Code Signing Guide: Architecture, Types, and Threats

If you have opened this blog post, you are surely seeking an answer to what is Code Signing. Code Signing Certificates are digital certificates used to authenticate the identity and company of the software publisher; to confirm the integrity of the software.
What is PKI (Public Key Infrastructure)?
Public Key Infrastructure (PKI) technology is used to secure the digital distribution of software. PKI also safeguards other executable files by signing them with a digital signature.
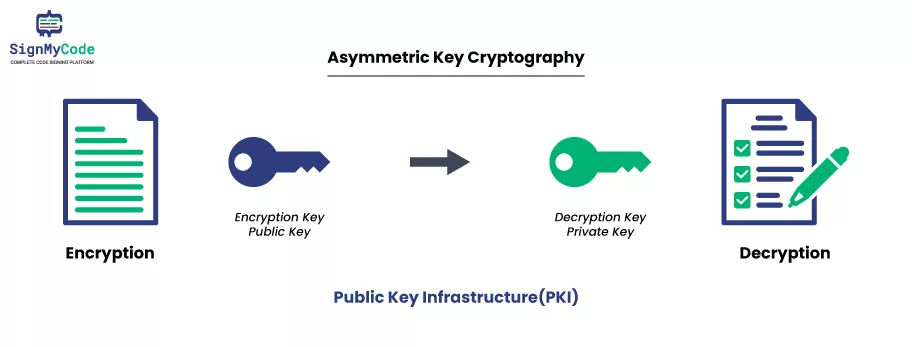
Code Signing Certificates are similar to SSL/TLS Certificates in terms of providing identity and trust to secure online transactions.
Digital Signing Certificates are used to protect software from malicious alterations and malware attacks. This process is done by verifying that the software is from a trusted source.
It also allows users to trust the downloaded applications by preventing errors or warnings during installation. It helps protect against tampering with the code, ensuring that the program you receive is the same program the software author created.
We know that Code Signing Certificates are crucial in securing web and mobile applications before they are publicly released. They allow software developers and publishers to provide their users with a trusted identity.
So, to keep your product’s integrity and protect against malicious alterations and malware attacks, let us read further in the guide below.
How does Code Signing Work to Prevent Cybercrime?
Now that we know what Code Signing is, let us know how Code Signing work.
- A Code Signing Certificate is an essential component for software and content developers. You are allowed to demonstrate the authenticity of their code and content.
- You must generate a private and public key pair to obtain a Code Signing Certificate. The public key is provided to a Certificate Authority (CA) with all the necessary documents.
- These files further authenticate and verify the identity of the organization or individual applying for the certificate.
- After your authentication is successful, a validated Digital Certificate is issued.
- This code signing certificate will include your organization’s full name and a public key.
- Ensure to keep the private key confidential. Then, you can use the public key to sign your software for a code or content within its validity period.
- Using Digital Signing for application and software security can help users to trust the code they are downloading and running, avoiding malicious text or symbols.
- Eventually, this will enable your users or audiences to download files without error messages or insecure pop-ups.
You can experience the below process at the deployment stage:
- Initially, software, script, or code, with other functioning documents, is signed using a digital certificate by using a publisher or a legitimate software developer.
- With an irreversible technique of cryptography, you get to use a mathematical hash function is used.
- Then, construct a hash value or else a digest that cannot be recreated after adding the code sign to the file.
- It becomes public as soon as the content is published on a website or by using a mobile network.
- Lastly, you can download the program (software or application) as a user. Then your system will decrypt the signature using a public key.
What is a Root Certificate?
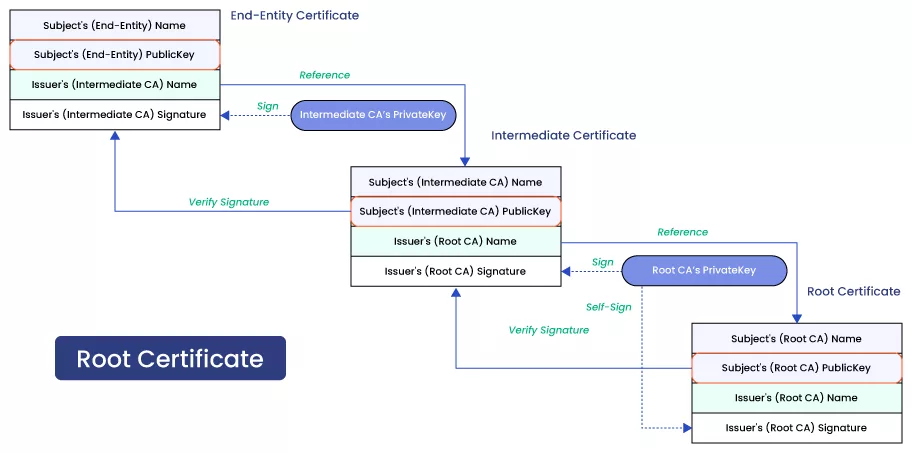
A Root Certificate is basically a public key certificate issued by a relied authority, such as a Certificate Authority (CA), used to identify a root certificate authority. It validates the authenticity of the software or executable downloaded by users.
The globally known CA’s signature embedded in the Root Certificate assures users that the software or executable is safe to download.
Root Certificates work like a family tree because they link the identity of the digital certificate used to the identity of the certificate authority that issued it.
Recommended: What is a Certificate Authority & Key Role of Certificate Authority
Without a valid Root Certificate, verifying the identity of the issuer and the certificate itself could be impossible. Root Certificates play an integral function in Code Signing Certificates, as they provide users an extra layer of protection and faith.
They can test the ‘chain of trust’ to track the original authority used for code signing.
What are the Types of Code Signing Certificates?
There are diverse types of Code Signing certificates that you must know about. We have briefed the categories below to save you time. Also, find the best options for each type of code signing certificate below.
When protecting your online software, code signing certificates are a must. They are available in different types, each with its own advantages and use cases.
The three main types of code signing certificates are:
- Organization Validation (OV) or Standard Certificates
- Individual (IV) Code Signing Certificates
- Extended Validation (EV) Code Signing Certificates
Organization Validation Code Signing
It is also known as the Standard Certificate of digital signing for application and software security. Organization Validation Certificates are aimed at organizations and companies to prove the software publisher’s identity and protect users from malware. These are the most commonly requested type of code-signing certificates.
| Certificates | Price | Link |
| Certera Code Signing | $199.99/yr | Add to Cart |
| Sectigo OV Code Signing | $210.99/yr | Add to Cart |
| Comodo OV Code Signing | $210.99/yr | Add to Cart |
| DigiCert OV Code Signing | $369.99/yr | Add to Cart |
Individual (IV) Code Signing Certificates
IV Code Signing Certs are aimed at individual users and software publishers and focus on protecting users from malicious software.
These certificates provide basic validation and verification and are suitable for users who don’t need to prove the identity of their company or organization.
| Certificates | Price | Link |
| Comodo Individual Code Signing | $210.99/yr | Add to Cart |
| Sectigo Individual Code Signing | $210.99/yr | Add to Cart |
Extended Validation (EV) Code Signing Certificates
This certificate provides additional security and are the most secure type. They include a more thorough authentication process and are commonly used by larger companies and organizations. These certificates ensure users that the software is trusted and secure.
| Certificates | Price | Link |
| Certera EV Code Signing | $269.99/yr | Add to Cart |
| Sectigo EV Code Signing | $274.99/yr | Add to Cart |
| Comodo EV Code Signing | $274.99/yr | Add to Cart |
| DigiCert EV Code Signing | $519.99/yr | Add to Cart |
In conclusion, code signing certificates are vital to keeping your software secure. The above-mentioned three main types serve different purposes depending on the user’s needs.
What are the Possible Vulnerabilities of Code Signing Certificates?
Till now, we know how important Code signing is as a security measure. You can ensure the authenticity of software and application downloads with digital certificates.
When code signing is in place, organizations can guarantee that the software or application installed is untampered and comes from a trusted source.
Despite this, code signing can be powerless against certain dangers, such as key theft or loss, insufficient certificate authority, and insecure cryptographic governance measures.
Theft or Loss of Private Signing Keys:
This can present serious risks to a firm’s security. Cybercriminals accessing the code signing keys might get a masquerade malware attack or have malicious code instead of the authentic code or software. This can lead to a variety of security risks and data breaches.
Threat to the Certificate Authority (CA):
Another serious threat to code signing is a direct attack launched on the certificate authority (CA) issuing code signing certificates.
If a malicious actor is successful, this can severely vandalize the firm using the certificates. Furthermore, if an attacker compromises the CA, an organization’s digital identity can be stolen, and malicious code can be distributed as if it were authentic.
Insecure Cryptographic Algorithms:
Finally, weak and insecure cryptographic algorithms for digital signing can create threats. Organizations must know the security measures in place and ensure their cryptography governance controls are secure.
Overall, organizations must be aware of several potential threats to code signing – theft or loss of private signing keys, compromised certificate authority, and use of insecure cryptography governance controls.
Organizations should ensure strong security measures regarding code signings, such as encryption and authentication protocols, to mitigate these risks.
How to Buy a Code Signing Certificate?
You can buy a code signing certificate easily with these simple steps below-
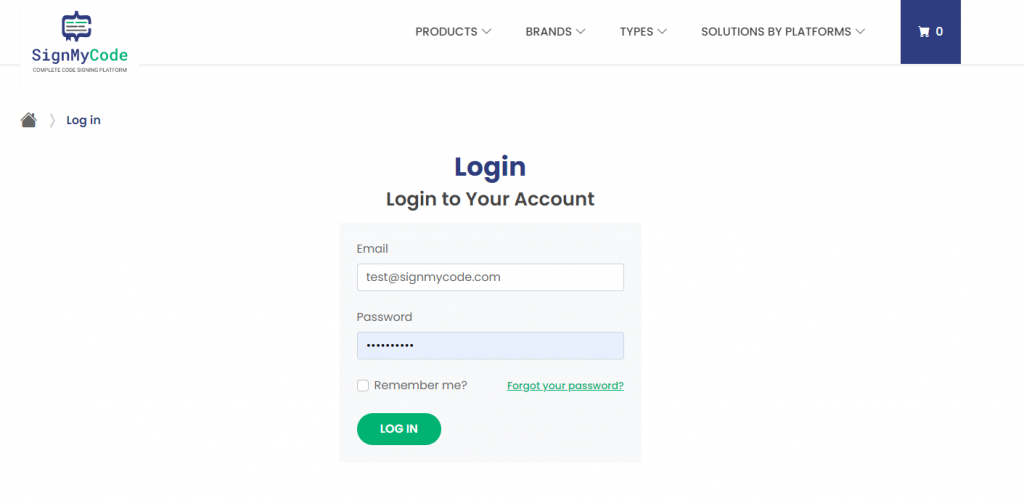
Step 1:
To log in, visit here and provide the following details in the prompted fields!
Step 2:
After typing the required details, you can click “Remember me” to save your login credentials to open your account on your next visit automatically.
Important note: If you do not remember the password with your registered email ID, click the “Forgot your password” option to begin retrieving your password.
Step 3:
Once you logged in successfully, choose the relevant products from the catalog.
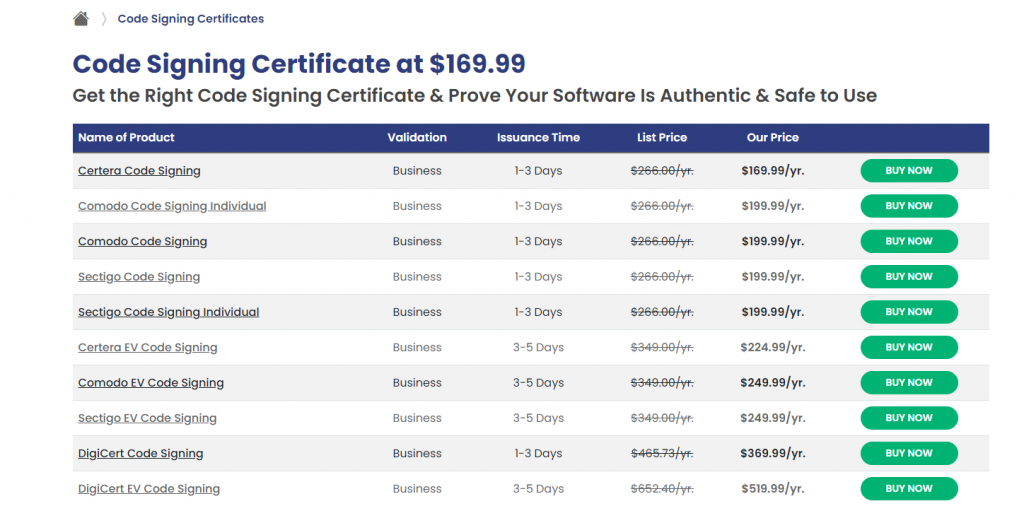
Step 4:
Click on Buy Now or Renew Now button and you will redirect to the checkout page! Fill all the required details including email, company name, address, first name, last name, phone number and payment details.

Step 5:
Once you done, you will redirect to the Thank you page and will get enrollment process link!
Wrapping up
You can always Purchase Code Signing Certificate to authenticate software codes, programs, and other digital content. They can ensure the code and software come from a verified source, thus building trust and security.
We hope you found this article descriptive, informative, and useful in understanding digital certificates and code signing.

