeping your software acceptable for a long time. Not only this, even if the certificate expires after some years, the timestamping can keep it alive as it is time-stamped at the time of approval.
The time stamping part of the architecture receives the code and signs it with its signature.
Along with this, the time stamping also stamps the time at which the code is signed. Again, it is optional but recommended.
Verifiers
Let’s move on to the last stage of the architecture. When the code is signed and timestamped, the software user tends to check it. If you are a developer, you must verify the digital signature before publishing.
Verifiers use trust anchors to check the digital signature. Now, what are trust anchors?
Trust anchors are public keys for root certificates stored in a root store. When the verifier receives a certificate, it is matched against the root store. Similarly, if it has a root certificate using the standard X.509 architecture, it is deemed legit. Browsers like Google Chrome and Mozilla Firefox also use this kind of root store.
So, that is all about what is a signing process and its architecture in absolute detail.
Are There Any Weaknesses in Code Signing?
Though code signing is extremely necessary and beneficial, some weaknesses may make your code vulnerable.
Improper Management of Keys
As private keys and digital certificates are involved in the code signing process, they need to be protected at all costs. If you don’t have a proper key management system, they may get hacked, and your software may lose its market forever. To ensure key security, hardware security modules are the best.
Hacking of Identification Information
The use of legitimate certificates can be done by hackers too. But, the one thing that is challenging for them is proving their identity. They might hack other firm information to sell malicious software. Therefore, when malicious software is backed by a legitimate certificate, the users may lose their data.
Deliberate Installation of Software
Here, there is no fault in code signing. If the user ignores the warning given by the system and deliberately installs the software, it will surely cause issues.
Conclusion
Code signing is the pivotal element of the public key infrastructure. It is the sole way for software developers to ensure that their users trust them and use their software. But, before making users trust you, you need to build trust in the eyes of CA to get a software signing certificate.
Once you have, the code signing process will not be difficult for you. Moreover, it will help you build a reputation and better revenue in the market.

