What is Code Signing SDLC?
Today, an intricate web of tools, programs, and individuals collaborates to bring applications to life. This interconnected network, the software supply chain, encompasses the various entities and processes that shape the software development lifecycle (SDLC), including developers, dependencies, network interfaces, and DevOps practices.
Given the diverse nature of these components, ensuring the security of each element becomes paramount.
You must safeguard the authenticity of applications throughout their journey in the software supply chain. This is where the concept of code signing emerges as a critical technique.
By code signing, developers can ensure that their final published software originates from the intended source and remains untampered by unauthorized parties.
This article delves into the code signing SDLC, shedding light on its inner workings and highlighting its vital role in reinforcing application security.
Furthermore, it explores best practices when implementing code signing in your software, empowering developers to establish robust security protocols within their supply chain. Let us begin quickly!
Code signing in the SDLC: an Essential Security Measure
A code signing certificate is crucial in ensuring the authenticity and security of applications, scripts, drivers, and other software components. By utilizing digital signatures, code signing verifies the original authors of these software elements, thereby establishing trust and integrity throughout the development process.
Recommended: What is a Code Signing Certificate? [Detailed Guide]
The fundamental principle behind code signing is signing code by its author whenever changes are made. This practice ensures that all actions taken on the code are authorized and traceable, bolstering the overall security of the software.
Code signing holds immense value as it confirms that all modifications made to the code are legitimate and appropriately documented. This verification process gives users confidence that the applications they receive are free from vulnerabilities or potential security risks.
Moreover, digital signatures prove to be particularly beneficial in team environments. When exchanging source code throughout the software development lifecycle (SDLC), code signing can be employed to achieve double authentication.
This strengthens security, is a preventive measure against attacks, and helps mitigate namespace conflicts.
Ensuring Security in Your Software Development Life Cycle (SDLC)
Engineering teams continuously develop, build, and deliver software in the current scenario of cloud-based distributed software. Manual security checks become challenging with continuous integration and continuous delivery (CI/CD) pipelines, as no specific stopping points exist.
Conducting a comprehensive security assessment after the entire build is complete can be time-consuming, resource-intensive, and akin to searching for a needle in a haystack.
Furthermore, even if vulnerabilities are identified, the need for code provenance and nonrepudiation poses significant challenges. Many security organizations, particularly those within high-growth software companies, are keen on safeguarding their customers by validating the build’s integrity and ensuring the absence of malicious code.
The surge in software supply chain attacks, exemplified by incidents like SolarWinds and Kaseya, underscores the ease with which malware can be injected into source code.
Recommended: Code Signing Security: Publishers Getting More Aware After GitHub’s Certificate Breach
Git repositories have become prime targets for attackers due to their vast amount of critical data, making them an efficient means of compromising both companies and their customers.
Attackers can exploit vulnerabilities in Git repositories, injecting malware packages that are unwittingly distributed to all customers using the software.
What is a Direct Threat to the Organizations?
One of the primary challenges organizations face in defending against these supply chain attacks at the developer level is the prevalence of personal Git accounts.
Since developers often create these accounts individually, controlling authentication to repositories and establishing a connection between these usernames and corporate identities becomes challenging. Determining whether developers can access the systems into which they check the source code poses a significant security concern.
Recommended: Roadmap to Secure Code Signing to Safeguard the Digital World
Organizations must implement robust security measures throughout the SDLC to mitigate these risks. It includes implementing secure authentication protocols, monitoring and controlling access to repositories, and enforcing policies that tie developer identities to corporate identities.
By addressing these challenges head-on, organizations can bolster their security posture and minimize the potential impact of supply chain attacks, ensuring the trust and safety of their software and customers.
Understanding the Secure Journey of the Code Signing Process
The code signing process typically consists of three key steps: Generating a public-private keypair, hashing, and description and verification.
Recommended: Code Signing Architecture: How it Works?
A unique public-private keypair is created, with the code’s author securely holding the private key. Then, the code is hashed, creating a fingerprint that serves as a digital content summary.
Finally, the code is described and verified using the digital signature, generated using the private key, and can be validated using the corresponding public key.
By adhering to this three-step code-signing process, developers can establish a robust security framework within their software supply chain. This framework ensures the code’s authenticity, integrity, and trustworthiness throughout its lifecycle, providing users with the peace of mind that they interact with secure and reliable applications.
Organizations and developers can strengthen the overall security of their applications by implementing code signing to foster among users.
Recommended: Importance of EV Code Signing Certificate for Apps and Software Security
Get a New Public-Private Key Pair
- The code signing process commences by generating a unique public-private key pair.
- The public key, representing your identity and your organization’s, is then submitted to a trusted certificate authority (CA) for verification.
- Once the CA successfully verifies these identities, it responds by providing a digitally signed code signing certificate and the corresponding public key.
Hashing for Security
- Upon receiving the code signing certificate and public key, the code undergoes hashing.
- Hashing involves using a one-way cryptographic function that irreversibly transforms the code into a unique set of values.
- The resulting output, the digest, is then encrypted by the private key.
- The encryption ensures that the code remains protected against external tampering.
- Subsequently, the hash function, its digest, and the code signing certificate are combined and packaged into a signature block, which is then delivered to the end consumer.
Decryption and Verification
- When users download the software, their computer initiates the code signing certificate verification process to establish its authenticity.
- Once verified, the public key from the previously generated public-private key pair decrypt the digest within the bundled signature block.
- Simultaneously, the hash function processes the software code, generating an output digest.
- The decrypted digest is then compared with the computed digest from the code obtained through the hash function.
- If the two digests match, it confirms that the software remains unaltered and safe for installation.
IaC Latest Security Challenges and Solutions in DevOps SDLC
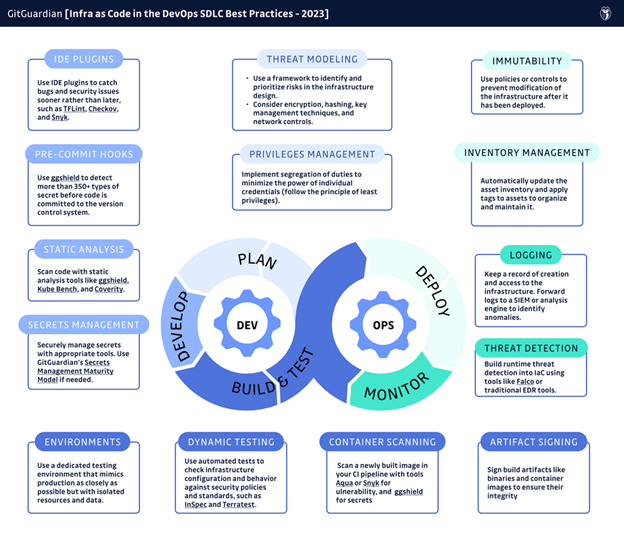
Incorporating Infrastructure as Code (IaC) in the DevOps Software Development Lifecycle (SDLC) introduces security challenges. Let’s explore these challenges and discuss potential solutions to ensure robust security throughout the IaC implementation.
Planning Stage:
Defining infrastructure requirements, designing, and identifying potential threats and vulnerabilities is crucial during the planning stage. To secure your IaC, two key measures should be taken: threat modeling and establishing privileges.
Threat Modeling:
Utilize established frameworks like STRIDE or DREAD to perform threat modeling. These frameworks aid in identifying and prioritizing critical risks associated with the infrastructure design.
Microsoft’s Threat Modeling Tool or OWASP Threat Dragon can assist. Consider implementing encryption, hashing, and robust key management techniques to safeguard sensitive data and credentials during transit and at rest.
Additionally, develop strategies to handle untrusted input effectively. Implementing network controls like a Web Application Firewall (WAF) can further enhance application security.
Establishing Privileges:
Follow the principle of least privilege, granting minimum permissions and access levels required for each resource and account. Implement segregation of duties for user accounts to separate responsibilities among team members.
Minimizing the power of individual credentials significantly reduces the potential damage from a compromised account or credential.
Development Stage:
The development or coding stage involves writing and updating the code or scripts that define the infrastructure. Adhering to security best practices during this stage is crucial. Here are some key recommendations:
Security-Based IDE Plugins:
Integrate security-focused IDE plugins into your development environment. These plugins provide real-time feedback and help identify vulnerabilities in your IaC code as you write it.
Examples include TFLint for TerraForm linting with security best-practice rules, Checkov for misconfiguration scanning across different IaC types, and Snyk, which offers an IDE plugin for code, container, and IaC scanning.
Recommended: Top 11 API Security Best Practices to Prevent Security Threats
Pre-Commit Hooks:
Leverage pre-commit hooks to automate the execution of static code analysis tools before committing code to the version control system.
Using pre-commit hooks, you can catch security issues, such as exposed secrets, before they become part of the repository’s git history. This proactive approach reduces the need for extensive cleanup work later on.
The above comprehensive approaches confirm potential vulnerabilities are identified and addressed early in the SDLC, reducing the risk of security incidents and maintaining the integrity and confidentiality of the infrastructure.
The Significance of Strengthening Application Security
In the cutting-edge software era, practicing robust security measures is an ongoing responsibility throughout the SDLC. Implementing code signing is pivotal in hardening application security, effectively reducing the attack surface and minimizing the likelihood of security breaches.
A vital aspect of the SDLC involves leveraging dependencies to optimize the software’s functionality. However, it is essential to recognize that these dependencies often rely on additional dependencies, thereby expanding the potential avenues through which vulnerabilities could arise within your SDLC.
To mitigate the risk of introducing malware into your source code, it is crucial to download third-party software and dependencies exclusively from trusted vendors.
Maintaining this level of caution ensures your code signing practices are effective. More than simple misconfigurations and dependency confusion can undermine your code signing efforts. Exercising diligence and discretion when integrating dependencies is of paramount importance.
Furthermore, attackers may exploit a technique known as typosquatting, specifically targeting internet users who inadvertently enter a misspelled or incorrect URL into their web browsers. These malicious websites can pose significant threats by downloading malware onto users’ computer systems or gaining unauthorized access to sensitive information.
Trusted Code Signing Certificates for App and Software Security – Starting at Just $199.99/yr Buy Now
How to Ensure Intensified Security?
To counter such risks effectively, it is essential to cultivate a multi-layered security approach. This includes implementing robust code signing practices, regularly updating software and dependencies to address vulnerabilities, and educating users about the potential dangers of typosquatting and the importance of verifying website URLs before accessing them.
Recommended: Must Know Software Development Best Practices For Every Developer
By prioritizing the hardening of application security and incorporating vigilant practices such as code signing, organizations can fortify their defenses against potential threats.
This proactive approach bolsters the reliability and trustworthiness of the software developed within the SDLC, safeguarding sensitive data and enhancing user confidence.
Incorporating Code Signing in Software Development Life Cycle (SDLC)
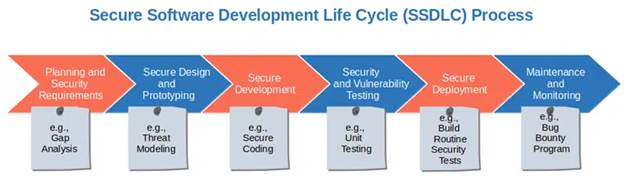
According to a recent global study by Venafi, a staggering 85% of CIOs acknowledge that developers and software engineers often compromise security for faster software releases.
However, rushing through the development process can lead to avoidable mistakes. To prevent this, consider the following practices:
Code Signing throughout the Entire SDLC:
Implement code signing early and consistently at every stage of the software development life cycle (SDLC). While this may pose challenges, transitioning from a traditional SDLC to a more secure SDLC ensures that security is integrated at each step.
Recommended: Secure SDLC Approach For Preventing Cyber-Attacks
Utilize Different Types of Signing Certificates:
To minimize potential damage if a code signing certificate is compromised, encourage your developers to use self-signed certificates during development.
Recommended: Self-Signed vs. Publicly Trusted CA Code Signing Certificates: What to Choose?
Once ready for production, replace these self-signed certificates with publicly trusted ones. It is crucial to note that using self-signed certificates in a production environment is strongly discouraged due to security risks.
With code signing practices in your SDLC, you can mitigate security vulnerabilities and safeguard your software’s integrity. Remember, prioritizing security throughout the development process is essential for ensuring the trustworthiness and reliability of your applications.
Its a Wrap
In conclusion, the significance of hardening application security cannot be overstated. By diligently implementing code signing practices and exercising caution when integrating dependencies, organizations can significantly mitigate the risks of malware, vulnerabilities, and security breaches.
By staying vigilant and proactive, we can ensure the integrity and security of our software applications, fostering a safe and trustworthy digital environment for all users.

